Since it was acquired by Facebook, Instagram has become one of the five most popular social media platforms in the world, accumulating some 500 million active users a day and with more than 1,000 images published every few seconds.
Being so popular, it’s normal for millions of users on the platform to carelessly expose all sorts of sensitive details, including location details, email addresses, personal data, and more, so Instagram can prove to be a great source of information collection.
Today, specialists from the cyber security course of the International Institute of Cyber Security (IICS) will show us how to use Instaloader and Osintgram, a pair of utilities for the analysis of Instagram profiles only by entering a person’s username.
Osintgram
To install it, download from GitHub (https://github.com/Datalux/Osintgram) and install the dependencies:
git clone https://github.com/Datalux/Osintgram.git
cd Osintgram
pip install -r requirements.txt
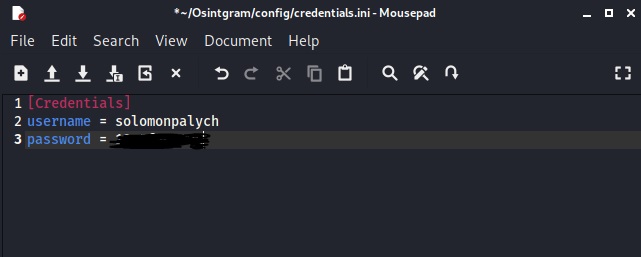
Before running the utility, you need to enter your account information in the credentials.ini file, which is located in the configuration directory. Enter your account name and password and save your details.
Now you can go directly to use Osintgram. Before proceeding, the experts of the cyber security course recommend entering the help menu:
python3 main.py –h
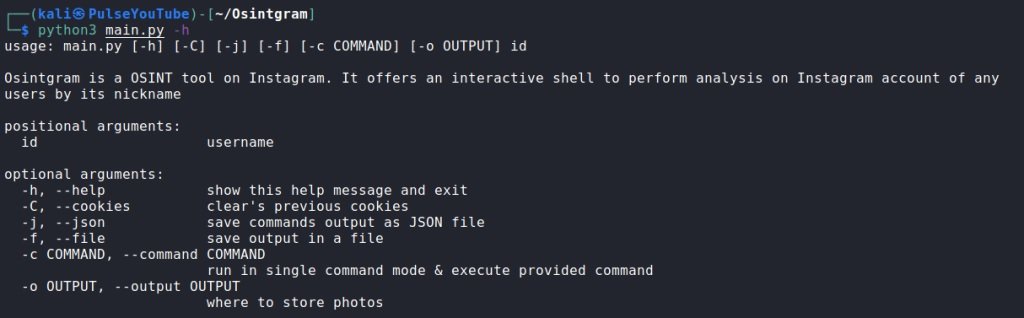
usage: main.py [-h] [-C] [-j] [-f] [-c COMMAND] [-o OUTPUT] id
Osintgram is Instagram's OSINT tool. It offers an interactive shell to perform analysis of any user's Instagram account by their nickname.
required arguments:
id username
optional arguments:
-h, --help show this message and exit
-C, --cookies clear previous cookies
-j, --json save result to JSON file
-f, --file save result to file
-c COMMAND, --command COMMAND
run in single command mode and execute the provided command
-o OUTPUT, --output OUTPUT
where to store photos
As you can guess, we only need to enter the name of the user of interest. After that, the utility will log in with the account we specified in the settings and determine the target.
python3 main.py
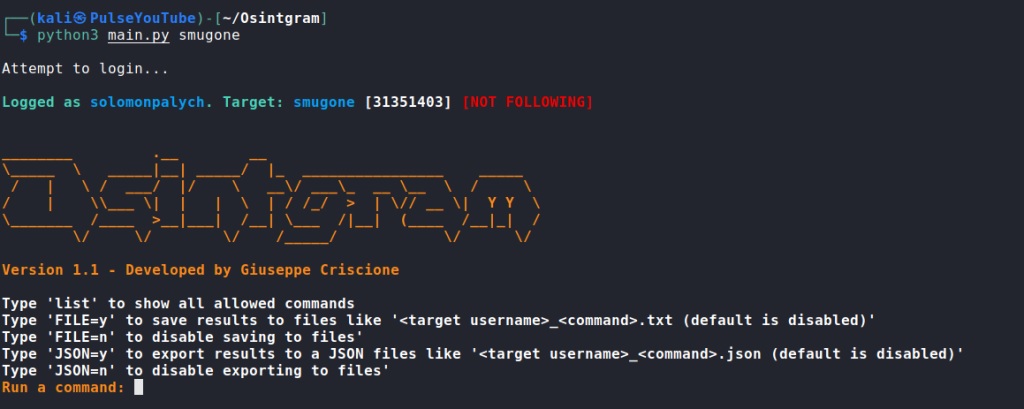
After a successful login, we see a list of commands to save the results and an invitation to enter. To view the commands for profile analysis, enter the list command:
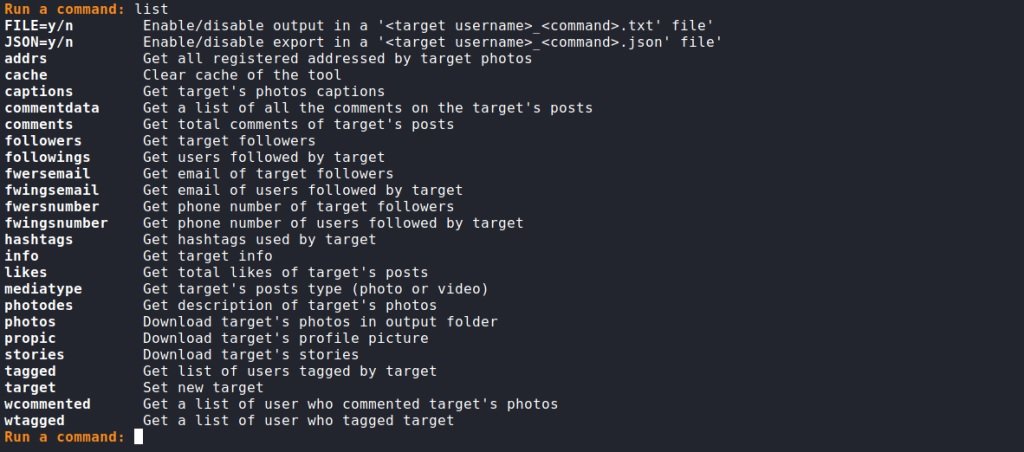
FILE=y/n Enable/disable output to file '<target username>_<command>.txt'
JSON=y/n Enable/disable export to file '<target username>_<command>.json'
addrs Get all addresses registered from target photos
cache Clear tool cache
captions Get captions for target photos
commentdata Get a list of all comments on the target's posts
comments Get all comments on the target's posts
followers Get the target's followers
followings Get the users the target is following
fwersemail Get target subscribers email
fwingsemail Receive email of users the target is following
fwersnumber Get the phone number of the target's subscribers
fwingsnumber Get the phone number of the users that the target is following
hashtags Get the hashtags used by the target
info Get information about the target
likes Get the number of likes for the target's posts
mediatype Get target post type (photo or video)
photodes Get description of target photos
photos Upload target photos to folder
propic Download target profile picture
stories Download story goals
tagged Get a list of users tagged by the target
target Set a new target
wcommented Get a list of users who have commented on the target's photos
wtagged Get a list of users who have tagged a target
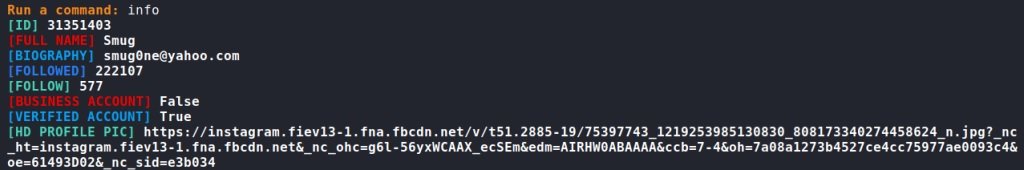
As we can see, Osintgram has very attractive resources. Let’s start by looking at general information about our goal by entering the info command:
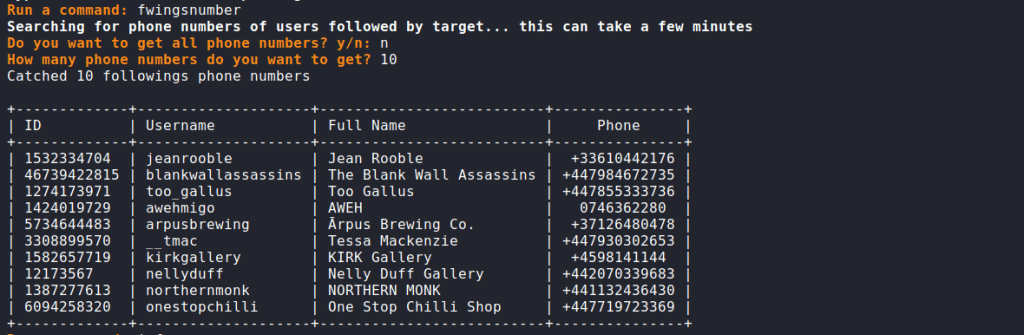
Next, let’s try to get the phones linked to the accounts that follow the target account. In the example shown below, the cybersecurity course experts specified to get a list of only 12 phone numbers:
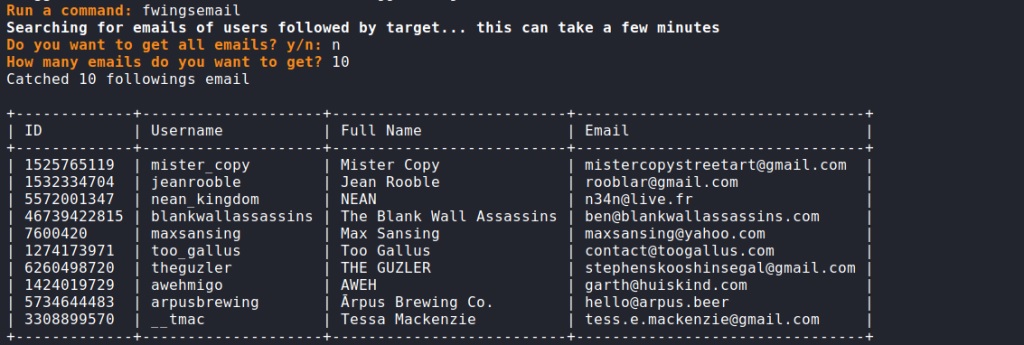
As we can see, we got a very specific result. Let’s do the same but with emails. Enter the flysemail command:
The other commands work in exactly the same way. It depends on the user’s goals how, when and in what way to apply them.
The experts of the cyber security course mention that the results can be saved in a txt file. To do this, before executing the commands, you need to enter FILE=y; you can also store the results in a json file by entering the JSON=y command.
Instaloader
According to the experts of the cyber security course, this tool allows you to download photos and videos from the target Instagram profile, as well as getting metadata and more related information. Its main feature is that there is a rather convenient opportunity to get detailed information about active profiles.
On Kali Linux and similar distributions, Instaloader can be installed with the following command:
pip3 install instaloader
Or you can download the tool from GitHub:
https://github.com/instaloader/instaloader
One of the main advantages of this utility is that the basic functionality can be used without logging into your account. If you need to download tags, geolocation, stories, and follower lists, you’ll need to specify your account username and password for authorization.
In the basic use case, simply specify the name of the desired profile and the download will begin.
instaloader smugone
With this option, you will download all the images and videos on the target profile, in addition to downloading all the descriptions with tags in text files. This feature also allows you to create json files for all available metadata, including profiles that have commented on the posts of the target profile.
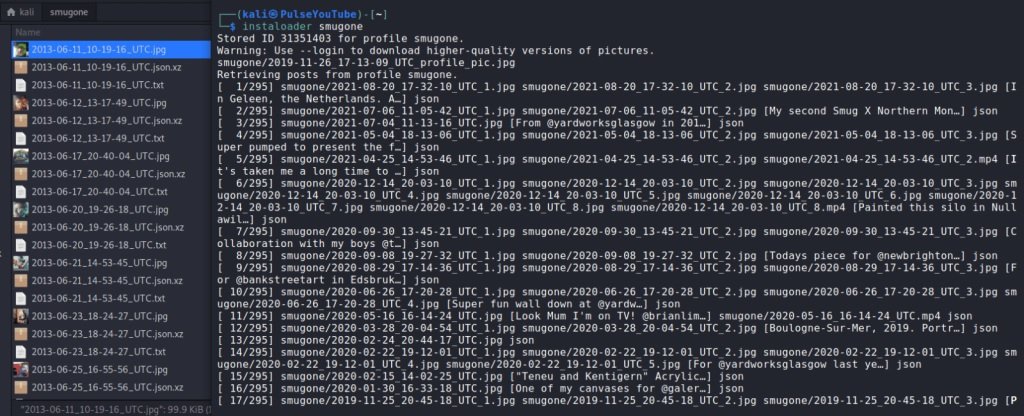
Subsequently, a directory with the name of the scanned profile will be created in the home folder to store the downloaded information, in addition to a text file will be created to register the user’s ID and a json file with the available user parameter identifiers.
If we need to update the downloaded data, we simply add the -F parameter to the original command and execute it. Instaloader will compare what we have and what is now in the profile to know what information needs to be updated.
Cyber security course experts also recommend adding the –help parameter to add more features:
instaloader smugone --no-posts --no-pictures -V -G -l solomonpalych -p 'password'
In this command, we set the target: the Instagram profile smugone: the -no-posts parameter indicates that no posts should be downloaded; the -no-pictures parameter indicates do not download images, the -V parameter indicates the download of videos, and the -G parameter indicates the download of geolocation tags. After that, through the -l parameter, the name of our profile is specified, and then -p specifies the password of our profile so that Instaloader could log in.
These are quite useful tools, since they allow you to fully exploit a source of public information such as Instagram for data collection tasks. Still, you should remember that this article was written for informational purposes only and does not represent a call to action; IICS is not responsible for the misuse that may occur to the information contained herein.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
