Determining the location of a device is one of the most complex hacking tasks, although there are several tools that can incredibly simplify this process, reducing everything to a matter of seconds.
This time, the experts in ethical hacking of the International Institute of Cyber Security (IICS) will show us how to obtain the location of a smartphone using only the phone number of the user we want to track. To do this, we will use Firefly, a mobile hacking tool that requires a monthly subscription, although we can also access some of its features using the free trial.
Before proceeding, we remind you that this article was prepared for informational purposes only and should not be taken as a call to action. IICS is not responsible for the misuse that may occur to the information contained herein.
Installation
As you can already imagine, the first step is to install the tool:
git clone https://github.com/M3-SEC/firefly
Next, go to the firefly cd directory and copy the firefly file from there to the internal folder (or wherever it is convenient for you so that you can quickly find the file in the browser, ethical hacking experts recommend).
mv firefly.py / storage / emulated / 0 /
The next step is to go to the site numverify.com and register to get the API through which the program will work.
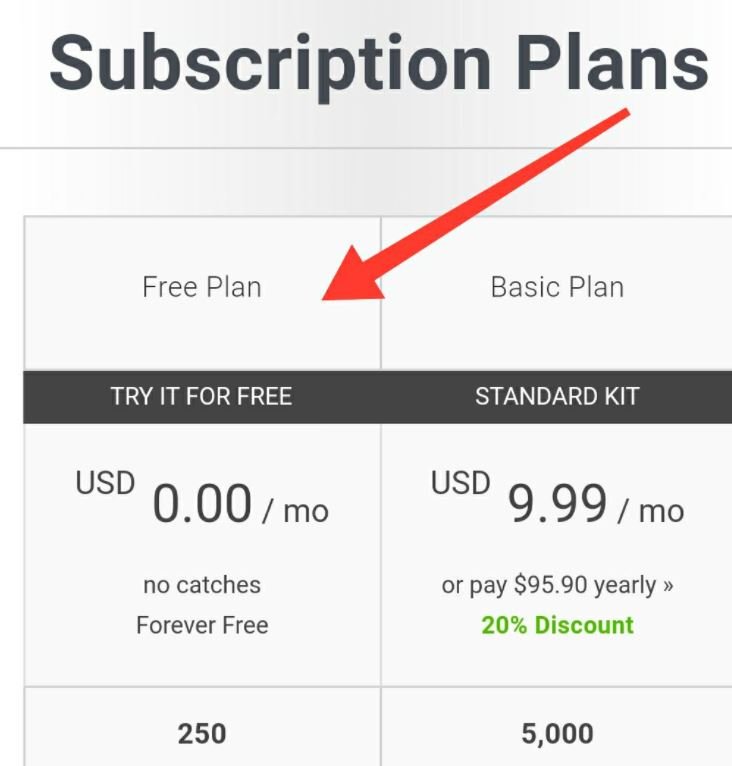
- We must choose a free subscription and enter any information and mail requested, preferably that is false information. Once you have completed the registration procedure, you will be able to see your API.
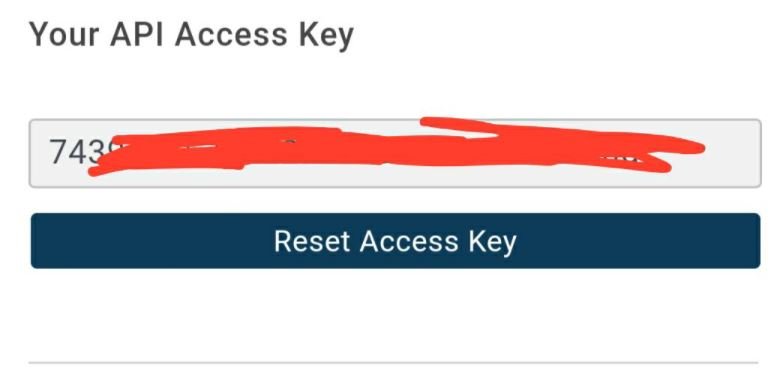
- Copy the API and go to the firefly file, which was previously transferred to the device’s internal memory. Open the file and you will see this line.
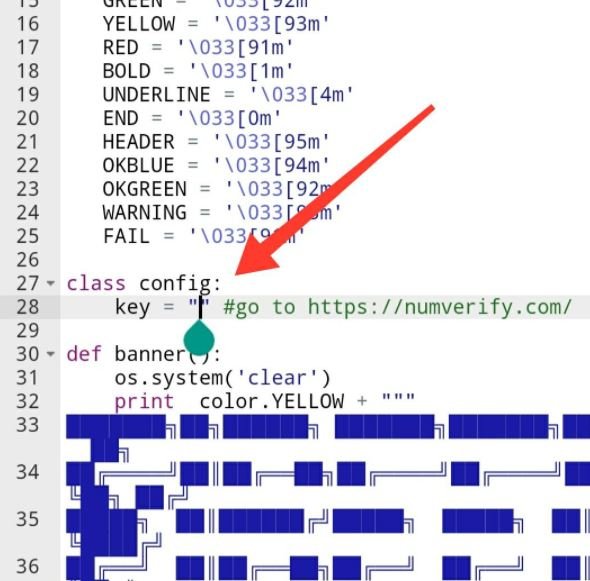
- We will have to insert our API in the fragment where the cursor appears. The result should be seen as shown below:
Now choose the Save and Exit options.
Now go to Thermux and transfer your file back to the mv /storage/emulated/0/firefly.py $ HOME/firefly, directory ethical hacking experts mention.
python2 firefly.py + phone number
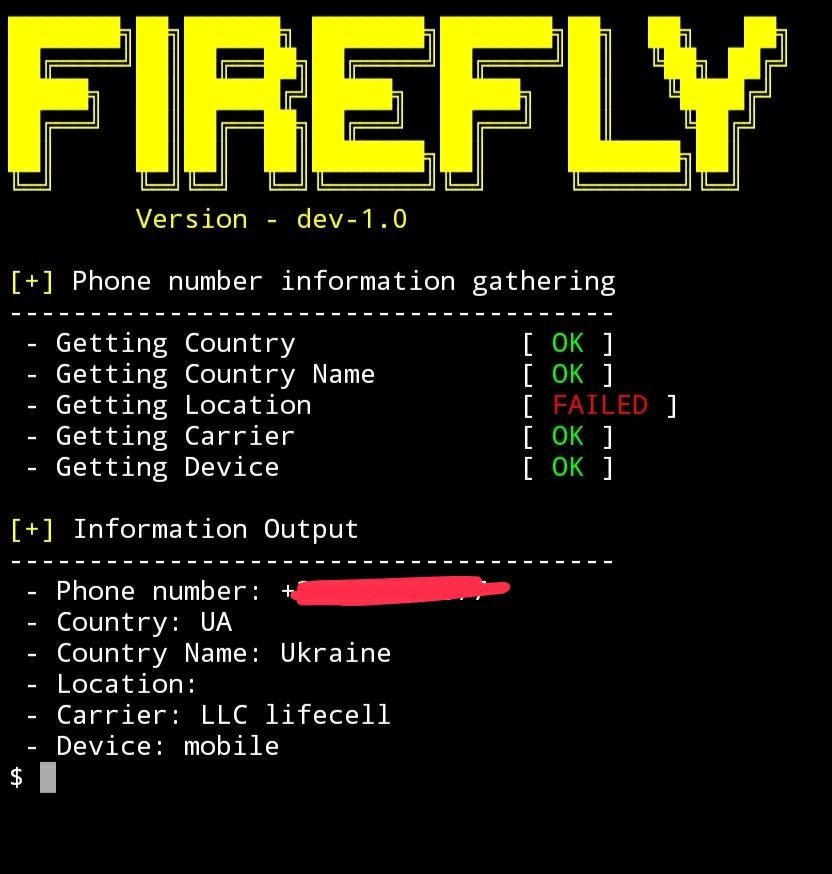
As you can see, everything went well in this example, with the exception that no information about the target’s city is displayed, probably because the phone operator does not provide access to this information.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
