The security mechanisms on routers are really weak, so it is not uncommon for threat actors to exploit vulnerabilities on these devices for malicious purposes.
Constant attacks on this technology require even less experienced users to know some router security methods, so vulnerability assessment experts from the International Institute of Cyber Security (IICS) will show you the best ways to check the security of your WiFi network, as well as show you some free and easy-to-use tools.
In their latest router security report, Check Point experts mentioned that there are at least 12 million DSL routers that can be hacked to extract their default access keys, including those of the most sophisticated models. These practices are closely related to CWMP and other protocols used by manufacturers to configure the configurations of these devices and connect them to services through an automatic configuration server (ACS).
Vulnerability assessment specialists also found that vendors do not encrypt connections between these servers and client computers, so a threat actor can easily deploy a Man-in-The-Middle (MiTM) attack by simply knowing the victim’s MAC address.
Another very common type of attack is the forgery of DNS addresses in the configuration of the router through servers controlled by the attackers, a variant mainly used to attack users of online banking services and payment systems such as PayPal, Visa, Mastercard, among others.
As vulnerability assessment experts mentioned above, threat actors exploit known vulnerabilities to access these devices; Although these flaws have been widely reported, administrators don’t usually worry about the security of these devices, so patches aren’t always installed even though it’s been years since this started to be an issue.
In addition to routers, these kinds of vulnerabilities affect VoIP phones, network cameras, and other computers that allow remote configuration via CWMP. Port 7547 is typically used for this. As a vulnerability assessment method, users can check their status on the router using Steve Gibson’s free Shields Up service. To do this, simply enter your URL and then add the following command:
/x/ portprobe=7547
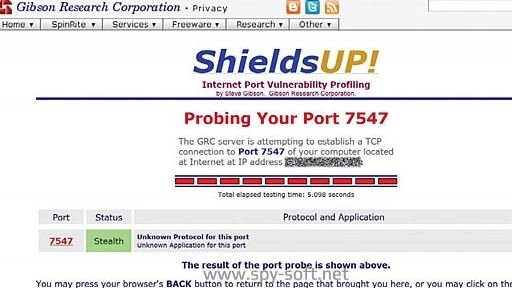
It should be mentioned that the result thrown by ShieldsUp! It is only 100% reliable when confirming the finding of a failure on the affected router, so a negative result does not guarantee that the device will not be affected by any vulnerability.
Another way to perform a free home network audit is to download and run Avast Antivirus. Its latest versions contain the Network Check Wizard, which identifies known vulnerabilities and dangerous network configurations.
ROUTER PROTECTION
There are other well-known issues that network device owners or (less often) their manufacturers don’t want to fix. Two years ago, DefenseCode experts discovered a whole set of vulnerabilities in the routers and other active network computers of the nine largest firms. All of them are associated with incorrect deployment of key component software. In particular, the UPnP stack in broadcom chip firmware or using older versions of the libupnp open library.
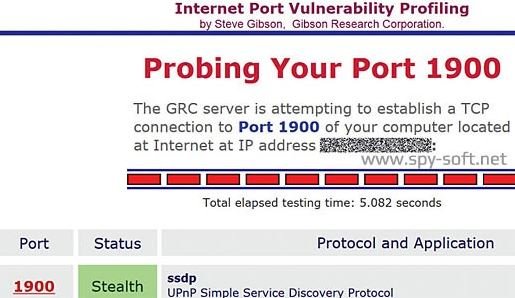
Together with Rapid7 and CERT specialists, DefenseCode employees found about seven thousand vulnerable device models. During more than half a year of active scanning of a random range of IPv4 addresses, more than 80 million hosts responded to a standard UPnP request for a WAN port were identified. One in five of them supported the Simple Object Access Protocol (SOAP) service, and 23 million allowed arbitrary code to be executed without authorization, mentioned by vulnerability assessment experts.
In most cases, this is done through a modified SOAP request, which leads to a data processing error and the rest of the code enters an arbitrary area of the router’s RAM, where it runs with superuser rights. On home routers, it is best to disable UPnP completely and ensure that requests to port 1900 are blocked. Steve Gibson’s same service will help in this.
FACTORY SETTINGS
Vulnerability assessment is considered the most common security weakness. Not only does this have to do with internal IP addresses, passwords, and administrator login common to the entire device series, but also include services that increase convenience at the expense of security. In addition to UPnP, the Telnet remote control protocol and Wi-Fi Protected Configuration Service (WPS) are typically enabled by default.
Finding critical failures in Telnet request processing is common. For example, the D-Link DIR-300 and DIR-600 series routers allow you to remotely receive a shell and execute any command through the telnetd daemon without any authorization. Using the Shodan analysis tool, researchers will be able to find a vulnerable router in a matter of moments. The following steps depend on the hacker’s profile; if it’s a white hat hacker, these weaknesses could be corrected. Instead, malicious hackers will surely try to compromise these devices.
ROUTER VULNERABILITIES
Due to firmware errors, SOMETIMEs WPS settings remain enabled even after you shut down the router through its web interface. You can find out if this happens using a WiFi scanner like WiFi Analyzer, available for virtually all Android smartphone models.
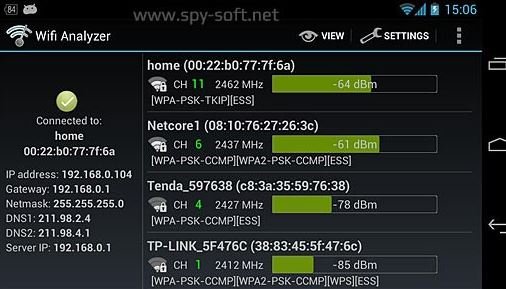
To prevent further damage, vulnerability assessment experts recommend that you do not accept commands on the WAN port or configure a specific IP address to use Telnet.
ALTERNATIVE SERVICES
The most popular open source firmwares are DD-WRT, OpenWRT and Gargoyle. They can only be installed on routers in the list of compatible ones, that is, those for which the chipset manufacturer has revealed complete specifications, vulnerability assessment specialists point out.
For example, Asus has a separate series of routers originally designed with DD-WRT in mind. It already has twelve models from the domestic to the corporate level. MikroTik routers run RouterOS, which is as flexible as the WRT family. It is also a complete network operating system based on the Linux kernel, which supports absolutely all services and any configuration imaginable.
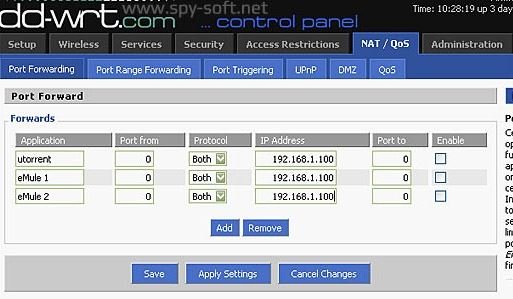
It is currently possible to install alternate firmware on many routers, but be careful and verify the full device name, as duplicate names may exist.
It is important to note that installing an alternative open source firmware is just one way to increase protection, so this will not provide complete security. All firmwares are modularly built and combine a number of key components; when a problem is found in them affects millions of devices in the same way, so each administrator will need to take the necessary precautions to prevent exploiting vulnerabilities on their devices.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
