In their latest research, Microsoft security teams detected a phishing campaign using more than 300,000 unique subdomains used in all sorts of attacks. The detection of these domains eventually led to the discovery of BulletProofLink, a phishing-as-a-service (PhaaS) platform dedicated to selling attack kits, email templates, hosting and other services for a relatively low price.
Also known as BulletProftLink or Anthrax, this is the operation responsible for many of the most ambitious phishing campaigns recently detected, offering various cybercriminal groups access to their malicious resources through a monthly subscription, guaranteeing a constant income to their developers.
The findings of this research were recently published in an extensive security report. Below, we will show the most important aspects of BulletProofLink, its methods, scope and potential risk to affected organizations.
Before proceeding, we must consider that phishing as a service operates similarly to ransomware-as-a-service (RaaS) platforms, in which malware creators and affiliates act together to deploy as many attacks as possible; while affiliates deploy the attacks in the wild and keep most of the profits for doing the dirty work, RaaS platforms receive a portion of the profits made from an attack and the payment of monthly subscriptions.
Phishing-as-a-service (PhaaS) developers provide a complete infrastructure for the deployment of these attacks, creating fake login pages, hosting platforms, templates, and hacking tools.
How BulletProofLink works
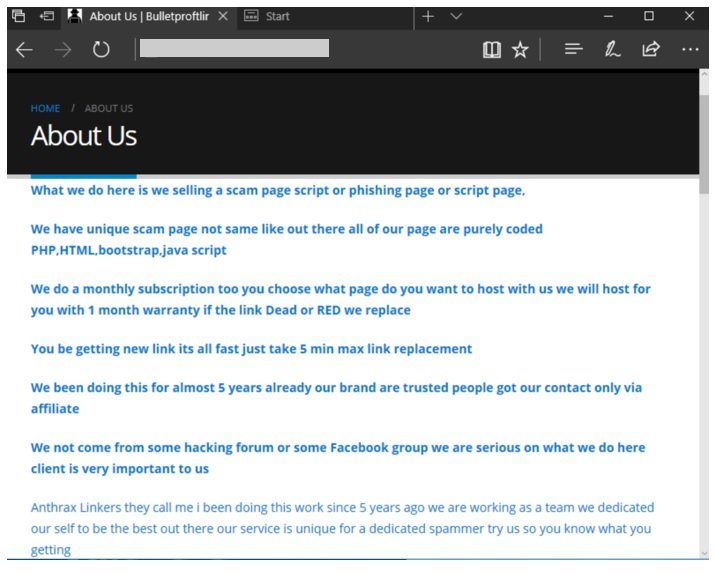
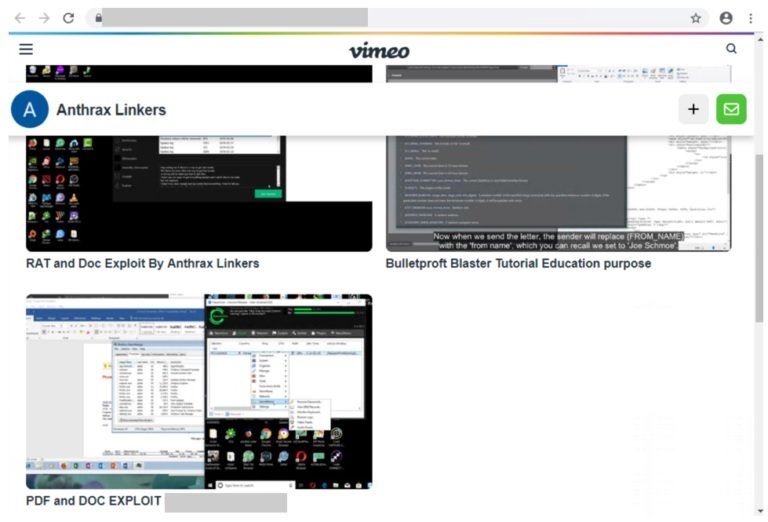
In the “About” section on their website, the developers of this PhaaS platform claim that BulletProofLink has been active since 2018, offering prominent services for spam and email engagement campaigns. Operators control other platforms with the aliases BulletProftLink and Anthrax, including blogs and accounts on YouTube and Vimeo with tutorials and promotional material.
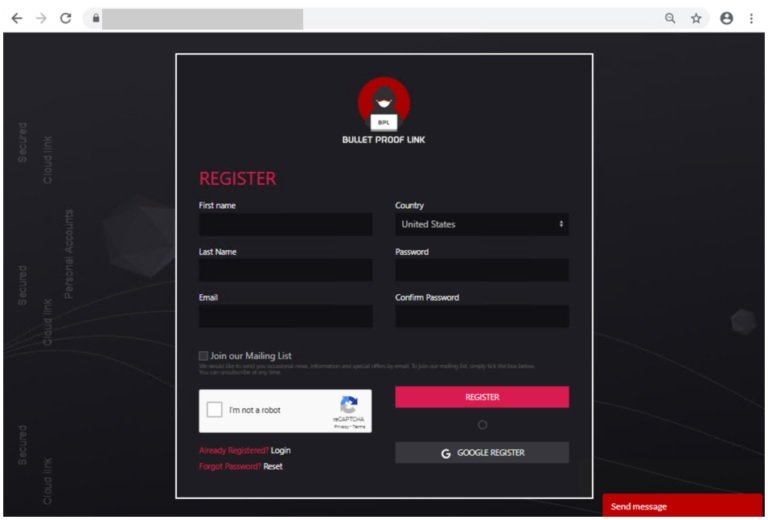
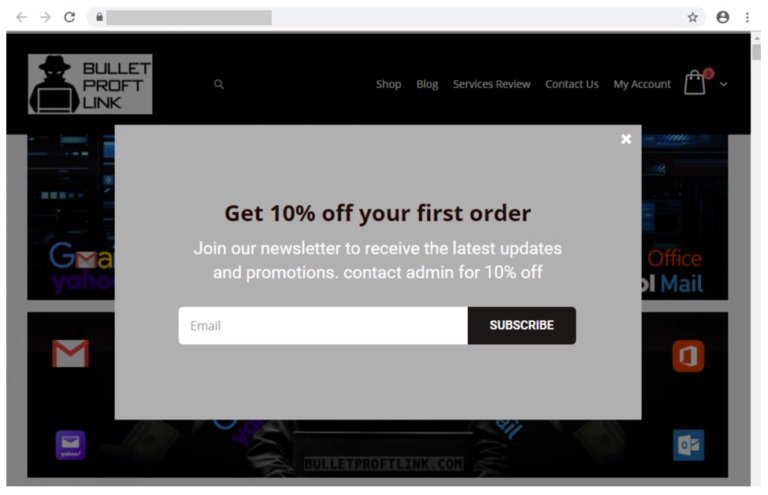
In addition, BulletProofLink has an online store where customers can register, log in and subscribe to the platform. Microsoft researchers detected multiple changes to this store throughout their analysis, although in essence this platform works like any other monthly payment service, even offering discounts to its new users.
Email templates
BulletProofLink offers more than 100 email templates for the deployment of phishing campaigns against all kinds of users and organizations. Threat actors can maintain full control of stolen information by creating their own collection pages or by using the platforms offered by BulletProofLink.
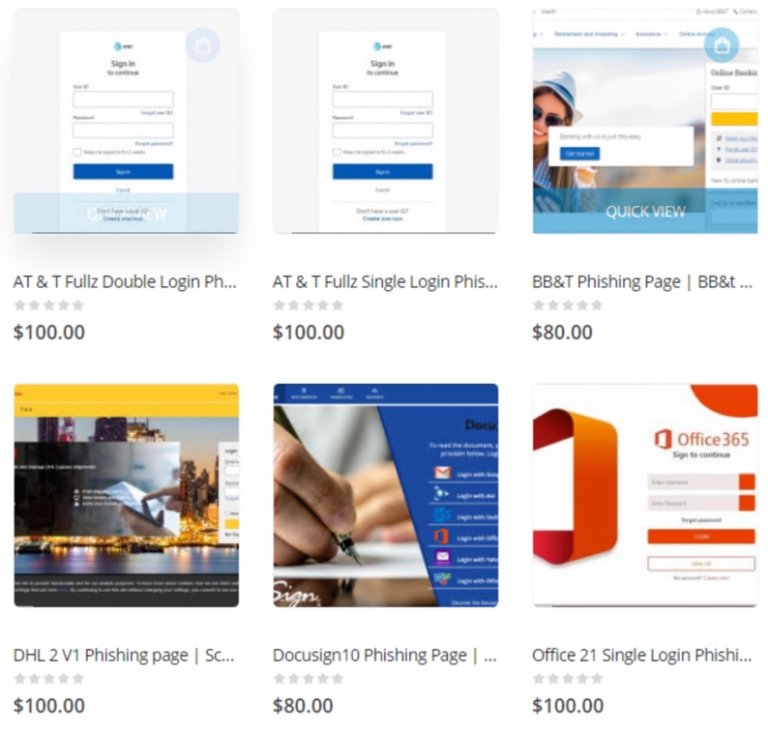
The analysis of the templates concluded that they are designed to evade detection in the target system, in addition to the enough that a simple look at these tools would not be enough to say that they were created by the same attackers, since all the templates are different from each other and only similarities can be found in their source code.
Support and hosting
Phishing platform hosting is another of the top services offered by BulletProofLink, with prices ranging from $50 USD for single-use links up to $800 USD for a full monthly subscription. The most common payment method seems to be Bitcoin, although other cryptocurrencies will most likely be accepted.
The website also includes a user support section with which customers can request further reports for the use of these malicious tools. This is not the only way to contact the creators of BulletProofLink, as customers can also receive advice via Skype, ICQ, deep web chat forums, among other ways.
BulletProofLink attack
As mentioned at the beginning, this PhaaS platform was detected during the investigation of a very aggressive phishing campaign using the BulletProofLink kit on sites created by attackers or that are part of the service. Microsoft researchers mention that the campaigns deployed since this operation employ a technique known as “infinite subdomains”, an attack method based on the use of a single URL for each attack target that has enjoyed increasing popularity among the cybercriminal community.
In one of the cases analyzed, an attacker employed the Microsoft logo intentionally using erroneous colors as a method to avoid detection by Microsoft, based on tracking the company’s distinctive colors.
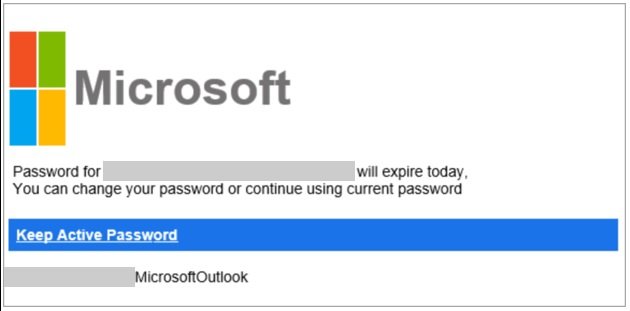
The messages also employ a technique called “zero-point font,” where they can populate the HTML code in the email with characters invisible to the target user, obfuscating the email’s malicious content in an attempt to evade detection. This is another technique of growing popularity among hackers, the researchers say.
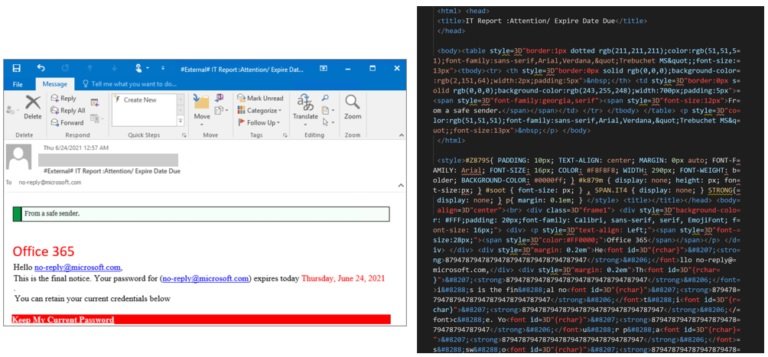
The phishing URL contained victim information encoded in Base64 along with a site owned by the attacker to which users are redirected. In this campaign, a unique base domain was used for the infinite subdomain technique, initiating campaign redirects and leveraging secondary sites for weeks.
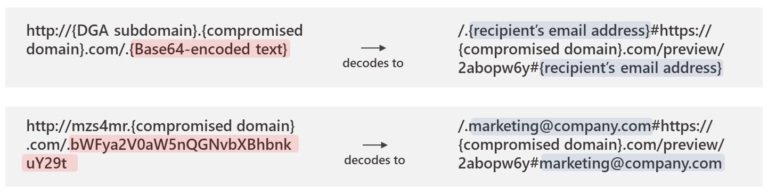
Even though law enforcement in multiple countries has already detected this operation, BulletProofLink remains a critical part of multiple active phishing campaigns, with large volumes of redirects to its password processing links from legitimate web hosting providers.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.