The Morpheus processor has caught the attention of the cybersecurity community thanks to its advanced security measures, which have allowed it to undergo more than 500 hacking attempts that have proved useless. This processor is able to constantly rewrite its architecture, making it impossible for threat actors to exploit vulnerabilities typical of conventional x86 processors, including Spectre and Meltdown flaws.
Morpheus was developed as part of a DARPA-funded project and has undergone some 580 security tests in which researchers try to hack a database by injecting code into an underlying system. Researchers have spent more than 13 thousand hours trying to hack this system without successful results.
Todd Austin, a professor of computer science at the University of Michigan, says: “The approach to addressing each security flaw individually is a lost battle, developers create code at incredible speed, and as long as this process continues to advance new vulnerabilities will continue to appear frequently.” Morpheus addresses a novel approach, because even if a threat actor finds a security flaw, the information needed for its exploitation could disappear within seconds.
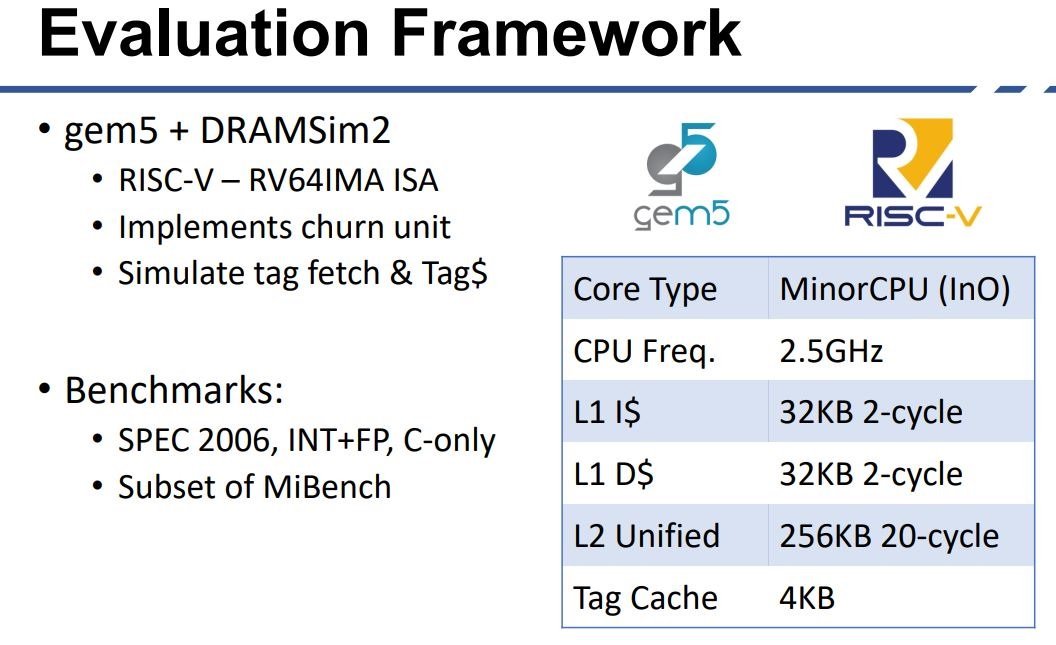
On its technical specifications, Morpheus uses the gem5 simulator in an Xilinx FPGA and simulates a core in order of 4 stages MinorCPU running at 2.5GHz with 32KB L1i and 32KB L1d. The L2 cache was 256 KB.
Austin mentions that Morpheus was developed with the aim of creating a difficult implementation to hack with any exploit focused on known vulnerabilities, which made it necessary to hide critical information from attackers while maintaining the integrity of the programmer’s tasks, but how was this goal achieved?
Developers chose to hide a data class known as “indefinite semantics,” which are pieces of information that the end user or developer does not need to know to operate a system. Austin compared this process to the action of driving a car: “To drive a vehicle we just need to know how to handle the steering wheel, gear lever and pedals; we shouldn’t even know the horsepower or the slightest details of the engine processes.”

Morpheus can encrypt memory pointers every 100 milliseconds as many times as needed. This constant encryption of information prevents threat actors from having the time to launch successful attacks, because by the time they can inject an exploit Morpheus settings will have changed.
Developers believe that Morpheus has already passed all the tests needed to demonstrate its anti-hacking capability, so they already plan to turn it into a business effort for the benefit of individual organizations and users, although this could take months or even years. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
