Cybersecurity experts have developed a new open source tool that makes it easier to use Hashcat. Dubbed CrackQ, this tool provides users with a REST API and a JavaScript graphical user interface (GUI) to interact with Hashcat in a more efficient way.
As users may remember, Hashcat is a powerful online password recovery tool that uses the power of graphics cards to find a plain text equivalent of a hashed password.

According to Dan Turner, a pentesting specialist who collaborated on the project, CrackQ’s goal is to make Hashcat one of the most effective tools in the ethical hacking community, as it has become incredibly popular for multiple security teams, pentesting and other groups specializing in offensive security.
Although CrackQ is not the first GUI tool written for Hashcat, it contains multiple features that make it stand above the rest. To get started, the tool is written in Python, allowing you to interact through libhashcat faster than running shell commands. In addition, Python contains multiple libraries that make it easy to add functions to Hashcat.
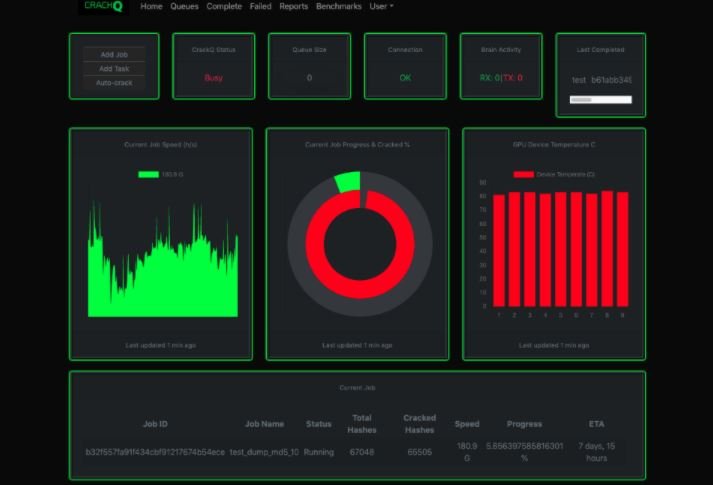
CrackQ can generate multiple analysis reports and dashboards from Hashcat results, including time and speed, insecure password patterns, and heat maps of common city names used in passwords.
Other tools for Hashcat use distributed computing, where they share the load across multiple computers. CrackQ uses a server/client architecture, with all commands running on the server: “Pentesters typically use dedicated GPU servers or custom computers, which are then shared by the computer,” Turner adds.
CrackQ is in the alpha version testing stage. Developers will expand the feature set in the coming months: “This first version had to do with creating a good foundation, ensuring it was a very stable application and making it more accessible to everyone,” concludes the expert.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
