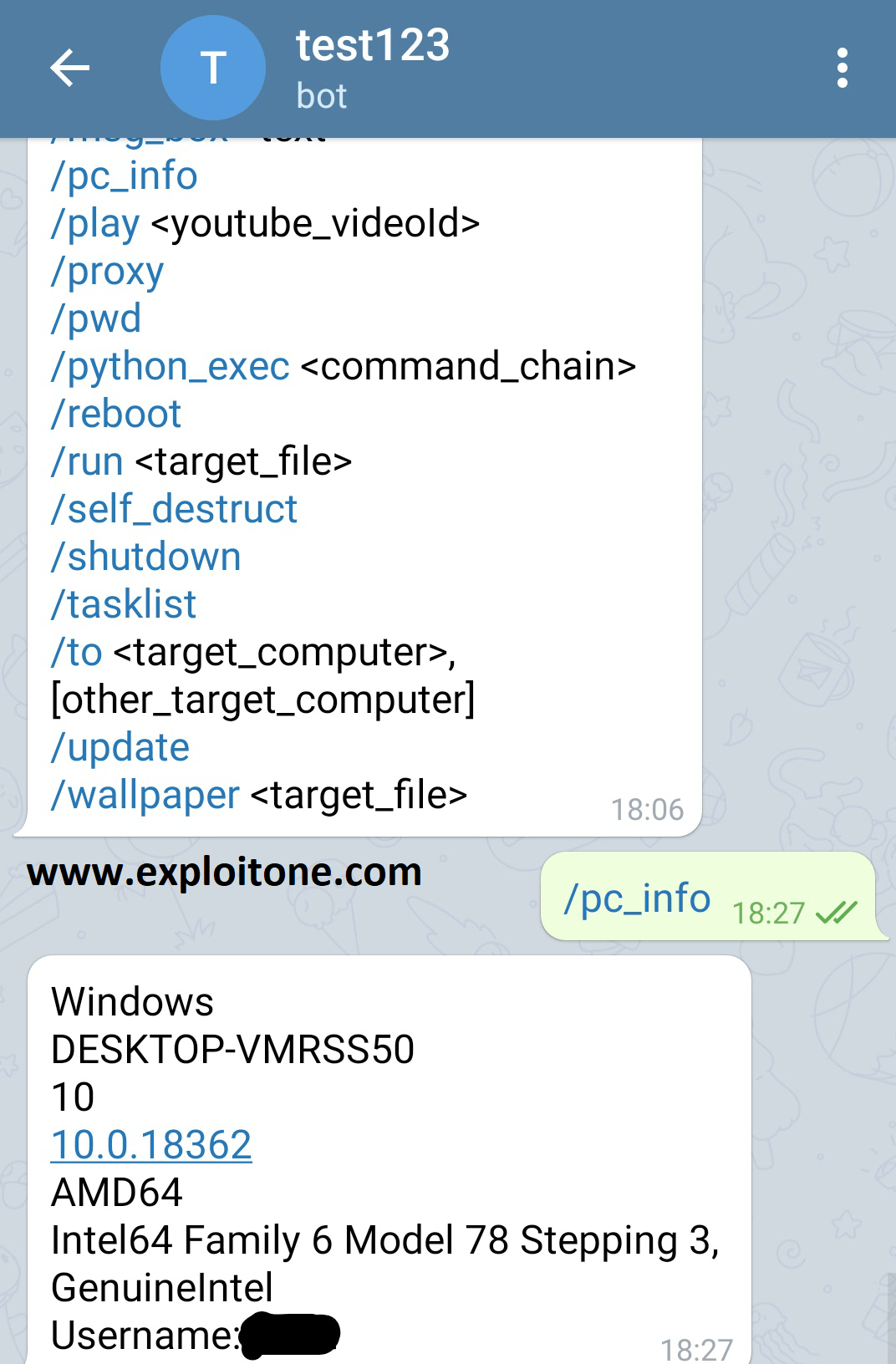
Webex vulnerabilities are being exploited by hackers using simple attacks
The Phishing Defense Center (PDC) has revealed the detection of a new campaign designed to extract login credentials from Cisco WebEx users by abusing an application-included security tool. To theRead More →