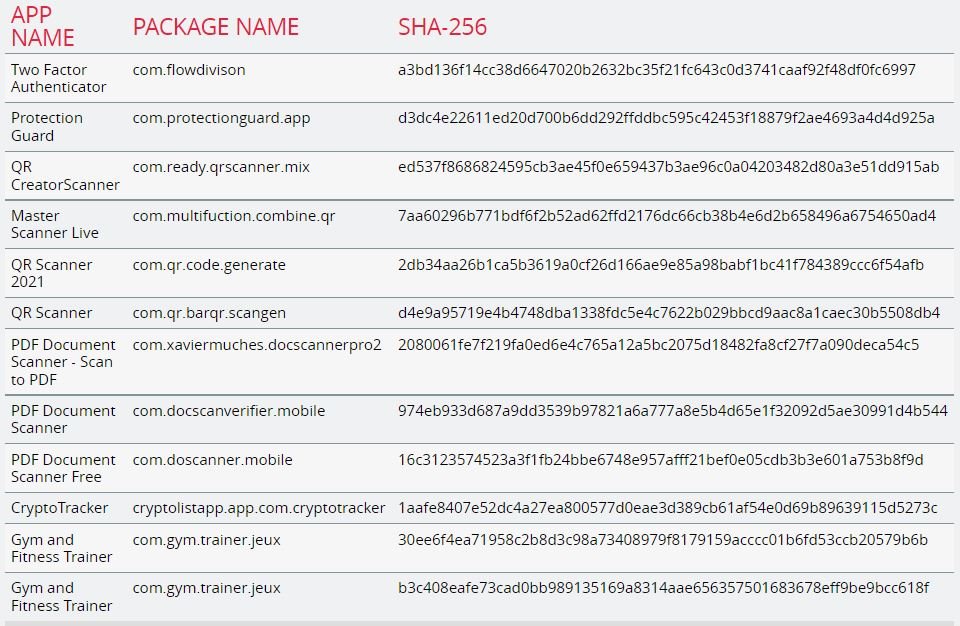
A recent investigation claims that a set of mobile apps available in Google official store and accumulating more than 300,000 downloads contain banking Trojans capable of stealing login credentials and multi-factor authentication codes, keylogging and taking screenshots on affected devices.
The malicious payloads were hidden in simple tools, including cryptocurrency wallets, QR scanners, and PDF readers, which remained available on the Play Store for at least 4 months. Below is a list with the malicious apps:
The developers of these apps resorted to various tricks to evade Google’s security mechanisms, based on limiting the use of functions such as the Accessibility Service of the Android system, a tool that many malicious apps abuse to commit their attacks. According to ThreatFabric researchers, this tactic is still functional because hackers leave minimal logs of malicious activity, which prevents the detection of malware using sandbox environments and machine learning.
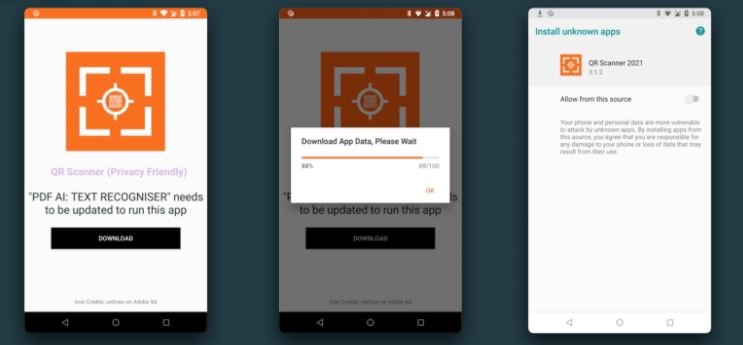
It all starts with the development of a legitimate app that, when installed on the target device, sends the user a message to download additional content. In general, these apps request the download of apps from unofficial sources, a very common practice but not recommended for technology users.
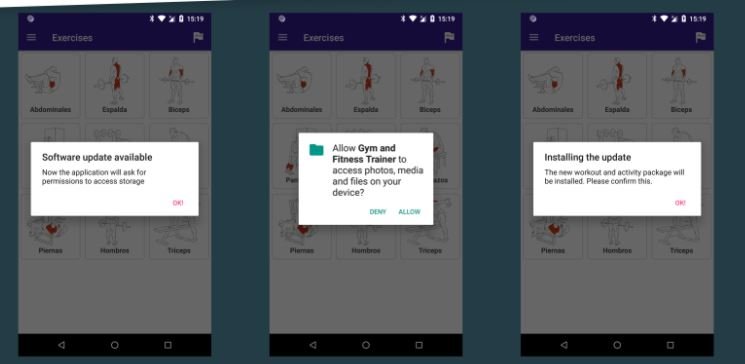
Initial applications are not detected by VirusTotal or other malware scanners, so there are no indications of malicious activity. It should be noted that hackers analyze the location details of the affected device, as they apparently only attack users in specific regions.
If the affected system meets the requirements, one of the four malware variants detected in this investigation is delivered. The main threat appears to be Anatsa, a Trojan for Android systems with extensive malicious capabilities, including remote access and automatic transfer to empty the affected user’s online banking accounts.
In addition to Anatsa, three more malware families were detected in this research, including Alien, Hydra, and Ermac, in addition to the Gymdrop dropper for malware delivery. This dropper also does not require the Accessibility Service to operate, as it simply deceives the user by requesting permission to install additional packages.
Although Google ensures that its mechanisms to detect malicious apps work, the detection of malicious apps in the Play Store is very common, so it is up to users to take the best measures to prevent their devices from running any malicious tool disguised as legitimate apps.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
