Security researchers at Cleafy’s fraud prevention firm report the finding of a new malware variant for the Android operating system aimed at users in multiple European countries. Identified as TeaBot, this malware appears to have been found at an early stage of development, although experts note that it has advanced capabilities such as credential theft and text message interception.
So far researchers have identified at least 60 attack targets, including banks in Spain, Italy, Spain, the Netherlands and Belgium. TeaBot supports six languages, including German, English, Italian, French, and Spanish.
Other capabilities of this malware allow operators to remove applications installed on affected devices, change audio settings, access the contact list, and take multiple records of the current state of the device.
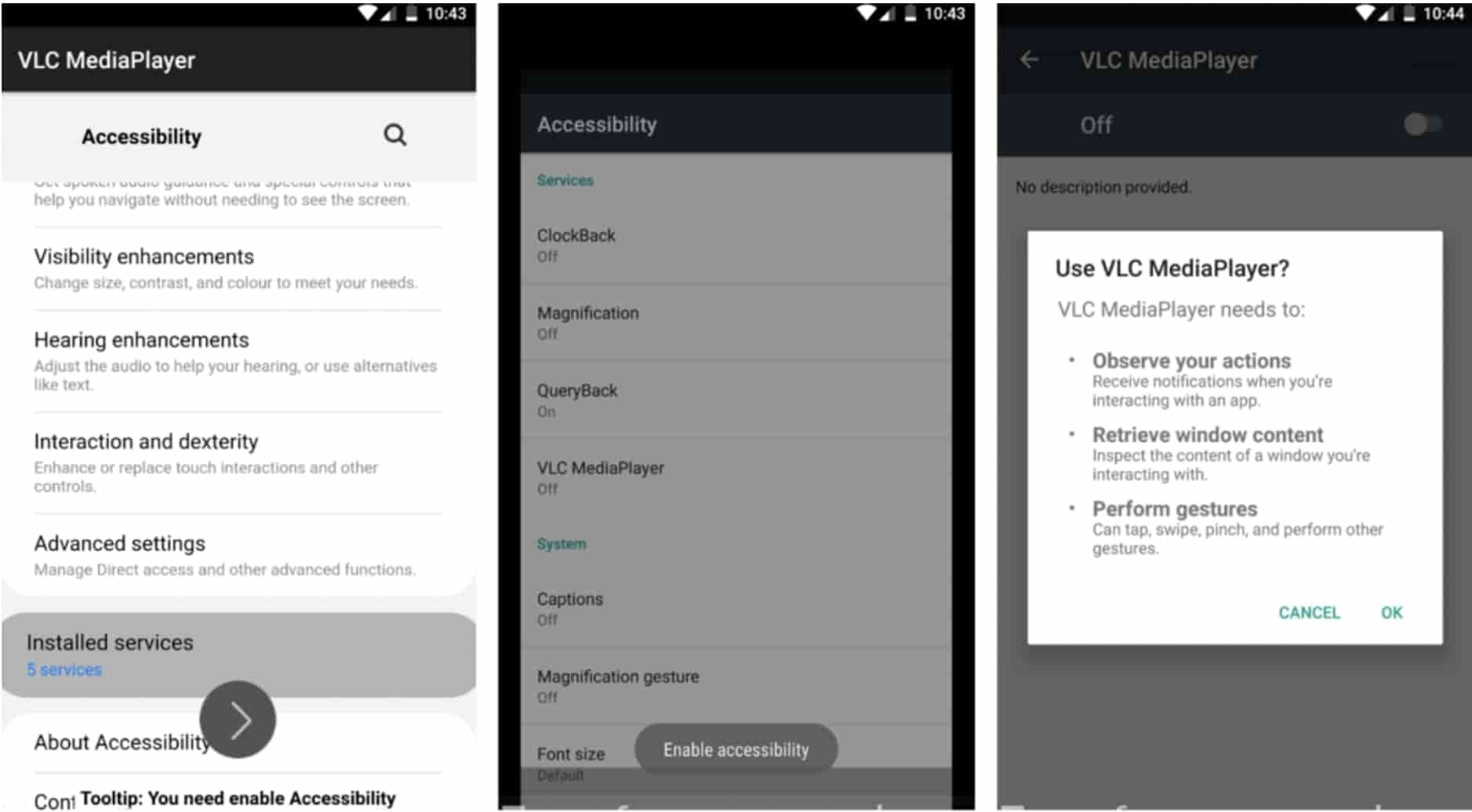
TeaBot operators can also take screenshots on affected devices and compromise Android Accessibility Services, displaying a pop-up window so users have no choice but to accept arbitrary accessibility permissions. This is a critical situation as it would allow threat actors to track all the victim’s interactions with the affected smartphone.
Researchers believe that TeaBot is similar to other malware identified as Oscorp, as both variants rely on seeking real-time interaction with compromised users, in a combination of abuse of Android settings with an account hijacking attack.
As if that wasn’t enough, TeaBot is able to steal multi-factor authentication codes on compromised devices, so threat actors could try to access other accounts of the affected user. Finally, experts discovered that TeaBot can disable Google Play Protect, a feature for automatic scanning of apps available in Google’s official store that prevents the presence of malicious apps on Google Play.
It should be mentioned that the Flubot banking Trojan also uses the same lure to infect Android devices, but researchers rule out a link between the two malicious developments.
As usual, users of android smartphones are advised not to download apps from sources outside the Google Play Store, as there are no security controls on those platforms for the detection of potential malicious apps. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
