To protect ourselves against hackers, it is not enough to be careful with the apps we install, we also have to worry about what we connect to our device.
Just when you think you’ve protected your system as well as you can, a new attack vector appears, a new technique that makes all your work obsolete.
And that’s fine. Not all hackers have malicious interests, and many want to find security holes precisely to cover them up and prevent others from using them; even if that means exploiting a process as common and simple as connecting a cable to our mobile.

The cable that hacks the mobile
Oddly enough, the O.MG Cable presented at the last Def Con, a conference for hackers and cybersecurity experts, is capable of doing just that. Although at first glance it looks like a conventional cable, inside it has the necessary hardware and software to steal our data and send it to an external server using Wi-Fi, as explained in The Verge.
In effect, the cable itself has a Wi-Fi connection, which speaks volumes about the complexity of this project; its creator, known simply by the acronym MG, has managed to integrate all the necessary chips into the USB connection itself, so that the attacker only has to get the victim to use the cable, for example, to charge the mobile, and the device will do all the work.
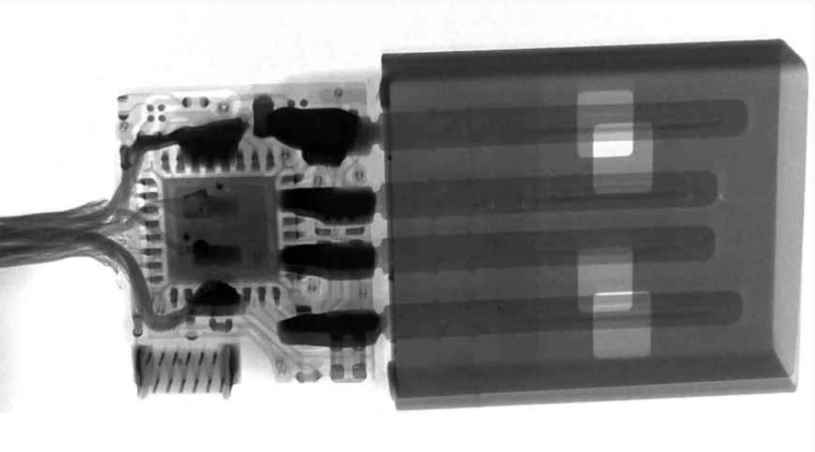
The cable is able to fool the system because it passes itself off as a USB keyboard, and in this way it is able to insert commands and execute them; In the same way, it is also capable of recording everything we write on the mobile while the cable is connected, saving up to 650,000 keystrokes in the internal memory. That includes data that is not normally obtainable because the connection is encrypted, such as our password or our bank details.
The attacker doesn’t even have to get the cable to retrieve the stolen data; the integrated Wi-Fi connection allows you to connect to an external server in which to record the information. In this way, the usual security measures are bypassed, such as antivirus or firewalls, since the connection is not made through the mobile. That also means the cable is capable of getting data from ‘air gapped’ systems, which are not connected to the internet for security.

The cable can be configured with different connections, such as USB-A, USB-C or Lightning for iPhones; in the same way, it is compatible with all kinds of operating systems, such as Android, iOS, Windows and macOS.
The O.MG Cable has been designed as a tool for professionals to test the security of their systems, and the price of $179.99 reflects this. Although it is unlikely that you will be the victim of an attack with this cable, this is a good reminder that you should never connect unknown devices to your mobile or computer, be they cables, USB sticks or anything else, since physical access is the most coveted by hackers.
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
