Play Store security teams confirmed that SharkBot, a dangerous banking malware distributed through fake antivirus tools, has finally been removed from Google official repository.
SharkBot was first spotted on the Play Store in October 2021. Since then, the malware has continued to spread through various malicious apps in the official Android app store, ironically employing supposed security tools.
This malware allows threat actors to empty the bank accounts of affected users, gaining full access to the compromised accounts. In this way, infected devices will continue to send money to accounts controlled by threat actors.
With a successful attack, threat actors will no longer need to steal their victims’ login credentials or evade multi-factor authentication systems. Thus, the attack makes a complex password and any additional means of authentication completely useless once SharkBot takes control of an Android device.
Google has already identified at least 6 malicious apps with SharkBot payloads, all hidden as antivirus and anti-malware products. By the beginning of March, four malicious apps distributing the banking Trojan had already been identified.
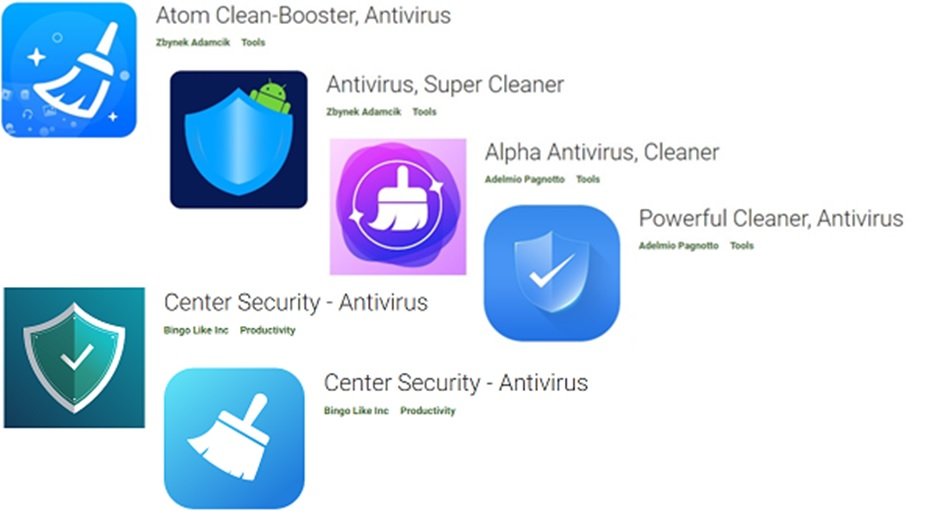
The applications identified as part of this campaign are:
- Atom Clean-Booster Antivirus
- Antivirus, Super Cleaner
- Alpha Antivirus, Cleaner
- Center Security – Antivirus
- Center Security – Antivirus
- Powerful Cleaner, Antivirus
Security firms such as Check Point Research and NCC Group have also reported the same malicious applications to the search engine giant. Google responded to the reports by deleting the list of these apps on the Play Store a week later, only to confirm a couple of weeks later that the malware has been completely removed from the platform.
For now it’s hard to determine how many of the users who downloaded these apps are still using them, but the best way to mitigate the risk is to uninstall these supposed security tools before it’s too late.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
