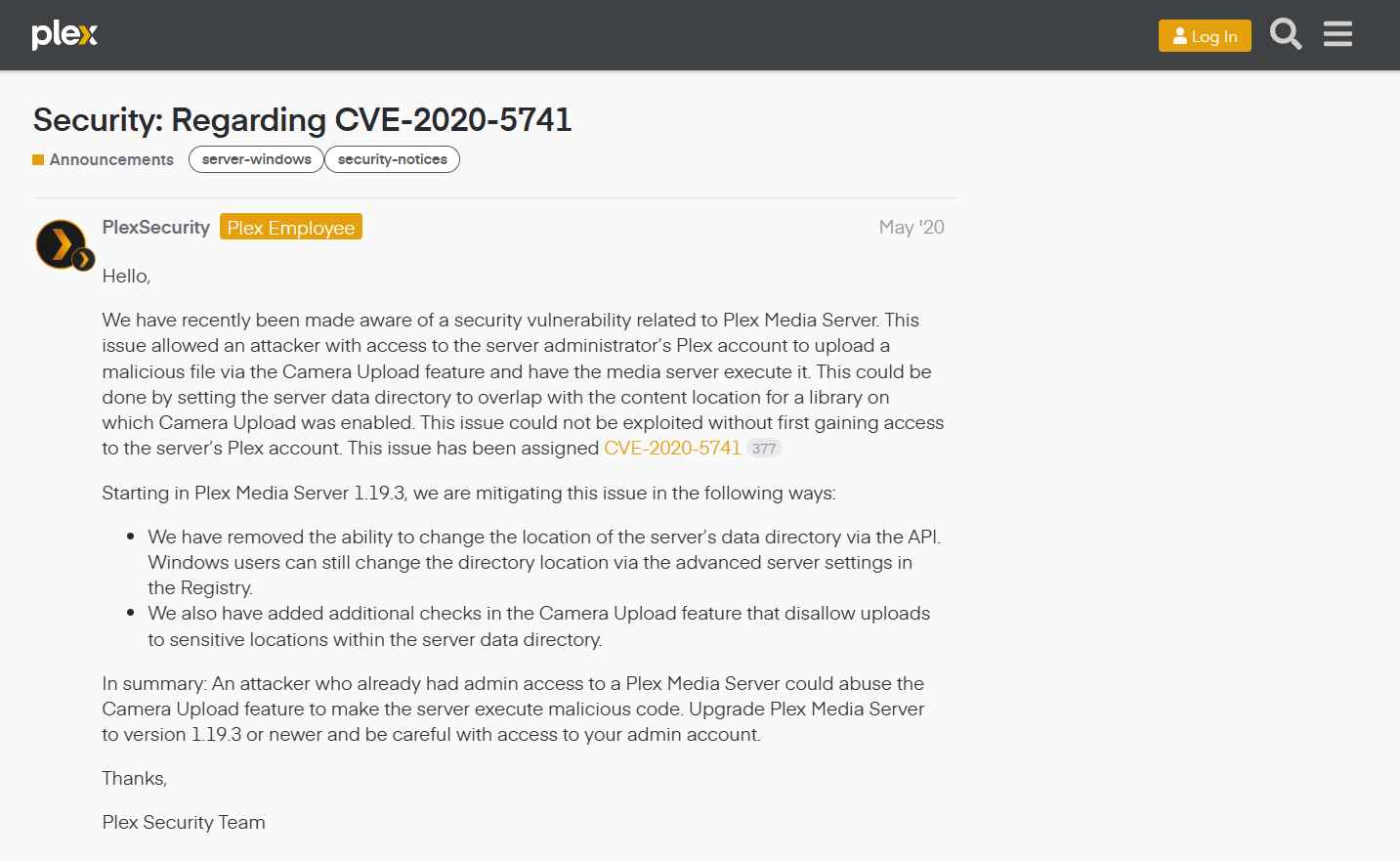
The first problem is a high-severity vulnerability in Plex Media Server that has been tracked as CVE-2020-5741 and is defined as a deserialization issue. This flaw may be abused to remotely execute arbitrary Python code if it is exploited. Due to this vulnerability, an attacker who had access to the Plex account of the server administrator was able to submit a malicious file to the media server using the Camera Upload function and have the server execute the file. The vulnerability was patched with the release of Plex Media Server version 1.19.3, and as it required an attacker to have administrative access to a Plex Media Server in order to successfully exploit it, it was very unlikely that attackers would target it.
While CISA added the vulnerability to the KEV list without sharing details on how it was exploited in the wild, recent media reports have suggested that the data breach at LastPass that resulted in the theft of user vault data might be related to a Plex bug that was exploited to hack a DevOps engineer’s computer. This is despite the fact that CISA added the vulnerability to the KEV list without sharing details on how it was exploited.
In the end, the attackers were successful in gaining access to the engineer’s credentials as well as the corporate vault for LastPass. Once the threat actors stole production backups and important database backups from LastPass, this event resulted in a huge data breach in the month of August 2022. The software package that was exploited on the employee’s home computer was Plex, even though LastPass did not disclose which software flaw was used to hack into the engineer’s computer. LastPass did not disclose which software flaw was used to hack into the engineer’s computer.
Once LastPass revealed that it had suffered a second data breach of its own in August, Plex also told its clients that their data had been compromised and requested them to change their passwords.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
