Have I Been Pwned is a service used by those who want to verify if the password they use or their email address was exposed as a result of a security incident suffered by an online service in which they have created an account. It offers an extensive database that collects email addresses, passwords and phone numbers from more than 600 websites that have been affected by a breach and more than 11,000 million exposed accounts.
As per research from welivesecurity, Cybercriminals designed a phishing site that masquerades as the official site of Have I Been Pwned, the service to check if our data was exposed in a leak. The apocryphal site not only has a design similar to the official one, but the URL is quite similar, which can lead more than one to believe that it is the legitimate one. The goal is to collect email addresses and passwords of users.
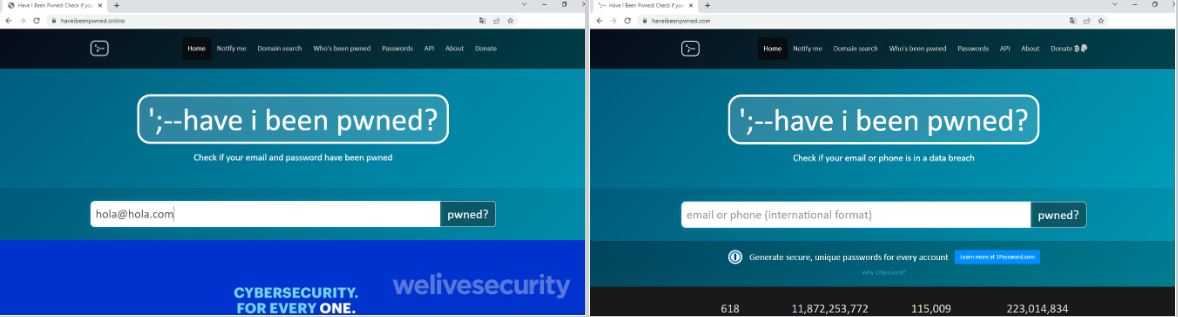
On the left the site that pretends to be HaveIBeenPwned and on the right the legitimate site.
If we look closely at the URL we can see that the difference between the legitimate site and the fake one is the extension. While on the official page it is .com, on the fake site it is different. However, the fact that the domain name is the same can lead more than one to fall for the deception. On the other hand, the aesthetics are very similar with practically the same elements.
A key change that the cybercriminals implemented in the fake site is the way of carrying out the query: while on the official page you only have to enter the email address or phone number to verify if the data was exposed in a leak, in the false site is requested to enter the email address first and immediately the field to add the password is added.
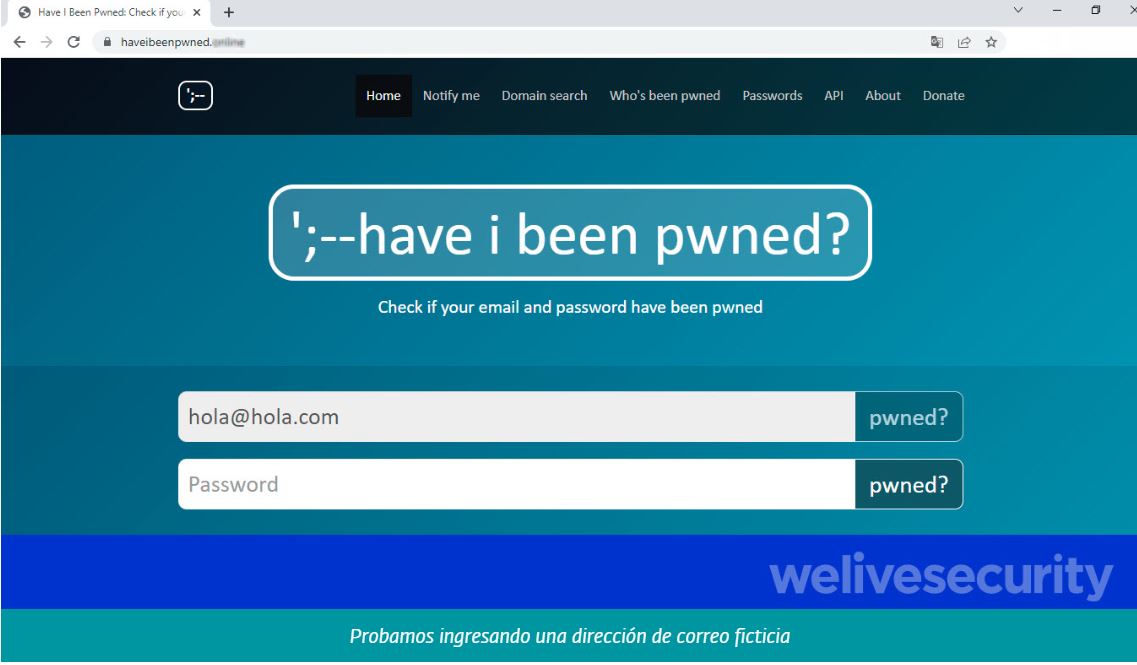
This should generate suspicion, especially for those people who used the service previously, since to verify if a password was leaked in some breach, the official site has a separate section available from the menu bar, in which visitors can verify if a password they use has been leaked, but without linking this information to a particular username or email address.
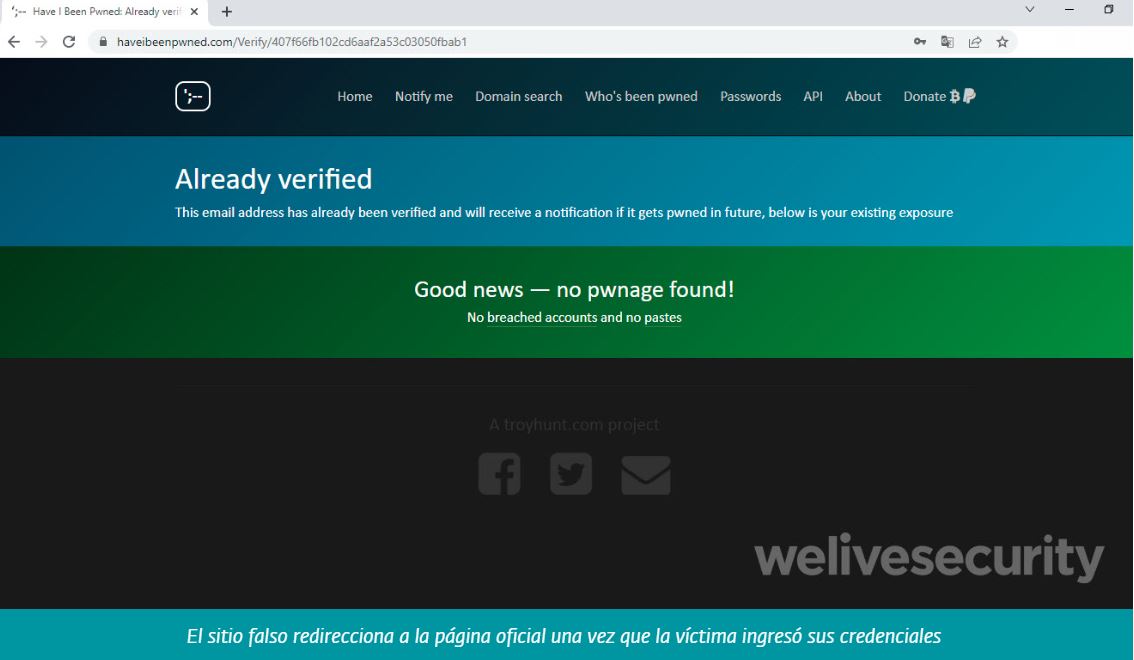
In order not to generate suspicion in the victims, after entering the data, the false site will redirect to the legitimate site, indicating that the credentials entered were not registered in any breach.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
