Reports indicate that a group of threat actors managed to compromise corporate networks at Virgin Mobile, based in Saudi Arabia. Apparently, hackers accessed the company’s email system and Active Directory domain controller, information that is now being sold on dark web forums.
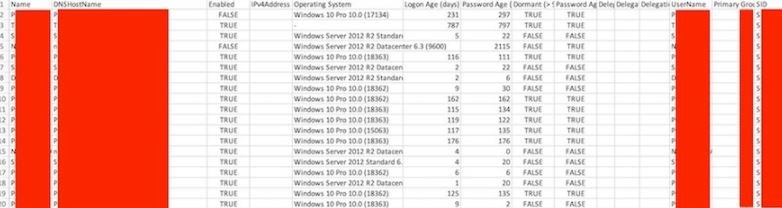
These reports have already been made up of cybersecurity specialists, who have found clues to the information exposed in hacking forums, including inter-employee emails, login activity, and spreadsheets about account managers’ performance.
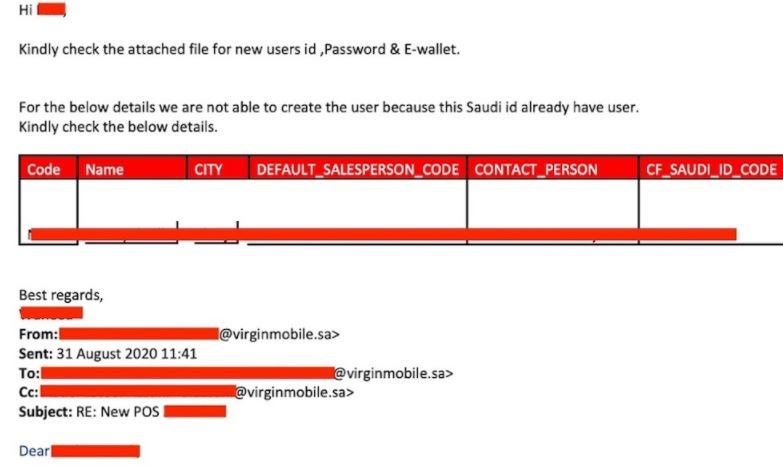
In addition, threat actors exposed more than a thousand accounts with usernames, employee names, email addresses, and password update records. The reports were confirmed by BANKINFOSECURITY.
A Virgin spokesperson stated that the causes of the leak have already been corrected, so a similar incident is expected to not be repeated. Regarding the causes of the incident, the spokesperson mentioned that it’s all due to a Microsoft Exchange-related issue that the tech company itself patched a few days ago. No details were added about the type of attack or vulnerability exploited by malicious hackers, although unofficial sources mention that attackers could have remained on the company’s networks for at least a couple of months.
On the other hand, the cybersecurity researcher and Have I Been Pwned founder, Troy Hunt mentions that samples of collected information appear “highly credible,” so the incident should be taken seriously: “We found multiple data attributes that are not normally accessible to an actor outside a private network; many things are required to go wrong for hackers to achieve such levels of access.”
Attacks on large companies in the Middle East have become a recent trend, including incidents in technology, financial services, government institutions and other organizations in countries such as Saudi Arabia, the United Arab Emirates, Jordan, Israel and Qatar.
Regarding the attackers, an Australian cybersecurity specialist who has requested anonymity mentions that, after analyzing a list of IP addresses linked to these incidents, it was possible to attribute this malicious activity to the hacking group identified by the cybersecurity community as APT35, also known as “Cobalt Gipsy”, allegedly sponsored by the Iran government, although it may be a hacking group capable of using IP addresses to divert attention from its actual location.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
