A group of malicious hackers managed to steal more than 1 TB of information patented by Saudi Aramco, one of the world’s largest state oil companies. The compromised information is currently for sale on dark web forums for at least $5 million USD. The company claims that this incident is related to security flaws of external contractors, in addition to claiming that the attack had no impact on its regular operations.
According to a report published by BleepingComputer, this incident is related to the hacking group ZeroX, who for days have been offering this information for sale. Hackers claim this database was stolen after compromising the company’s networks and servers last year and includes recent information and records from more than 20 years ago.
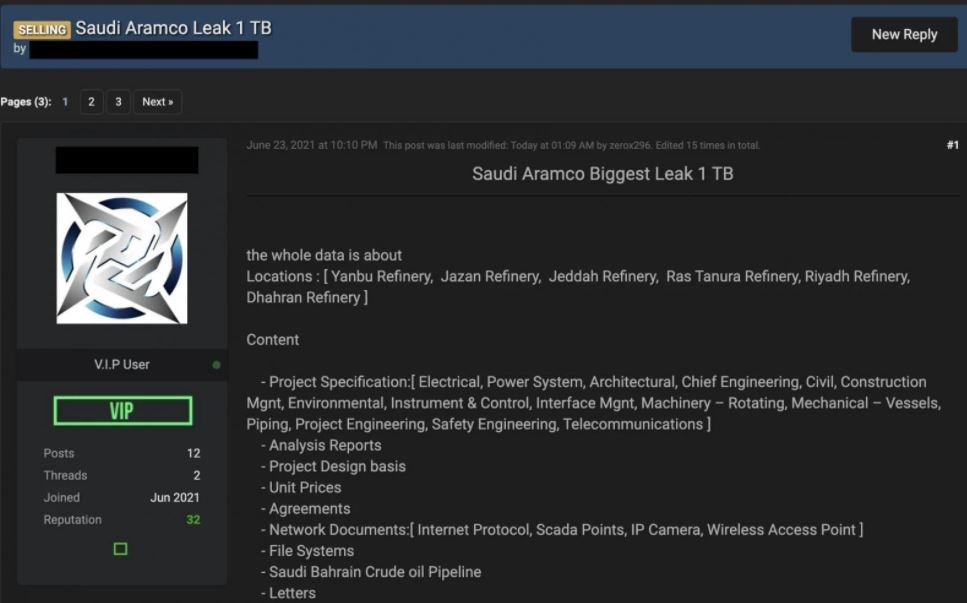
An alleged member of the hacking group answered some questions, mentioning that it was all related to exploiting a zero-day flaw, though he declined to offer further details. The hacker also posted a sample of the compromised information to demonstrate the legitimacy of the leak. The dark web post also contained a 28-day countdown, marking the start of negotiations for the database.
Among the compromised logs are sensitive details such as:
- Complete information on more than 14 thousand employees
- Project details for systems related to electricity, energy, architecture, engineering, civil, construction management, among other areas
- Internal analysis reports, agreements, letters and price sheets
- Map of precise locations and coordinates
- Customer lists
While the cybersecurity community initially attributed this leak to a ransomware infection, both the affected company and threat actors denied such a claim. This reinforces what was said by Aramco representatives, who from the outset attributed the incident to a contractor’s commitment: “We can confirm that this leak had no impact on our operations, we will continue to analyze the incident in search of any new information,” the Aramco representative concludes.
Finally, it was confirmed that the threat actors did not even report the situation to the affected company, so the possibility that this incident is related to any extortion attempt was completely ruled out.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
