Phishing remains one of the most effective cyberattack variants, and SANS can be a proof of that. Specialists mention that the cybersecurity training firm was the victim of a phishing attack after one of its employees received a simple email.
SANS is one of the world’s leading IT security training firms, so it’s unusual for many to have fallen into a phishing campaign so easily.
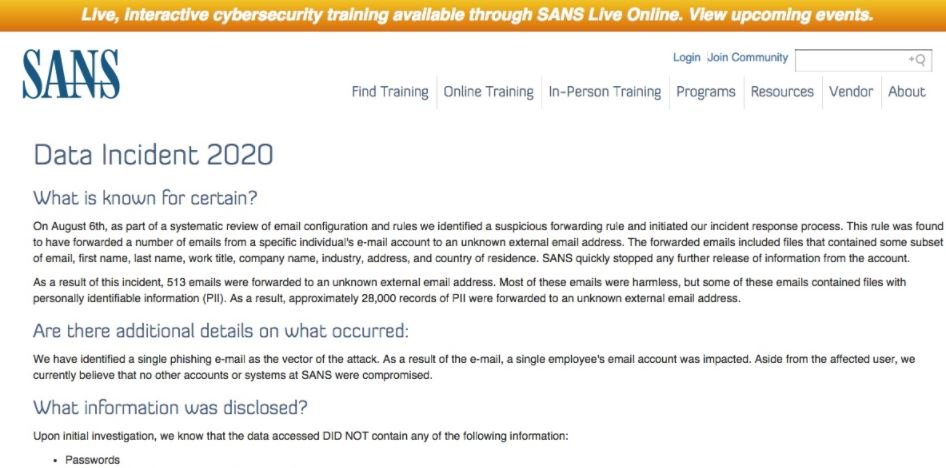
Through an alert posted on its website SANS acknowledged that an employee fell into a trap that allowed threat actors to obtain login credentials and access to an enterprise email account. The incident was detected on August 6 during a routine review: “We identified a single phishing email as the attack vector. As a result, one of our employees’ email accounts was affected. We believe that there are no other accounts or systems compromised,” the SANS alert mentions.
After gaining access, the attacker configured a forwarding rule for any email received by the compromised account to an external address, in addition to installing a malicious Office 365 plugin. The company has not revealed any further details about the plugin, although attackers likely have used Office 365 Oauth to gain persistence in the email account.
In total, 513 emails were forwarded, of which around 28,000 personal records can be obtained from the company’s employees and customers. SANS states that the information provided does not include passwords or financial data, although full names, email addresses, telephone numbers, addresses, and more may be found.
Regarding the incident investigation process, it is SANS staff the same in charge of dealing with the incident. The company ensures that all necessary measures have been taken to ensure that similar incidents are not repeated in the future. Affected users and employees are being notified and should be aware of any new phishing incidents using the compromised information.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
