According to a report by security firm Comparitech, the confidential information of more than 106 million tourists in Thailand was exposed on the Internet without any protection, leaking confidential records including full names, passport details and more, in an unusual data breach incident.
Bob Diachenko, leader of the firm’s investigation team, reports had discovered the leak on August 22, when he notified the Thai authorities, whose investigative agencies recognized the incident and began taking steps to analyze it and eliminate improper access.
The researcher believes that anyone who has traveled to Thailand during the last ten years could be affected by this leak. Diachenko even confirmed that he was able to find his own data in the leaking even though he only went to this country on one occasion.
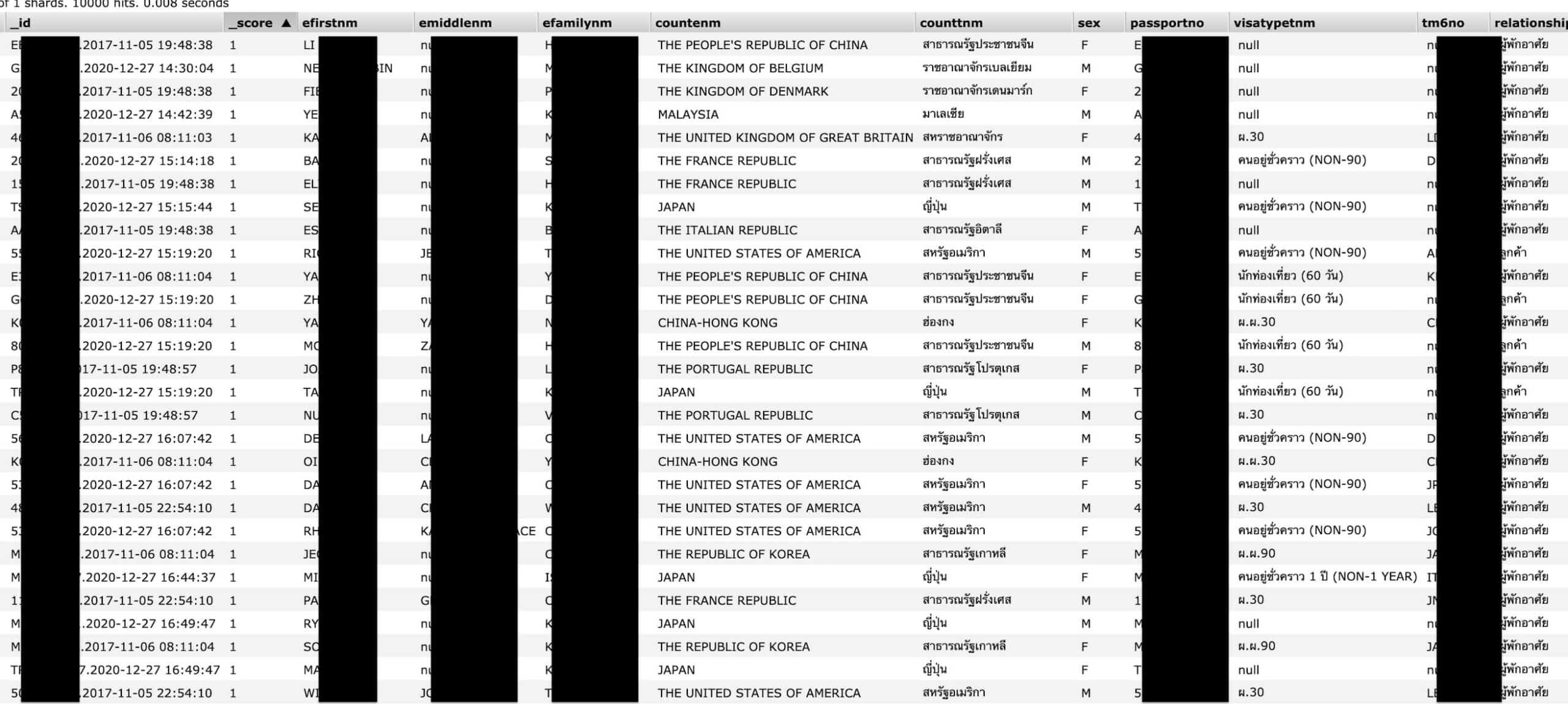
This Elasticsearch implementation had about 200 GB, equivalent to about 106 million unique records; to be precise the database exposes sensitive details such as:
- Full name
- Sex
- Passport number
- Residence Permit
- Type of visa
- Date of arrival in Thailand
- Arrival to Thailand card number
Despite the magnitude of the incident, good news is that the database contained no financial record, so this information leaking does not pose a risk of financial fraud to the millions of affected users.
It should be clarified that the IP address of the database remains public, although the Thai authorities replaced the exposed data with a honeypot after receiving the report. In this way, anyone who tries to access this data will receive a message informing that any access to that IP address will be registered for legal purposes.
Finally, even though authorities responded immediately to Comparitech’s report, it is impossible to know how long the database remained exposed. In previous cases, it has been shown that a few hours are enough for a threat actor to find a compromised database, so this kind of reports must be taken with total seriousness.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
