IT infrastructure in multiple Japanese agencies would have been compromised due to a potential flaw in the ProjectWEB information exchange tool, developed by information technology firm Fujitsu. The company confirmed that threat actors authorized some projects on this platform, compromising user information.
In an email sent to some investigators, the company confirmed the incident. “We have detected unauthorized access to ProjectWEB, so we will conduct a thorough investigation in collaboration with the Japanese authorities. Use of this tool will remain suspended until further notice.”
So far there remains no certainty about exactly how it happened, although cybersecurity specialists mention that this could have occurred either due to the exploitation of a failure or a supply chain attack.
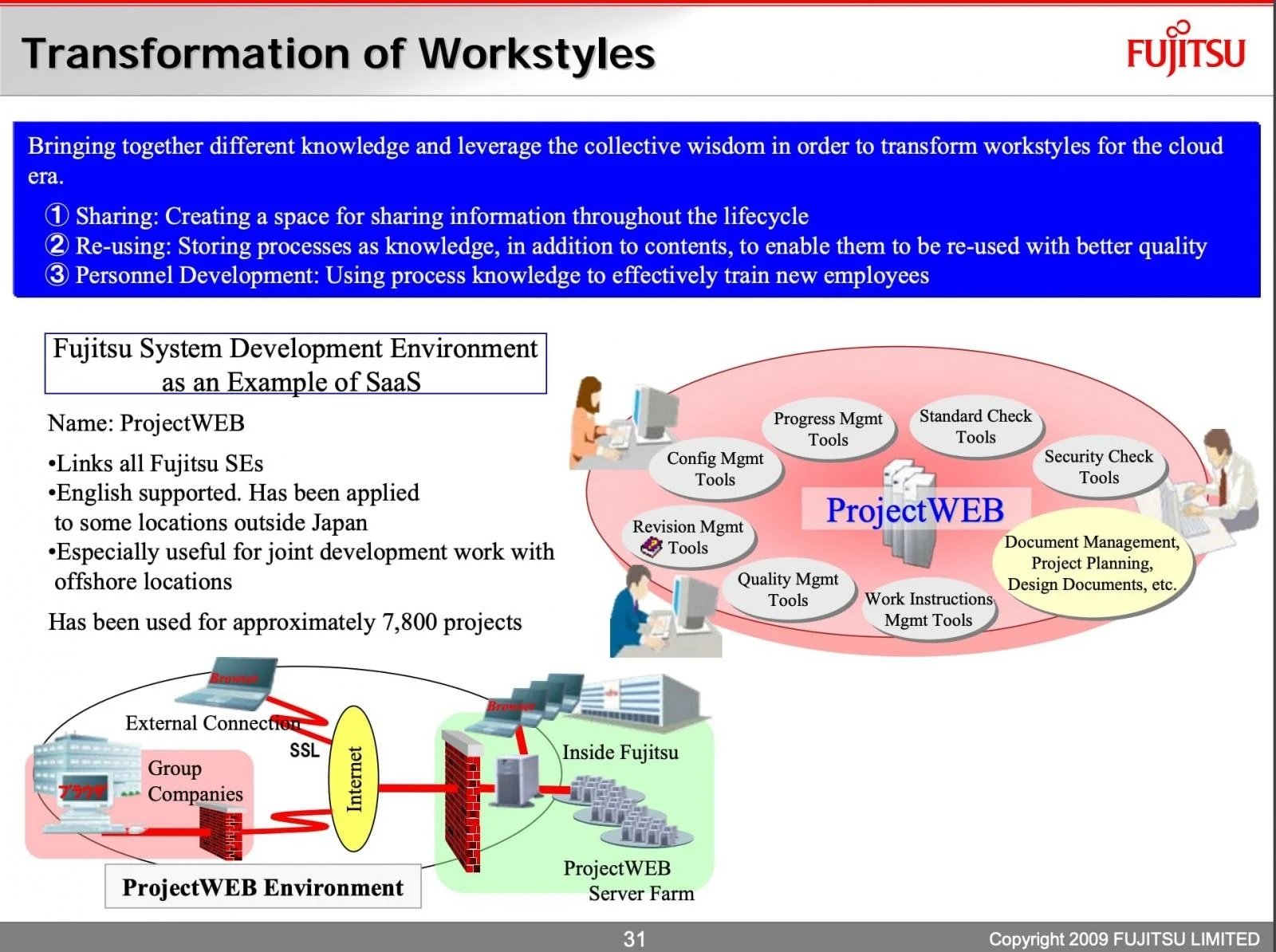
Moreover, this week the National Cybersecurity Center in Japan revealed that threat actors could have gained inside information during this malicious campaign. The company also reported data theft on some projects hosted on this tool. ProjectWEB enables members of an organization to exchange information internally to optimize workflows and share relevant data with project managers and links to other areas of the organization.
Through this unauthorized access, threat actors accessed at least 75,000 email addresses and confidential records, including email settings and internal documentation. It should be mentioned that the compromised tool is very popular in Japan, managing around 7,000 public and private projects.
At the moment the company’s website is out of service, which is believed to be a temporary security measure as the investigation concludes.
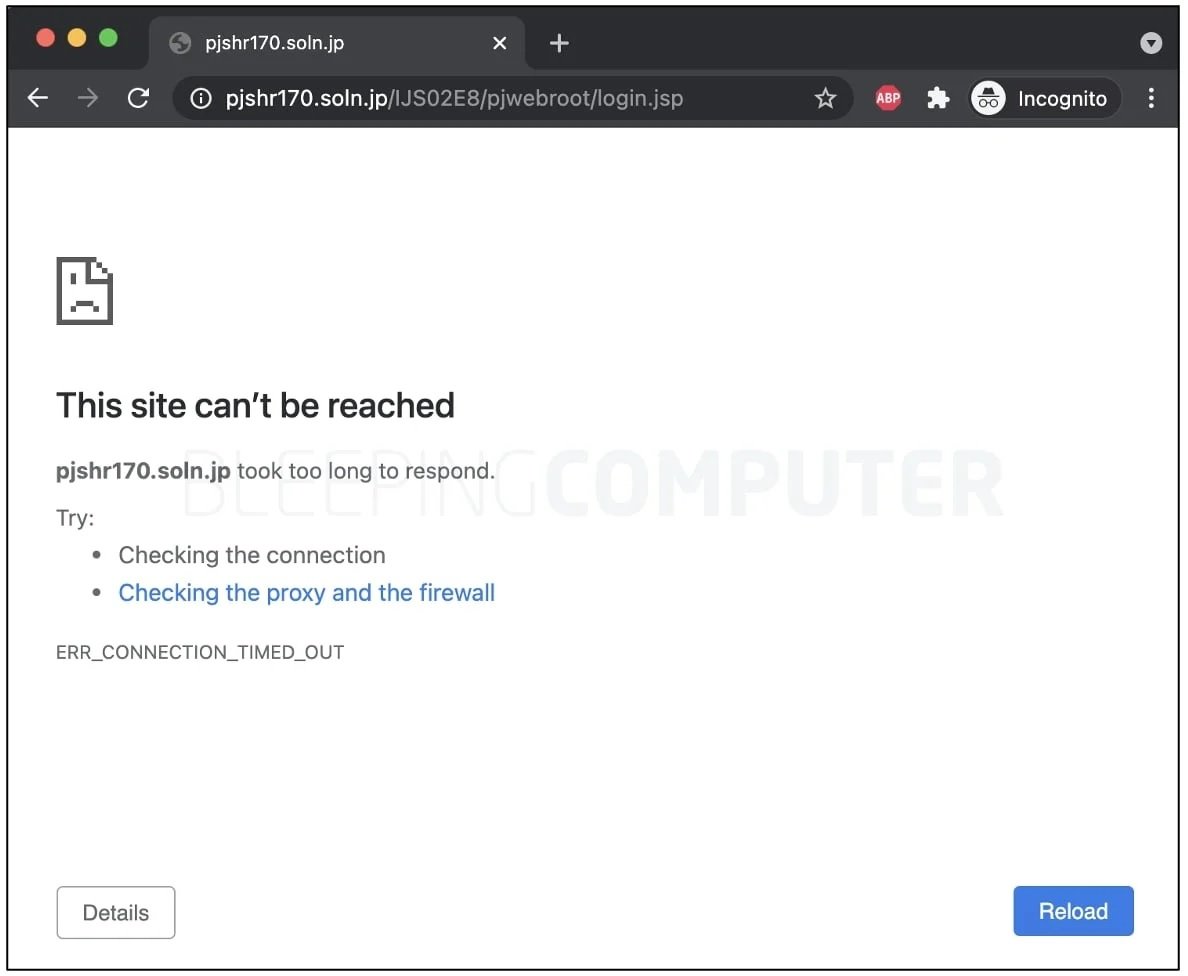
Because the ProjectWEB portal was hosted in the “soln.jp” domain, one way to check if an organization has been affected is to search for traces of the domain or URL mentioned above in your network logs. Fujitsu says it is in communication with affected authorities and customers to address the incident.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
