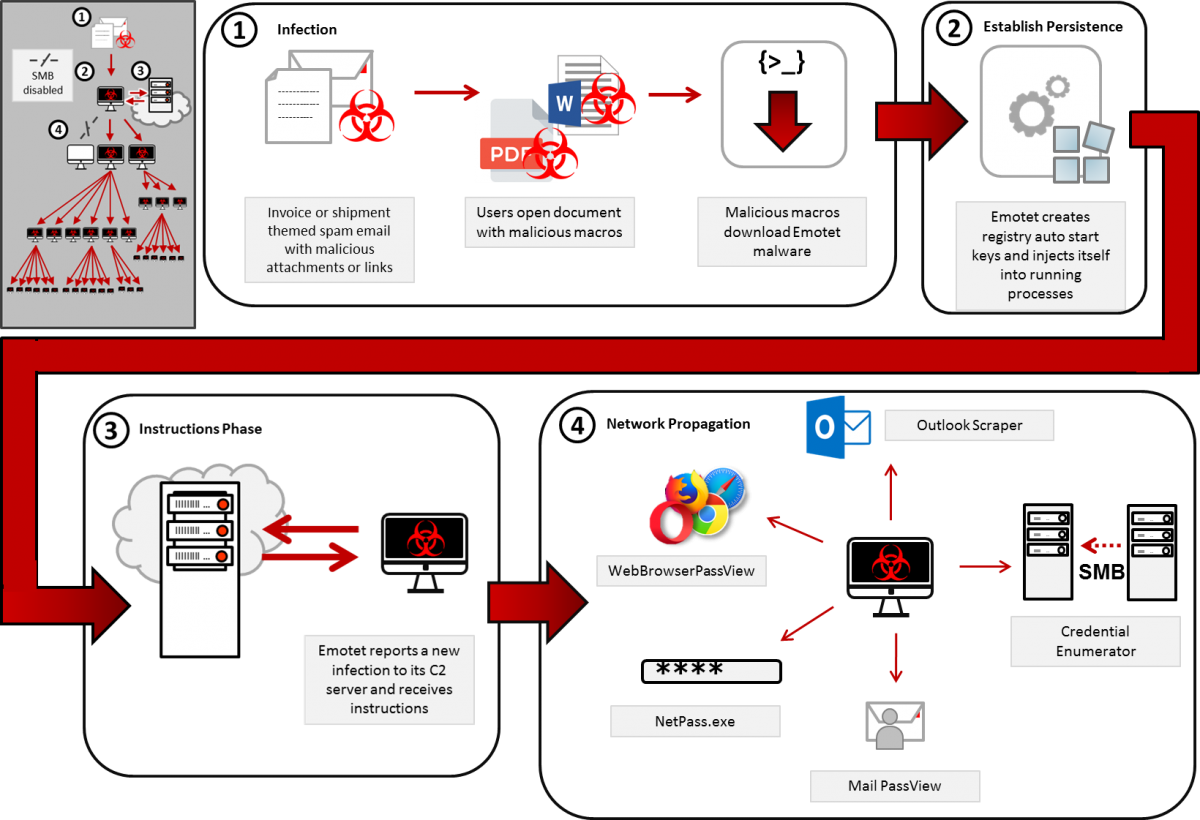
Cybersecurity specialists claim that an Emotet infection was able to shutdown an organization’s entire network just by maxing out CPUs on Windows devices, as well as bringing its Internet connection down after an unidentified employee was deceived to open a file attached to a phishing email.
In a report submitted to Microsoft, the experts mentioned: “A user received an email loaded with the Emotet malware, a variant of polymorphic virus capable of navigating through shared networks and legacy protocols, which collapsed the central networks of the target organization.” This variant of viruses managed to evade the detection of security tools, spreading through the company’s systems and causing massive disruptions across multiple services.
After entering the target system, the Emotet payload was executed on the systems of the target company, whose name was not revealed; according to the report, the complete infection of the target networks only took five days.
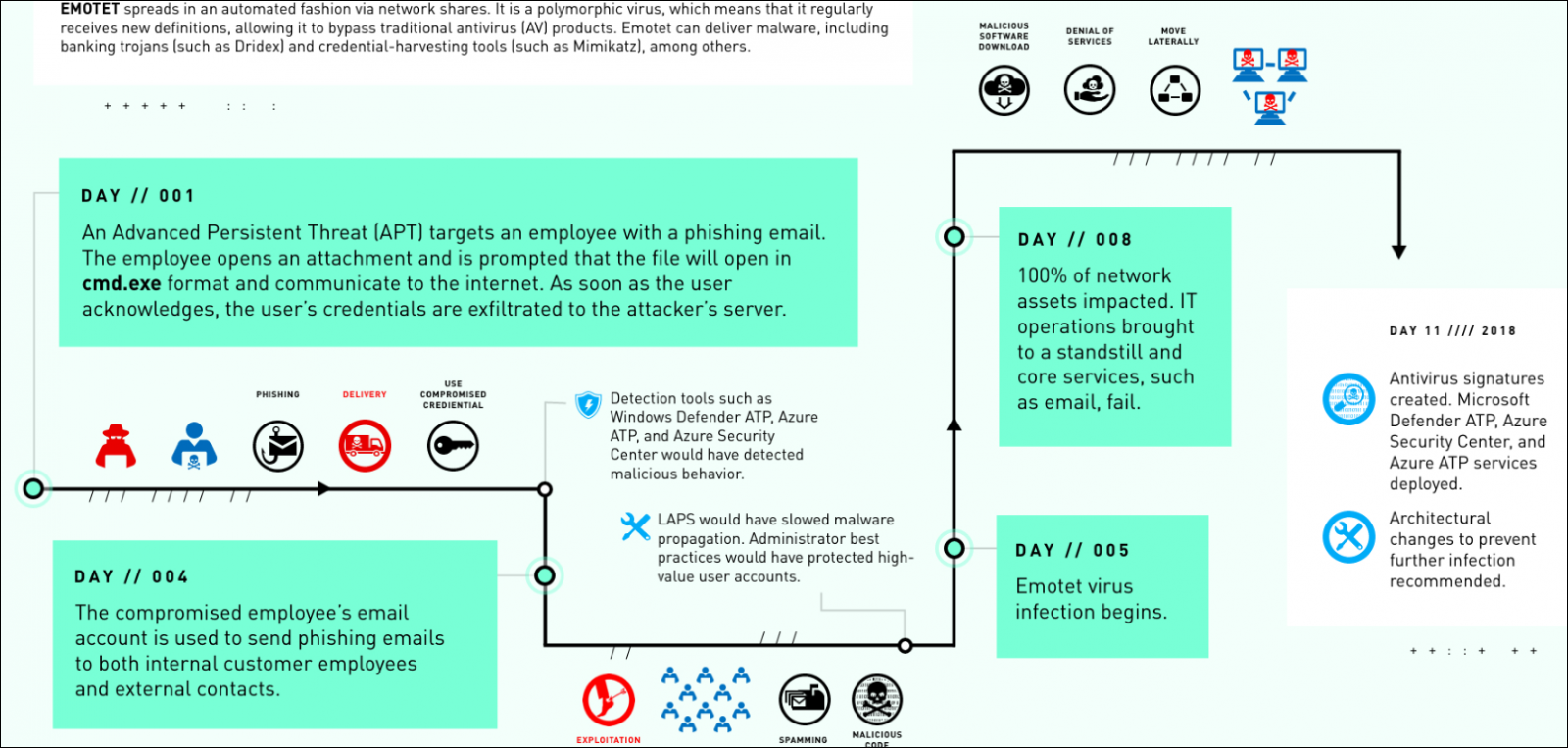
In addition, before completing the attack, hackers used the stolen login credentials to send phishing emails to other employees of the company. It is reported that the attackers also tried to contact individuals and external companies.
Malware continued to expand across the company’s networks without system administrators being able to notice the slightest hint of anomalous activity. After a full week after infection, problems finally began for the company, whose IT department had to deal with computer overheating, sudden reboots and blue screens, as Emotet occupied the company’s entire bandwidth, generating something similar to a denial of service (DDoS) condition.
This incident is also being investigated by the Microsoft Detection and Response Team (DART); Due to the features of the attack and the malware used, a potential link between this attack and the malware infection that paralyzed the systems of the city of Allentown, Pennsylvania, has even been mentioned a couple of years ago. On that occasion, Allentown authorities had to pay nearly $1 million US to restore their computer systems. As the city’s mayor reported, malware eradication cost less than $200,000 USD, although completing the recovery process increased spending by an additional $900,000 USD.
Emotet, first detected in 2014, was initially developed as a banking Trojan. However, the constant development that cybercriminal groups have made has made it an advanced malware loader, widely used to deliver malicious tools like Trickbot and multiple variants of ransomware.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
