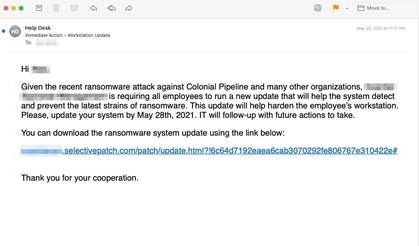
It’s been a couple of weeks since the attack on Colonial Pipeline and the cybersecurity community is still finding evidence of malicious activity related to this incident. A new report indicates that a hacking group is taking advantage of this news to deploy a phishing campaign, sending malicious emails to steal information from users interested in this and other notorious attacks.
Apparently this campaign was deployed in order to target customers and newsletter subscribers of the security firm INKY, who reported having received emails with alleged reports about the attack on the pipeline, in addition to including a supposed update of anti-ransomware system for protection against similar incidents. If users clicked on the attached links, they were redirected to a website registered with NameCheap.
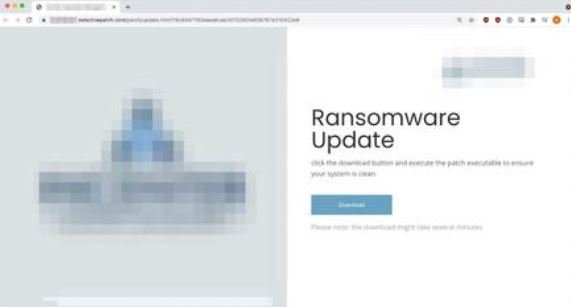
Those responsible for these attacks created legitimate-looking malicious websites, almost seamlessly copying the INKY image but adding a download button to inject a Cobalt Strike payload into the target system. This malicious tool is the second most reported security threat, according to Red Canary’s malicious activities report.
“The operators of this campaign try to abuse the growing number of ransomware attacks, offering potential victims the ability to install a supposed security update to prevent an infection. The risk increases considering that all hackers need is for the target user to click on the malware’s download button,” the report states.
This is a sophisticated attack and has apparently allowed threat actors to evade detection of some of the most sophisticated anti-spam solutions.
For security, experts recommend that IT managers in organizations that work with INKY alert their employees to the possible appearance of these phishing messages: “The success of these attacks is based on misinformation, since many employees often do not have the knowledge to identify a potential security threat. In these cases, prevention and awareness are the best security measure,” the report concludes.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
