After a data breach was revealed that compromised Audi and Volkswagen customer information, it has been confirmed that this compromised data is being sold on a dark web hacking forum. This week, a well-known user on an illegal hacking platform made a post announcing the sale of the database of these automotive firms.
Earlier this week, Volkswagen Group of America (VGoA) disclosed that its security teams detected that a vendor left customer data exposed on the internet between August 2019 and May 2021. The company acknowledged that the incident would have compromised confidential information of thousands of customers. The incident involved 3.3 million customers of Audi, Volkswagen and some authorized dealers in the U.S. and Canada.
The seller claims that the file contains more than 5 million records, of which about 4 million could belong to customers of the affected companies.
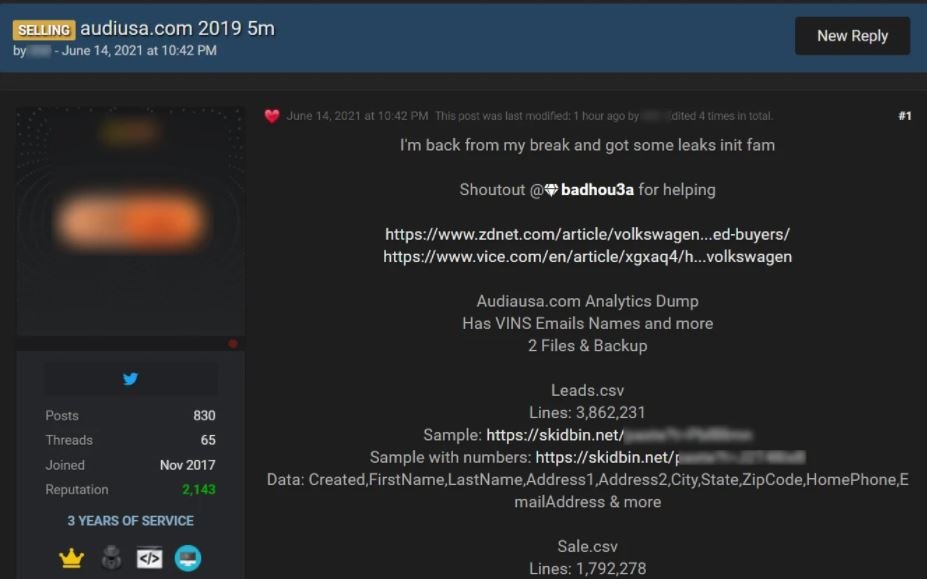
The seller also claimed that the database includes sensitive information such as full names, phone numbers and even some details about the vehicles of the affected users, although it does not store social security numbers. Vice researchers, in charge of the first report, claim that hackers would have accessed the exposed data last March after finding it in an Azure Blob container without the necessary security measures. .
Those interested in accessing this information will need to pay between $4,000 USD and $5,000 USD. The vendors previously mentioned the sale of other databases extracted from other companies, including a Virtual Private Network (VPN) services firm and multiple app developers for Android operating systems.
This hacker or group of hackers also claimed responsibility for compromising the systems of the Copy Me That recipe website.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
