Ransomware incidents remain a serious threat to individuals and organizations, especially in times of pandemic. A couple of months ago, researchers at the University of California, San Francisco (UCSF) noticed that they were unable to access some data and systems, including research on a vaccine for COVID-19. They later noticed that a hacker group encrypted their servers, demanding a ransom payment to restore access.
Threat actors reportedly demanded about $3 million in exchange for releasing the compromised information. The malicious hackers did not seem to target these labs, as the rescue negotiator mentioned that the target was “in the wrong place and time.” UCSF even hired a professional negotiator to agree payment to hackers.
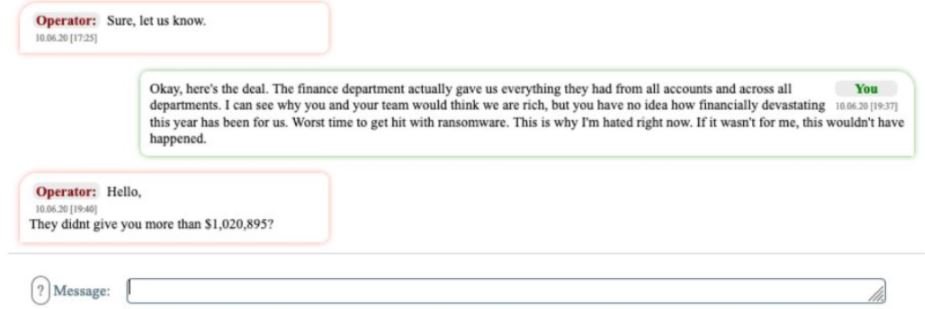
During the negotiations, conducted through a dark web platform, UCSF offered to pay $780,000, although hackers said the University could pay much more: “Keep that 780 grand to mc Donald’s; that’s a very small amount for us,” the threat actors said.
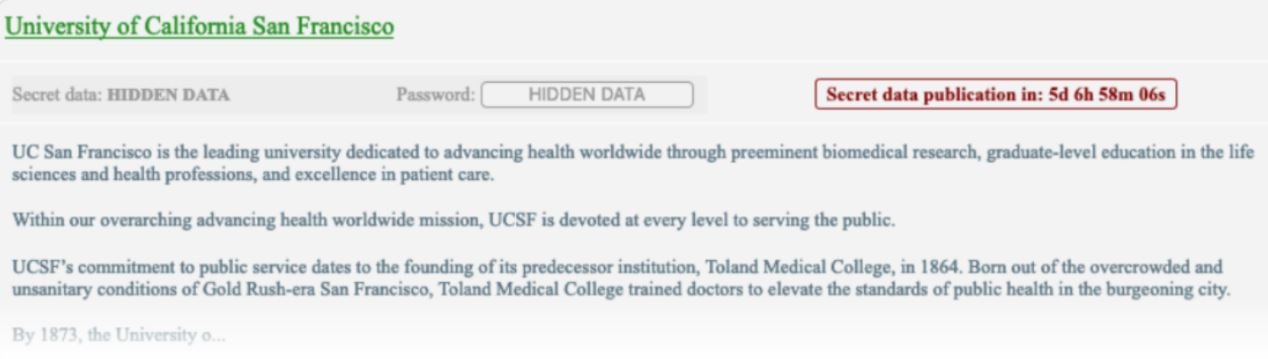
After a day of negotiations, UCSF pledged to pay a $1.02 million USD ransom, although criminals set their best bid at $1.5 million USD. Eventually, the university offered a payment of just over $1, 140,000.
After security firms and federal agencies analyzed interactions between hackers and UCSF, they concluded that these criminals appear to be members of the huge Netwalker hacking group.
Cybersecurity specialists say these kinds of incidents are on the rise, as threat actors assume that companies or individuals have much to lose. A recently released report by the Federal Bureau of Investigation (FBI) states that Chinese government-sponsored hacking groups could deploy serious attacks on universities and research centers working on a vaccine for the virus that threatens humanity.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
