A few years ago, a group of hackers managed to compromise nearly 20,000 online accounts of Dunkin’ Donuts customers using a massive credential stuffing campaign.
Cybersecurity specialists point out that credential padding is highly successful because many users of online platforms use the same password to access two or more services, facilitating the work of threat actors.
During the incident in the coffee shop chain, hackers were able to access multiple details contained in users’ point cards, for example:
- Full names
- Email address
- Dunkin’ Donuts account number
- Access key
- Account balance, only in some cases
Security reports mentioned that the compromised information was posted on hacking forums on dark web, so they could have been used to deploy phishing attacks against the company’s customers. While the incident was reported to Dunkin’ Donuts via its mobile app provider, the coffee shop chain did nothing about it.
As if that wasn’t enough, in early 2019 the company revealed a new security incident affecting its customers’ information through a credential attack. Although again the company’s executives tried to ignore the incident, this time things were different, as the state of New York decided to file a lawsuit against the company; if approved by a judge, the lawsuit will result in a $650,000 USD fine for the large donut seller.
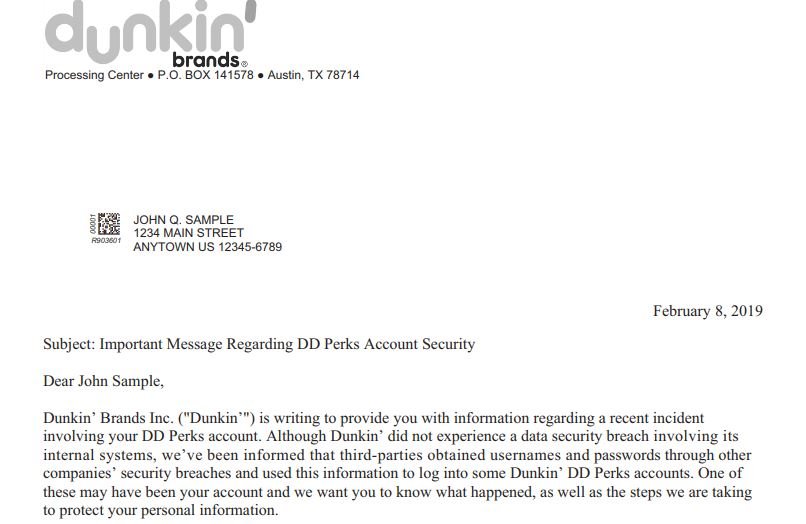
Local authorities argue that the company never notified its customers of the problem, did not reset the passwords of those affected, or implement any security mechanism to contain the attack.
Dunkin’ Donuts said: “Our IT teams voluntarily implemented the required security measures long before the New York Attorney’s Office filed the lawsuit.”
Subsequently, a company spokesperson mentioned that no authority had required them to implement security mechanisms, although a commitment to the safety of their customers and the prevention of security incidents spurred this initiative.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
