Drizly, an alcohol delivery start-up, has just notified its customers that it suffered a data breach that could have compromised your personal information.
Through an email sent to its customers and filtered to various media outlets, the company revealed that some of his personal records were obtained by a threat actor; among the data committed are
- Email addresses
- Dates of birth
- Passwords encrypted with bcrypt
- Delivery address, in some cases
It is mentioned that around 2.5 million users would have been affected.
The TechCrunch platform obtained a sample of the compromised data, including some accounts from Drizly’s internal staff. When verifying data with public records, it was concluded that some compromised user profiles also include phone numbers, IP addresses, location data, and more.
The company did not specify when the incident occurred or the exact number of accounts affected, although it advised all its users to reset their passwords to avoid subsequent attacks. In this regard, a spokesman for Drizly said: “About 2.5 million accounts were affected, including the homes of about 2% of affected users.” The spokesperson concluded by mentioning that users’ financial information was not compromised.
Despite these statements, the dark web forum where the information was posted ensures otherwise.
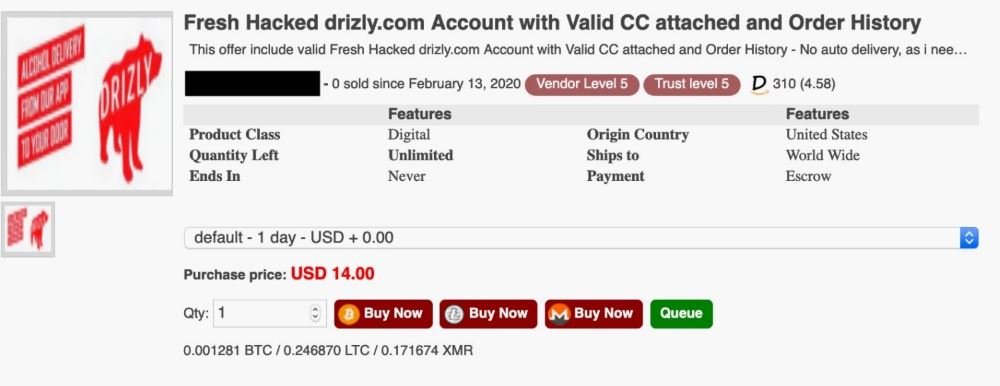
The ad mentions that Drizly’s hacked accounts are on sale for less than $15. Although sellers don’t mention when the data breach occurred, the ad appears to have been released last February. The seller does not provide a sample of the compromised information, although it states that this database includes valid payment card numbers.
Along with Minibar and Delivery.com, Drizly is one of the leading alcoholic beverage delivery services in the United States and Canada, raising more than 60 million since its launch.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
