The leak of a database exposed the personal data of around 200,000 individuals who appear to be involved in a fake review scheme on Amazon, usually employed by vendors of dubious reputation on the platform.
While there is no one-size-called method for these fraudulent schemes, experts mention that such an operation usually involves paying certain people to leave positive reviews on low-quality products, increasing the seller’s reputation and attracting unsuspecting users.
Recently, a Safety Detectives security team found an unprotected Elasticsearh implementation that stored about 7GB of sensitive information, including 13 million records apparently linked to the Positive Review Scam on Amazon. While it is not known who is responsible for the operation of the compromised server, experts believe that it could have been operated from China.
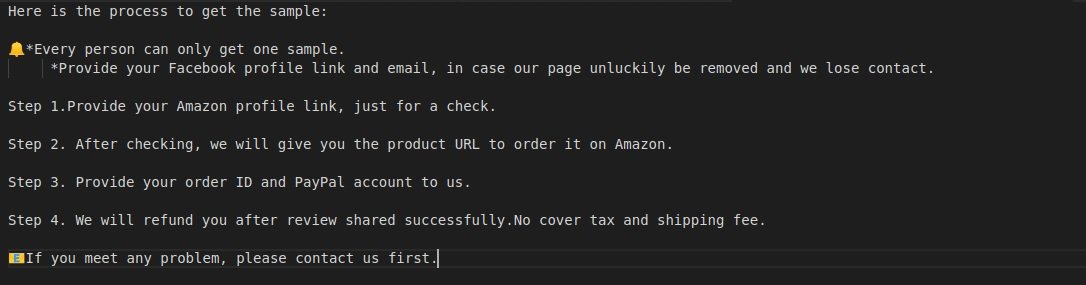
As mentioned at the beginning of this article, the database stored information of between 200 thousand and 250 thousand Amazon users and vendors allegedly affiliated with the fraudulent scheme. The records contained confidential details such as
- Full names
- Email addresses
- Addresses of PayPal
- Numbers associated with WhatsApp and Telegram
According to experts, this leak implies that at least 200,000 individuals are involved in these questionable activities. Additional documents revealed details of how fraud operators are operating, including sending links to items they wish to sell and receiving high reviews. Subsequently other members of the scheme left a positive review and purchased the item, so they would receive a kind of refund that would allow them to keep the item unpaid, leaving a high rating on the seller’s page. Because Amazon doesn’t manage these kinds of operations, it’s easy to fool the platform by giving the impression of organic growth for the seller.
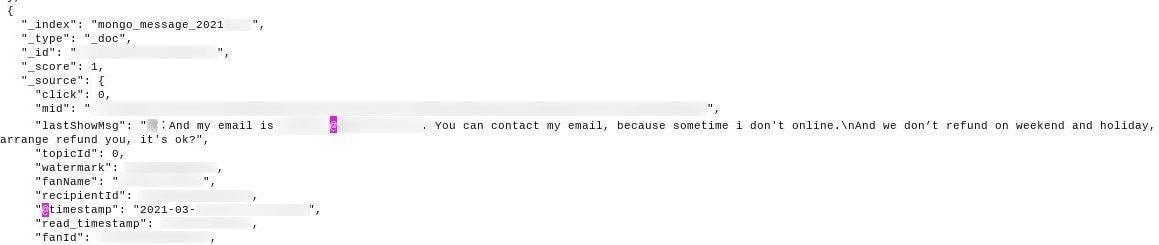
Amazon does not allow sellers to review their own products or offer other users monetary or in-kind rewards in exchange for positive reviews. However, it is obvious that low-reputational sellers do not hesitate to subscribe to these kinds of fraudulent schemes to try to stay competitive on the world’s largest sales platform. Perhaps the obvious solution is for Amazon to implement more effective mechanisms to try to detect these schemas.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
