A cybersecurity report mentions that a malicious hacker is selling a database storing confidential registers belonging to over 170 million Pakistani citizens in a dark web forum. According to the report, this is a data compilation of multiple telecommunication companies operating in Pakistan, including Ufone, Telenor, Warid and Zong.
“Hi, I’m selling a database leaked to telecom networks of Pakistan. I have the details of about 176 million phone services subscribers updated in 2020. Interested users can contact me for further details”, mentions the threat actors’ post.
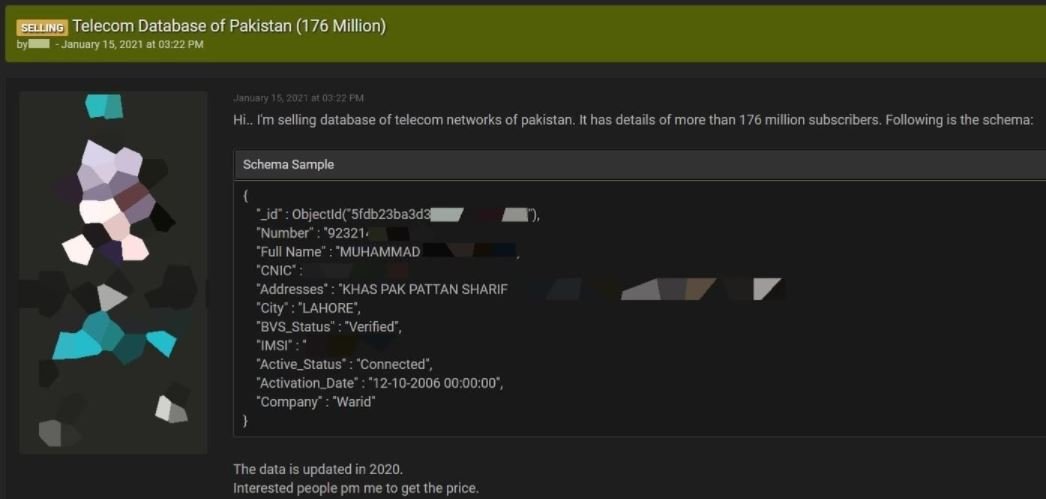
A sample of the compromised information obtained by cybersecurity specialists impersonating potential buyers, the database includes details such as:
- Users’ full names
- Addresses
- Phone numbers
- Users’ IMSI numbers
- Account details
- Biometric authentication data
- National ID card number
- Phone operator
The specialists also mentioned that this database may not have been stolen from a telecomm company; instead, they theorize this leakage could be the result of illegal data scraping campaigns performed both by private companies and by Pakistani government agencies. This is not the first time such an incident is reported.
Experts think that, in case this leakage is legitimate, this could lead to malicious campaigns targeting Pakistani citizens: “Threat actors can deploy SIM swap attacks, phishing campaigns and identity theft frauds, while hacking groups sponsored by national states could deploy complex cyberattack campaigns.
The cybersecurity community considers this kind of incidents are no surprises; last year, a malicious hacking group leaked confidential details belonging to at least 44 million Mobilink clients, posting the compromised information at multiple dark web forums. A few days later, a security report revealed the finding of a powerful Android spyware disguised as multiple Pakistani government mobile apps to spy on unaware users, mainly political dissidents and activists. Pakistani authorities have received multiple information requests on these allegationS, but no answer has been issued.
This incident poses more questions than answers for local cybersecurity experts, as they even consider it to represent a potential breach of the security of government institutions. The most worrying thing about the case is the systematic silence that the authorities put into practice regarding these kinds of incidents.
For further reports on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses fell free to visit the International Institute of Cyber Security (IICS) websites, as well as the official platforms of technology companies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
