Cybersecurity specialists report that a hacker is selling real-time access to a single-use password system, allowing cybercriminals to access Facebook, Twitter, Google, Amazon, Microsoft, Signal, Telegram accounts, among many others without having to obtain multi-factor authentication codes.
This report should be taken seriously, as a related attack could engage billions of users. In turn, cybersecurity experts point out that this is the consequence of using servers that handle OTP requests from online service users.
The first reports on this hacker were published by researcher Rajshekhar Rajaharia, who mentions that the hacker offers 50 GB of data extracted from multiple sources and webshell access to the OTP generating platform. The seller asks for about $5,000 USD in cryptocurrency, although Rajaharia notes that initially the hacker planned to sell this information for about $18,000 USD.
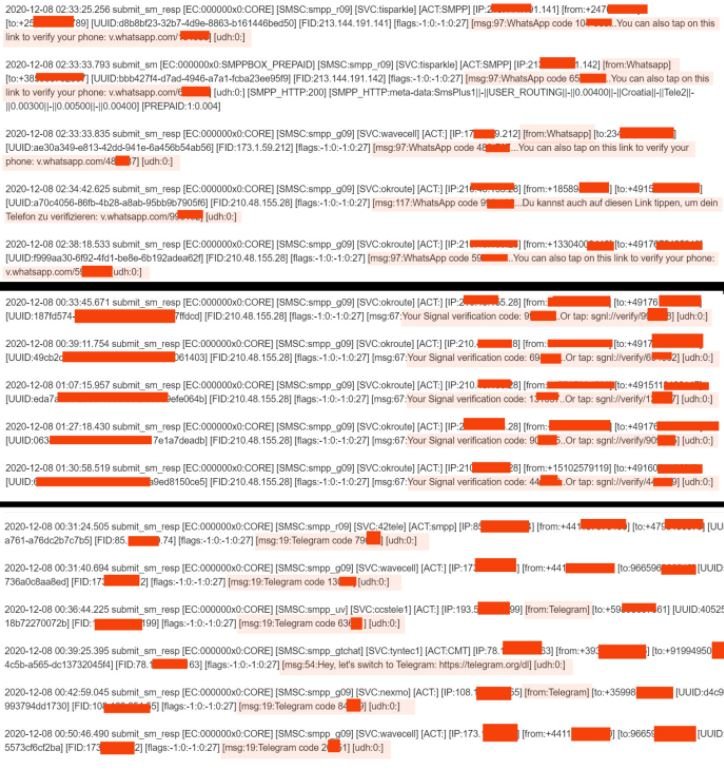
The researcher was able to access some of the samples shared by the hacker, allowing him to confirm the presence of some one-time codes in the database. It should be noted that not necessarily all tokens can remain valid, although this does not seriously detract from the incident.
The leak also includes other data such as phone numbers, email addresses, SMPP details, among others. In addition, although the seller deleted its publication from the platform on dark web the database is still on sale on Telegram.
Finally Rajaharia notes that this can be a massive blow to online services: “Multi-factor authentication was the ultimate defense mechanism to protect our online transactions; if these defenses are violated, the chances of facing a massive attack could increase considerably.”
The company responsible for the OTP system sent a statement to the operators of potentially compromised platforms stating that their systems have not been compromised, although they mention working with a group of cybersecurity experts to analyze reports and prevent any incidents.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
