A severe cybersecurity incident has been reported by a group of specialists. According to a recent investigation, the Telmate telecommunications service presented a database containing tens of millions of call logs, text messages and personal details about thousands of prisoners in the United States. Telmate is a service with special security measures used by inmates in the U.S. to stay connected with family and friends.
This database was found online, fully exposed and within reach of any user who knows where to look, as it did not have a password or some other protection measure.
On August 13, security researcher Bob Diachenko detected the exposed database while analyzing another incident, so he immediately notified Global Tel Link, the company that owns the Telmate service. While Global Tel Link security teams responded immediately to Diachenko’s report and secured the database, unauthorized access may have occurred before the expert from Comparitech detected the exposed information.
Telmate’s main product is GettingOut, a platform (including apps for iOS and Android) that provides monitored telecommunications for inmates and their families through voice calls, text messages, photos, voicemail and even video calls.
After analyzing a sample of the information presented, Diachenko concluded that the database presented could contain information from all prisons where this technology is used, as GTL is the largest provider of prisoner communication services in the U.S., hosting nearly half of this market, specialists mention.
Once the database was secured, Global Tel Link issued a statement: “We closed some servers as a security measure after detecting a vulnerability in the data system due to the actions of some vendors. The vulnerability was quickly fixed, and additional measures were implemented.” The company also assured users that their health information, passwords or financial data were not compromised.
In his research, Diachenko mentions that the database was indexed to the BinaryEdge search engine in mid-August, although it is likely that it has remained exposed before. As mentioned in previous paragraphs, the leak was notified to the company, which referred to the database a few hours later. With regard to the data presented, the records appear to come from the electronic tablets used for the GettingOut service, which are provided to inmates by the administration of their respective prisons. The database contained three different indexes at the time of detection:
- 227, 770, 157 message logs
- 11, 210, 948 inmate records
- 78, 885 administrative records with login details for Telmate’s control panel
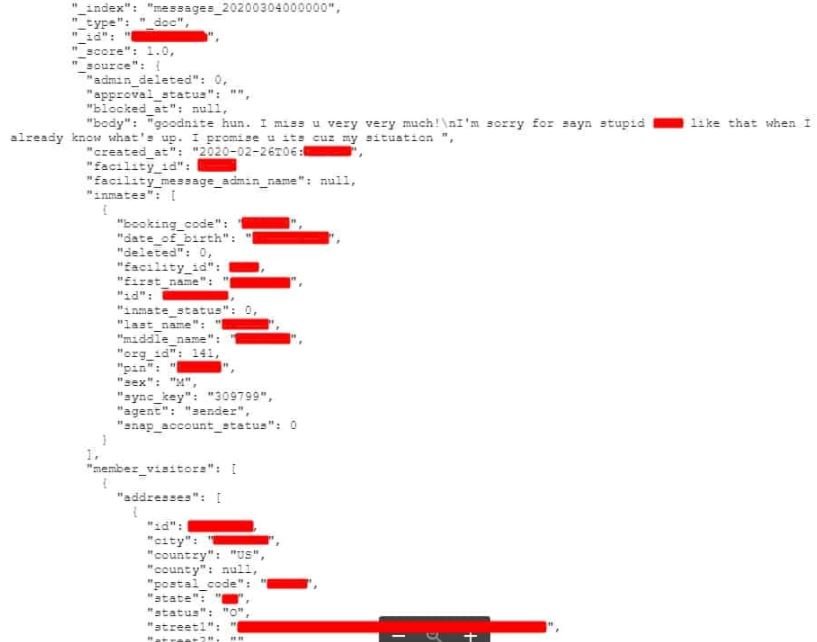
The text messages presented contain all kinds of conversations and multiple details about prisoners and their personal lives, as well as requests for transfers, legal assistance and other issues related to their life in prison. Diachenko also highlights the large amount of metadata contained in the messages exposed, since in each you can find details such as:
- Text message content
- Time mark
- Inmate information
- Date of birth
- Full name
- Sex
- Recipient of the message
- Full name
- Email address
- Home
- Message status (this field refers to whether the message was sent or whether prison staff decided to block it)
On the other hand, the prisoners’ records also contained multiple details such as:
- Full name
- Crime committed
- Prison where the sentence is served
- Account balance (used to cover Telmate service fees)
No matter whether it is information from individuals serving prison sentences, exposing this data can be dangerous, mainly for the friends and family of inmates, who could be victims of crimes such as extortion, fraud, phishing campaigns, among other malicious practices.
Global Tel Link has not announced what steps it will take to address this incident, in addition to securing the exposed database. At the moment it is only known that the company will be notifying Telmate users directly whose information may have been exposed, not forgetting that the investigation has not been completed.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
