Information security specialists from CyberNews revealed the finding of an online storage implementation allegedly owned by digital marketing company View Media containing about 40 million records of U.S. citizens.
The leak occurred due to an unprotected Amazon Web Services (AWS) server, which allowed any user to access the information. Among the data presented are details such as:
- Full names
- Email addresses
- Phone numbers
- Addresses and postcodes
Amazon detected the information leak, so the bucket was closed on July 29.
This AWS bucket contained 5,302 files, including 700 job declaration documents for advertising campaigns in PDF format and 59 files were 38, 765, 297 records of U.S. citizens were stored; because some records doubled, the number of unique records is closer to 23 million.
The following are some samples of the logs stored in this online deployment:

As can be seen, these records date back to 2018 and 2019:
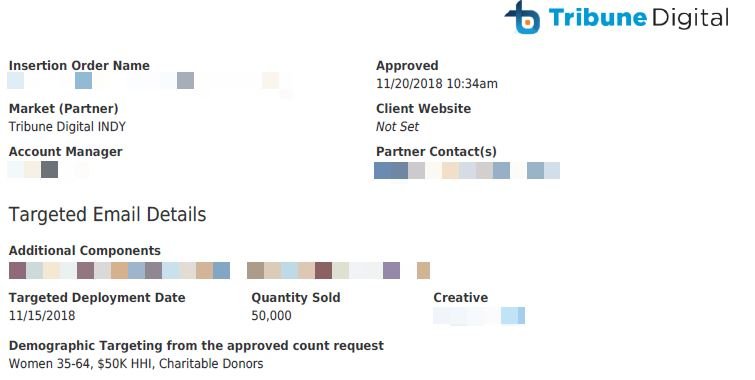
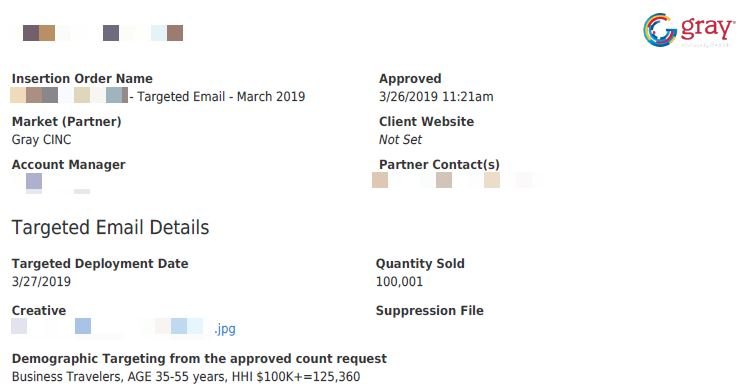
There is no certainty as to how long the database remained exposed; although experts believe that exposure time could be extended by months. It’s relatively easy for any user to find an exposed AWS deployment, so there’s a high chance that someone has accessed this database.
Citizens whose information was compromised during this incident are exposed to multiple malicious scenarios, for example:
- A threat actor could use exposed names, email addresses and phone numbers to deploy all kinds of fraudulent activities
- Simple contact details may be enough to deploy massive spam, phishing and social engineering campaigns
- A well-organized group of threat actors could use this data in combination with information collected in other incidents to perform complex fraud
View Media was notified in connection with this finding, although the marketing company has not made any statements in this regard. Amazon also made no mention of the incident after the bucket was closed.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
