Cybercriminal groups have demonstrated great adaptability to the context of the pandemic and the use of remote communication tools, as they have now begun using platforms such as Zoom to deploy an ambitious sextortion campaign. Bitdefender experts detected this trend targeting nearly 250,000 Zoom users worldwide, who received a message that carries the topic: “About Zoom’s Conference Call”.
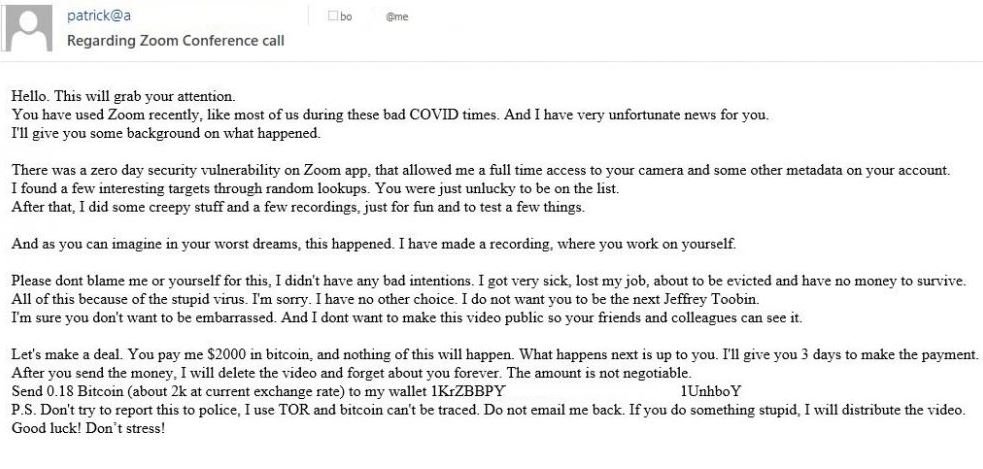
“I have some very unfortunate news for you. There was a zero-day vulnerability in the Zoom app that allowed me full-time access to your camera and some other account metadata,” the scammers mention. “I found some interesting goals through random searches. You were unlucky enough to be on the list.”
Although it’s just an attempt at fraud, criminals seem to be aware of the multiple security vulnerabilities reported on platforms like Zoom, so they know this is a concern for thousands of users who have turned to this platform to work, attend classes or stay in touch with their loved ones.
After raising the problem, the scammers finally reveal their intentions: “I made some recordings of you in intimate moments,” it can be read in the message. This appears to be a typical sextortion campaign, as there is no indication that threat actors may have actually accessed sensitive user information.
“Please don’t blame me or you for this, for it’s all the virus’s fault. I don’t want to make these images public, and I’m sure you don’t want your friends and colleagues to see you like this,” the scammers continue.
Finally, the extortionists set a three-day deadline for victims to make a payment of $2,000 in Bitcoin; otherwise, the criminals threaten to disclose the alleged video among the victim’s contacts. This attack variant has proven to be a high degree of success in recent years, as it plays with victims emotionally, making it difficult for them to make the right decisions in the face of these attacks.
Still, needless to say, threat actors don’t really have access to the Zoom account or users’ files. The success of these attacks depends entirely on the victims, so it is worth being cautious.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
