A team of cybersecurity specialists has revealed the finding of a new vulnerability presenting the DNS protocol that could be exploited to launch denial of service (DDoS) attacks with unusual power. This attack variant, known as NXNSAttack, relies on the DNS delegation mechanism to force DNS resolvers to generate more queries on compromised servers, which could lead to service disruptions similar to those generated by larger botnets.
In its report, the team of researchers mentions: “We show that the number of DNS messages exchanged during the conventional resolution process could be much higher in real-world scenarios, due to the proactive resolution of the IP addresses of the name servers. This inefficiency becomes a problem in processing requests, which could lead to a devastating attack against one or both recursive resolutions and servers.”
What is the attack?
A recursive DNS lookup occurs when a DNS server communicates with multiple authorized servers in a hierarchical sequence to locate an IP address associated with a domain and return it to the client. This resolution usually begins with DNS resolution controlled by Internet service providers or public DNS servers, such as Cloudflare or Google, depending on system configurations. Resolution passes the request to an authorized DNS name server if it cannot locate the IP address of a particular domain name.
Resolution passes the request to an authorized DNS server if it cannot locate the IP address of a particular domain name. But if the first authorized DNS server also does not contain the desired records, it returns the delegation message with addresses to the following authorized servers that the DNS resolver can query.
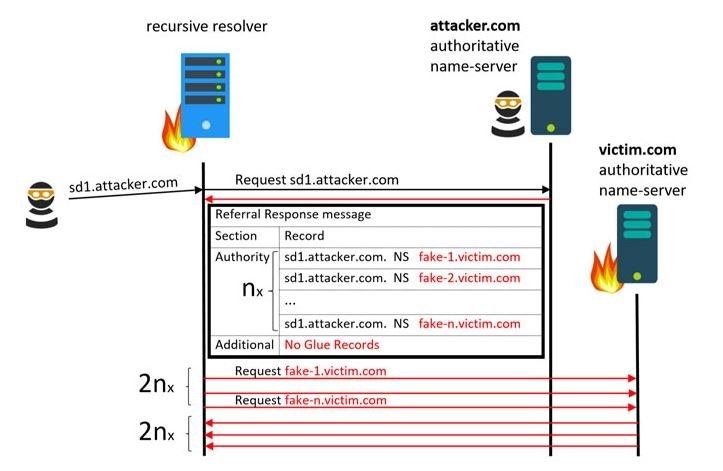
This hierarchical process continues until the DNS resolver reaches the correct authorized server that provides the IP address of the domain, allowing the user to access the desired website. Researchers found that these large unwanted overheads can be exploited to trick recursive resolvers into sending a large number of packets to a target domain instead of sending them to legitimate servers.
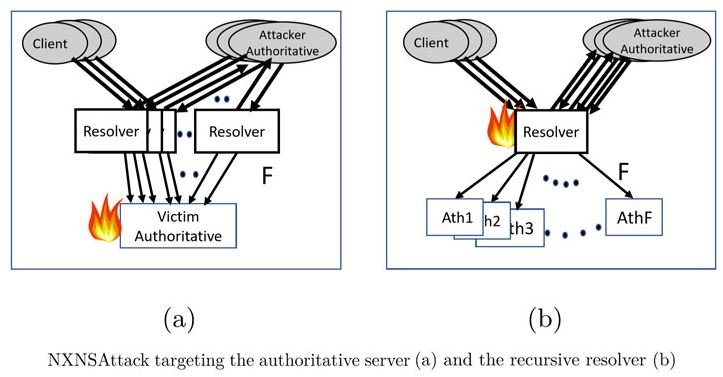
In this attack you can increase the number of packets exchanged by the recursive resolver by more than 600 times, overwhelming not only those who resolve DNS with more requests they can handle, but also floods the target domain with malicious requests. Using a botnet (like Mirai) could further scale up the attack, experts note.
It is strongly recommended that network administrators running their own DNS servers update their DNS resolution software to the latest available version to mitigate the risk of exploitation.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
