For some time several security firms and ethical hackers have been on the trail of a famous hacker identified as Fxmsp, who broke into the networks of at least three cybersecurity providers last year. After some experts tracked the hacker’s companies in clandestine forums, they detected network intrusions associated with their mode of operation, revealing their real identity.
This hacker became widely known nearly a year ago, when cybersecurity company Advanced Intelligence revealed some reports about its multiple attempts to sell a set of network accesses from Symantec, Trend Micro, among other companies. Fxmsp was asking for about $300, 000 USD in exchange for this information.
The attacker and his accomplice went unnoticed by the public shortly after receiving too much media attention, though cybersecurity experts believe it has never ceased to be active. Group-IB researchers analyzed Fxmsp’s activity on public forums where he advertised his businesses, and assessed that the hacker compromised the networks of at least 135 companies in 44 different countries.
Fxmsp has attacked organizations of all kinds, including small and medium-sized companies, government institutions, banks and large companies, including some on the prestigious Fortune 500 list. Investigators believe the hacker would have earned up to $1.5 million in a three-year term.
Although it is a considerable figure, the investigators believe that the hacker could have earned a lot more money, as much of the information he put up for sale did not have a published price, so the payment should be negotiated directly with the criminal. Shortly before disappearing from radar at the end of 2019, the hacker carried out one last attack on an electric company in Europe.
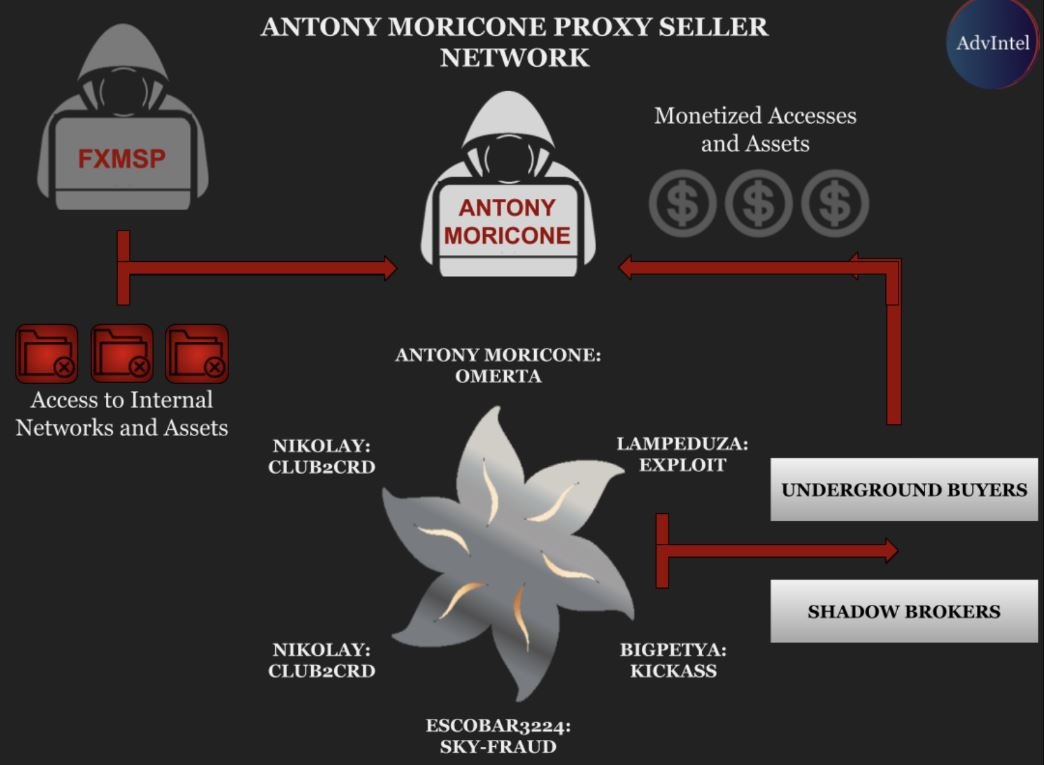
Fxsmp-linked operations are so complex that researchers doubt that it is a single individual. Yelisey Boguslavskiy, from the Advanced Intelligence research team, believes that this Fxsmp is part of the GPTitan group, made up of multiple hackers dedicated to data theft on high-profile networks.
Experts say that, in turn, GPTitan is supported by two cybercriminal groups based in the United States and China. The joint work of all these hackers would have allowed the networks of the three affected cybersecurity firms to be compromised. Researchers believe Fxmsp stopped acting on its own and has joined some international hacking group.
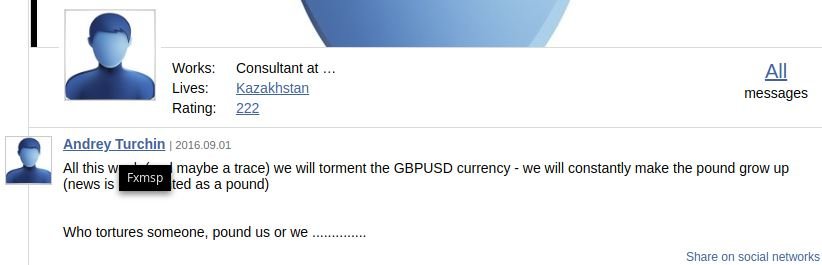
Researchers also revealed in a report what the identity behind Fxmsp may be. According to the traces collected, the real name of the hacker is Andrey Turchin, possibly originally from Kazakhstan). Security firms like BleepingComputer agree on this data.
According to anonymous reports, Andrey would have already been arrested by Kazakhstan’s police, although that has not been confirmed.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
