A couple of days ago it was confirmed that meat-producing giant JBS suffered a ransomware attack that completely paralyzed operations at some of its plants. Although no further details were added at the time, the Federal Bureau of Investigation (FBI) has officially confirmed that the attack was perpetrated by the operators of the REvil ransomware, also known as Sodinokibi.
“After analyzing the characteristics of this attack, we have decided to attribute it to REvil (Sodinokibi). We will be working hard and in conjunction with the affected company to bring the offenders to justice,” the investigation agency’s brief statement said. “We will continue to work so that cybercriminal activities do not go unpunished,” the message adds.
While not many details about the JBS incident are yet known, it is a fact that ransomware attacks have increased disproportionately over the most recent months. Just a week ago, the operators of the DarkSide ransomware claimed responsibility for the attack on Colonial Pipeline, the most important pipeline in the U.S., causing the temporary interruption of some critical operations.
A few days after the colonial pipeline attack was confirmed, Ireland’s public health system also formed a Conti ransomware infection, which could put critical patients at risk.
Because the cybersecurity community believes that the vast majority of these attacks are deployed from Russian territory, so Jen Psaki, press secretary of the U.S. government, mentions that President Joe Biden will engage in talks with Russian President Vladimir Putin regarding these attacks. It should be mentioned that this does not mean that the hackers behind these attacks are sponsored by the Russian government.
REvil is operated by a core group of Russian threat actors who recruit affiliates or partners who breach corporate networks, steal their data and encrypt their devices, in a practice known as ransomware as a service (RaaS). The profits made by these malicious campaigns are divided between malware developers and attack operators.
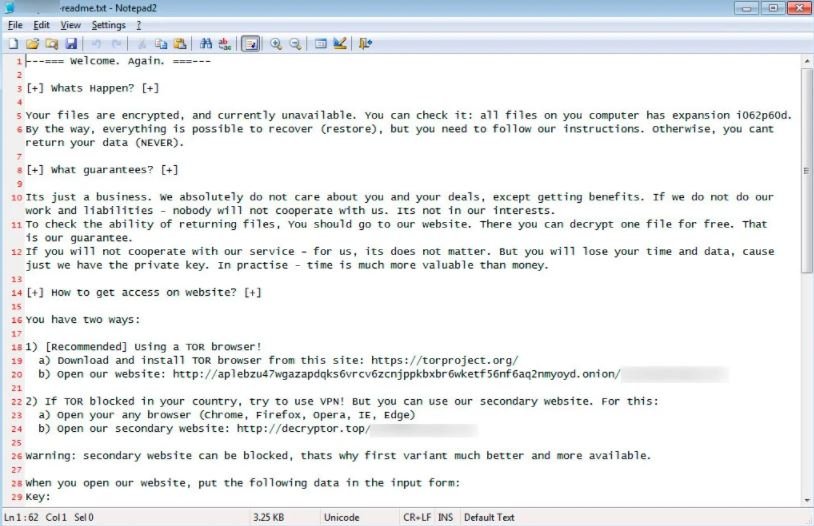
REvil was first detected in early 2019 as a suspected variant of the GandCrab ransomware, which shut down its operations for good after drawing the attention of investigative agencies. Traders claim to have earned more than $100 million USD over the past year.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
