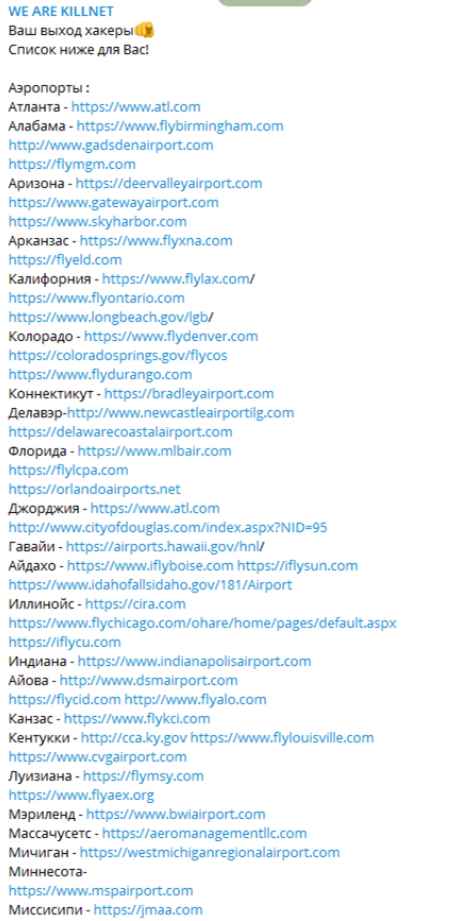
A widespread campaign of distributed denial-of-service (DDoS) assaults, in which servers were saturated with web traffic to take domains offline, impacted the websites of major US airports. Along with other airports in Florida, Colorado, Arizona, Kentucky, Mississippi, and Hawaii, the victims include Los Angeles International Airport (LAX), Hartsfield-Jackson Atlanta International Airport (ATL), Chicago O’Hare International Airport (ORD), and others. The DDoS attacks caused the websites of several airports to be either intermittently down for many hours or slow to react. They didn’t directly affect how the airport operated.
The Transportation Security Administration and the FBI were informed about the occurrence by certain airport administrations.
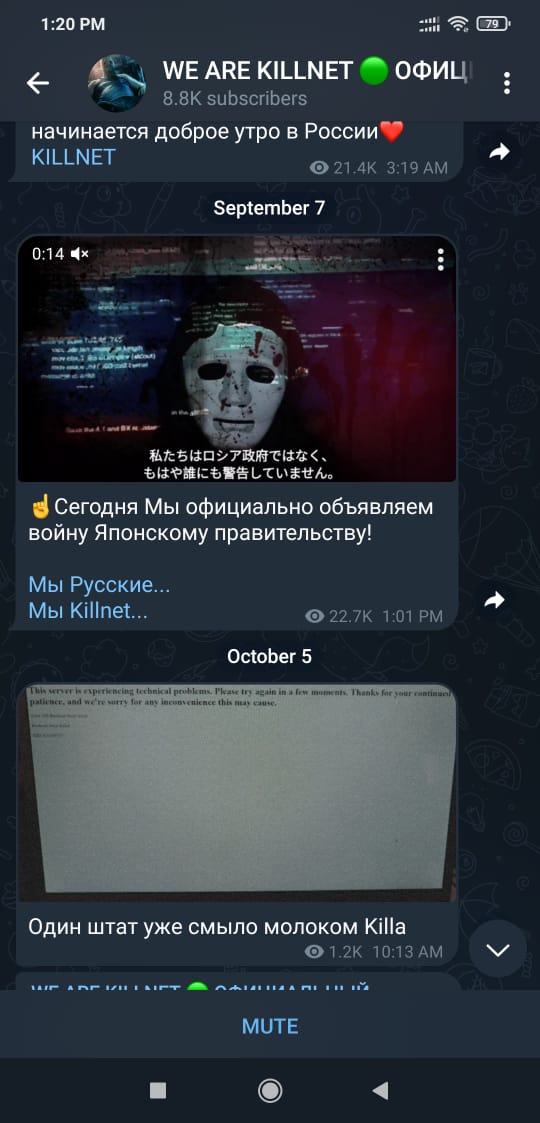
On a Telegram channel, the pro-Russian hacktivist group “KillNet” claimed responsibility for the attack and named 14 targeted domains. This kind of attack has already been utilized by KillNet. According to a government cybersecurity alert, they took down a US airport’s website in March 2022 as revenge for US backing for Ukraine.
Last week Killnet announced that it intends to cause chaos on official US websites. State and federal websites are listed among the targets in a tweet with screenshots of the activity, which is headlined “USA OFFLINE: F**K NATO . When the news originally emerged, several of the stories in the US media were criticized by security researchers since they failed to indicate that the hack only affected the websites for the airports.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
