A recent security report mentions that operators of the DopplePaymer ransomware variant have just leaked a massive database allegedly belonging to the Illinois Attorney General’s Office because officials refused to pay the ransom demanded by hackers. The information presented includes all kinds of confidential court records, including documents that do not appear in public records.
According to the report, the files were posted on a dark web hacking forum managed by the ransomware operators. The leak includes personal information about some inmates in state prisons, as well as their complaints and permits, among other information.
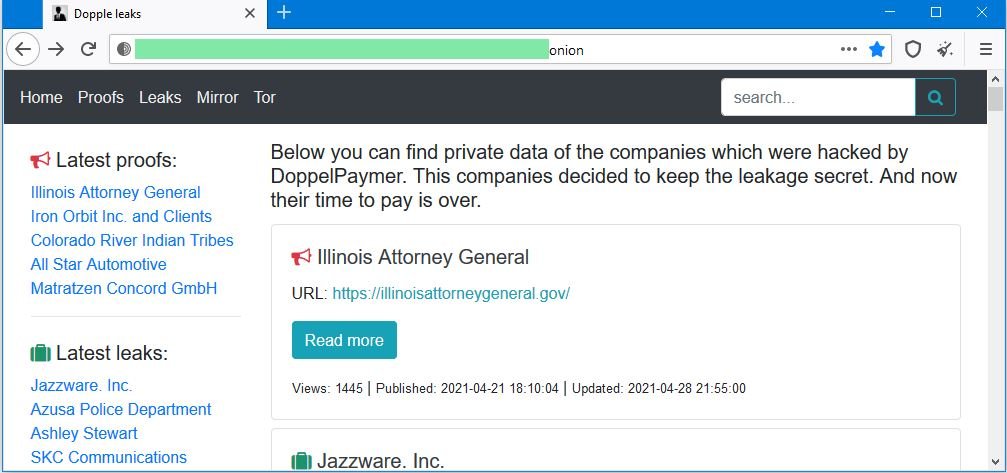
Investigators believe the attack would have occurred on the night of Saturday, April 10, although the incident was reported to the appropriate authorities until April 13; the notification only mentions that the office network was compromised, although officials did not mention anything about the ransomware attack. The type of attack was revealed until April 21, when DopplePaymer hackers attributed the attack began leaking some samples of the compromised information.
As mentioned at the beginning, after negotiations stop advancing the hackers began publishing larger amounts of information. So far nothing is known about the reasons why the bailout negotiation failed.
In this regard, cybersecurity specialists with experience in negotiations with cybercriminals mention that it is common for negotiations with ransomware trading groups to fail due to possible legal implications, as negotiating with such groups can bring problems with the U.S. Treasury Department.
Recently the U.S. government listed EvilCorp as a sanctionable cybercriminal group and, because DopplePaymer was created by this hacking group, any payment or transaction to its accounts is prohibited for any entity in the U.S. In some extraordinary cases, the Treasury Department may authorize exceptions; although it is unknown whether this will be the case.
Several members of the cybersecurity community have tried to contact a representative of the Illinois Attorney General’s office, although they have not yet obtained an official response.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
