Ransomware is one of the most dangerous malware variants that can infect a vulnerable system. When this attack manages to bypass our security measures, all stored files will be encrypted and can even be lost for good; to prevent so, affected users should pay a ransom in cryptocurrency, thus hackers will grant victims access to decryption keys and recover access to their affected resources.
These attacks are usually blocked by most security solutions, but sometimes hackers succeed and complete their plans. Besides, paying a ransom is not always the right option, because if we cannot prove that we are the ones who have paid, then there is no way to get proof of payment to the hacker. And even if the payment works, it is up to the attacker to give the key to decrypt the files.
MalwareHunterTeam specialists have discovered a new ransomware variant called Black Eye created by hackers from “GHOST CYBER TEAM”. When the malware enters a computer, it encrypts all the files, and leaves a text file on the desktop with instructions for retrieving the information. In that text file usually is a Bitcoin address to which to send the ransom, as well as an email to send the proof of payment.
The unusual thing about this campaign is that the attackers do not ask solely for money as a ransom. Instead, hackers ask affected users to subscribe to a YouTube channel and post comments on most videos.
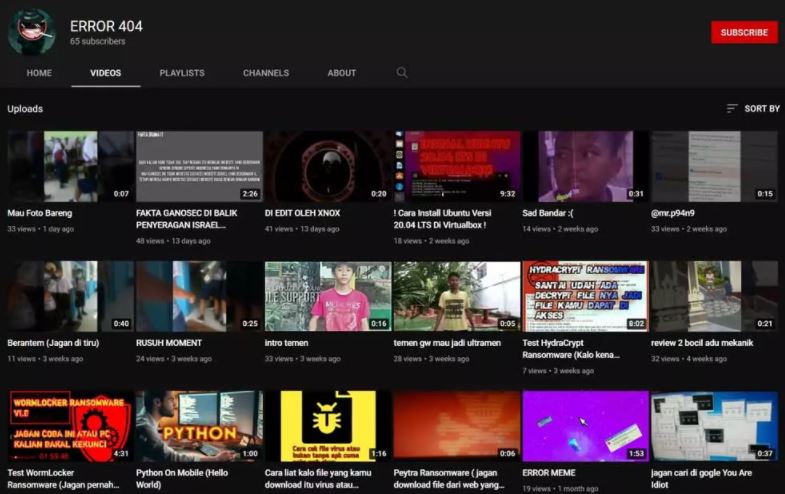
By performing these interactions, the attackers will hand over the decryption keys.
The problem is that there is no way to contact the hackers to prove that the comments have been posted, plus the videos are in Indonesian, which complicates communication between hackers and victims. Although it seems like a joke, this is a real threat. Besides, this attack only infects one device, so it does not spread to others connected on the same local network. So far, it does not seem that they have been too successful, since they only have 65 subscribers, and the videos of the channel do not have comments.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
