Microsoft Exchange servers had a vulnerability of CVE-2020-0688 and developers already resolved this issue two weeks before. But hackers are still scanning unpatched Microsoft Exchange Server across the internet to exploit.
The issues is about the Exchange Control Panel component, in creating a unique cryptographic key during installation. Due to this, hackers are searching the unpatched servers, to remotely execute arbitrary code with SYSTEM privileges and compromise the vulnerable servers.
Researchers Kevin Beaumont and Troy Mursch warned that attacker are compromising the unpatched servers and stealing the passwords and other confidential information from the servers.
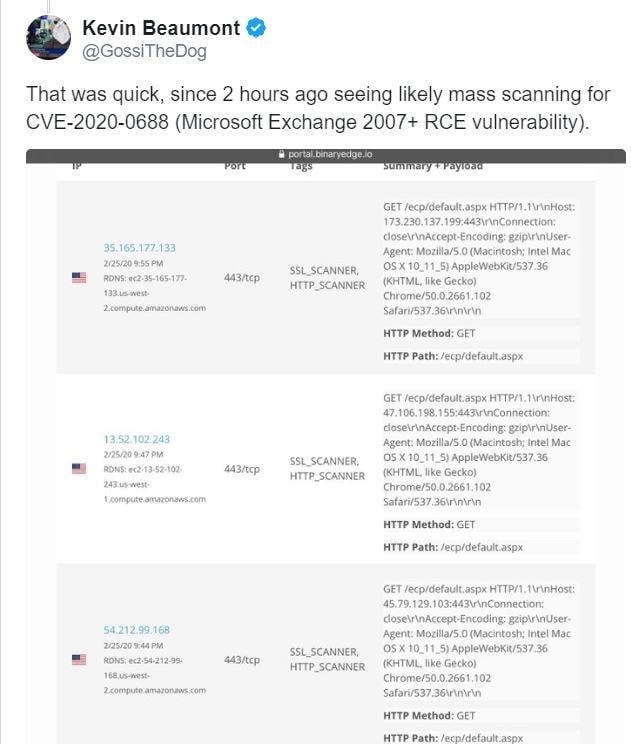
Demonstration of this vulnerability has already been done by Zero Day Initiative.
Click on this link below to watch the demo of the issue.
HOW TO FIX
Request to the System Administrators to install the patches as soon as possible.
| Version | Security Bulletin | Patches |
| Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 | 4536989 | Security update |
| Microsoft Exchange Server 2013 Cumulative Update 23 | 4536988 | Security update |
| Microsoft Exchange Server 2016 Cumulative Update 14 | 4536987 | Security update |
| Microsoft Exchange Server 2016 Cumulative Update 15 | 4536987 | Security update |
| Microsoft Exchange Server 2019 Cumulative Update 3 | 4536987 | Security update |
| Microsoft Exchange Server 2019 Cumulative Update 4 | 4536987 | Security update |
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
