Cybersecurity experts report the detection of a new variant of attack based on the manipulation of executable images. Identified as Process Ghosting, this attack would allow threat actors to bypass the protections enabled on a target Windows system in order to execute malicious code. Gabriel Landau, a specialist at Elastic Security, published a detailed report of this attack.
According to the specialist, the attack extends the methods of endpoint evasion known as Process Herpaderping, allowing the execution of code inadvertently for any anti-malware solution. The Process Herpaderping attack was first described in October 2020 as a method to hide the behavior of a running process by modifying the executable on disk after the image has been mapped to memory.
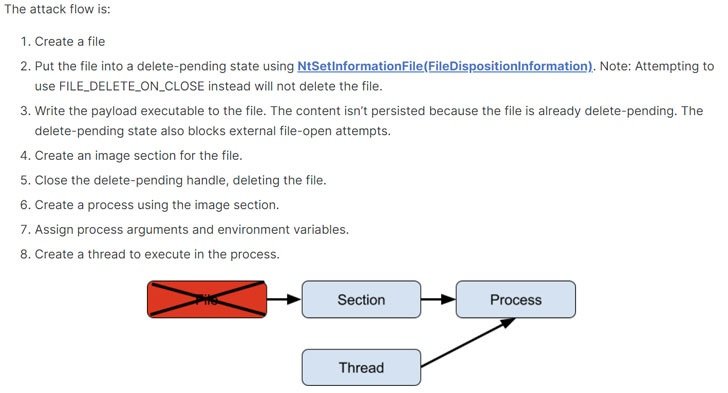
According to the expert, the evasion tasks work because of “a breach between the time a process is created and the time security products are notified of its creation,” allowing threat actors to identify a space to manipulate the executable before security products can scan the malicious activity.
Process Ghosting goes a step beyond attacks like Process Herpaderping by allowing the execution of malicious payloads that have already been removed, as well as taking advantage of the stage where Windows tries to prevent executables from being modified only when the binary is assigned to an image section. In other words, it is possible to create a file, mark it for deletion, assign it to an image section, close the file handle to complete the deletion, and then create a process from the now fileless section.
In order to address this security risk, Microsoft released an updated version of its Sysinternals Suite in early January with an enhanced System Monitoring utility to help detect these attack variants more efficiently.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
