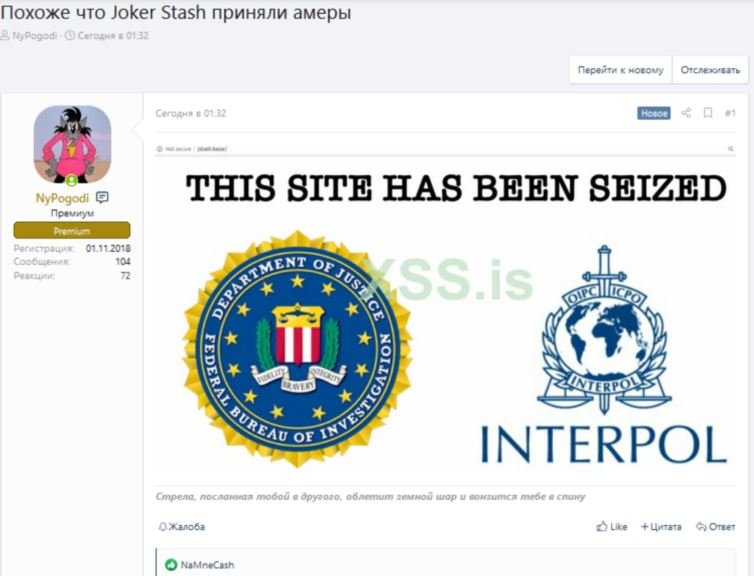
According to recent reports, the blockchain domains of Joker’s Stash, a platform known for selling compromised payment cards, showed a notification from Interpol and the U.S. Department of Justice announcing that police had taken control of these sites. Joker’s Stash operators have several versions of the site, with blockchain domains including .bazar, .lib, .emc and Tor.
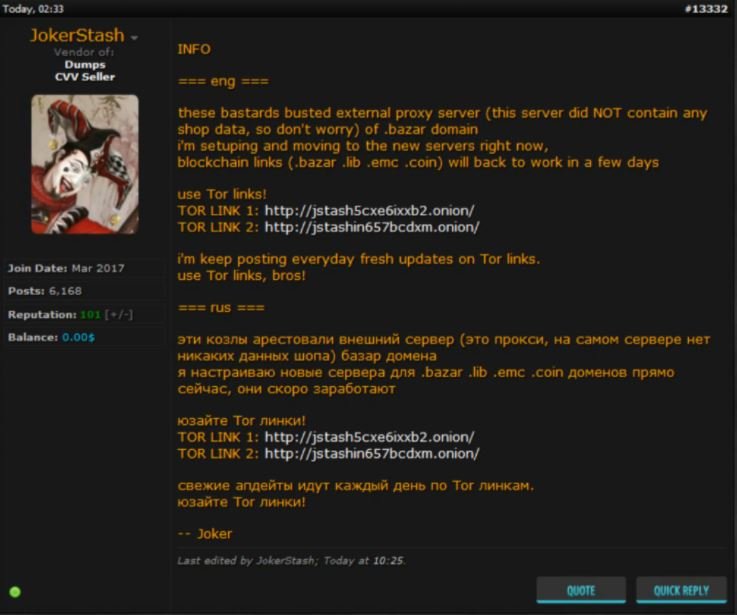
In response to the notification, the official representative of Joker’s Stash created a post on Club2CRD, a Russian-speaking forum, to report that the external proxy server of the .bazar domain had been compromised: “New servers are being created to migrate the affected services; everything will be back to normal in a few days.”
Blockchain DNS technology is a decentralized system for top-level domains that allows access to advanced security features. Blockchain DNS sites are usually accessed through Chrome, with a browser extension that allows access to sites with certain URL suffixes. Joker’s Stash started this technology a few years ago.
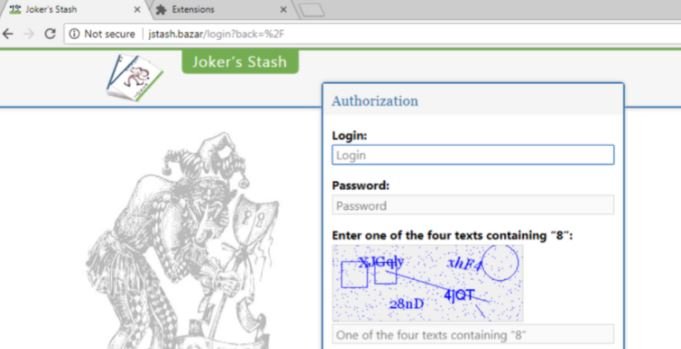
Platforms similar to Joker’s Stash have been experimenting with DNS peer-to-peer technology to hide malicious activity. Because blockchain domains do not depend on a central authority, records contain unique encrypted hashes instead of a person’s name and address, so it is more difficult for research agencies to detect and delete these sites.
When a clandestine forum fails, users immediately assume that this is part of a raid, so they send requests for information to the operators of these forums. In this case, the Joker’s Stash team may have released its incident update to avoid unfounded fears about failures in the affected domain.
In their latest update, Joker’s Stash .bazar, .lib, .emc, .coin domains have stopped displaying the order forces seizure note. Instead, the sites simply display a “Server Not Found” warning. The Department of Justice and Interpol have also not commented on this.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
