In 2019, a group of videogame hackers managed to break into Nintendo’s systems after compromising an employee’s computer, an incident that resulted in the leakage of source code from titles such as Super Mario 64 and even vital information about consoles such as Switch and 3DS, as well as internal sensitive data.
Among the documents presented are the records of a group of Nintendo hired investigators who would have carried out an espionage campaign against various video game hackers, all in order to offer them employment or, in some cases, threaten to take legal action against them.
To the surprise of many users and videogame enthusiasts this is a common practice for the entertainment industry, including videogame developing. However, the leaked documentation mentions that this group of researchers followed for months the hacker known as “Neimod”, who presumes to be the first to hack a Nintendo 3DS.
Apparently Nintendo knew all about the hacker; his home, habits, hobbies, close people and even his favorite foods. The documents also detail a plan to approach the individual without raising suspicions and avoiding legal allegations against Nintendo.
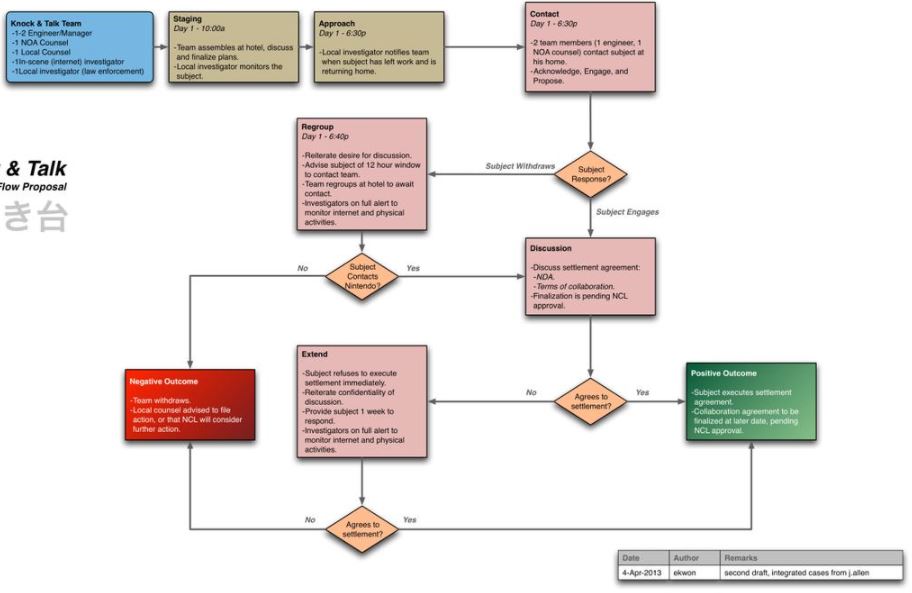
As mentioned above, Nintendo may have tried to convince it to work together to find vulnerabilities in its consoles. Other hackers who have received similar offers mention that, if you refuse to work with Nintendo, they may face demands from the company.
Despite the constant surveillance against him, Neimod’s real name has not been revealed, not to mention that the hacker significantly decreased its online activity after the Nintendo 3DS’s commitment in 2013. At the moment it is unknown whether this campaign is still active, although video game hacker groups will most likely continue to develop methods to compromise Nintendo’s developments.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
