Cybersecurity researchers from Bishop Fox detail the development of a hacking technique to analyze pixelated text and recreate its original wording in a completely readable way using a single software tool, which could prove useful in various circumstances, including in cyberattacks.
This process depends on the Depix tool, based on the search for permutations of pixels could have resulted in certain pixelated blocks, employing what is known as de Bruijn sequence from the correct source. In real-world examples, you’re likely to get minor variations in the analyzed text. This tool is available on GitHub.
In the following example, we can see pixelated text and decrypted by the tool, a process known as pixelation:
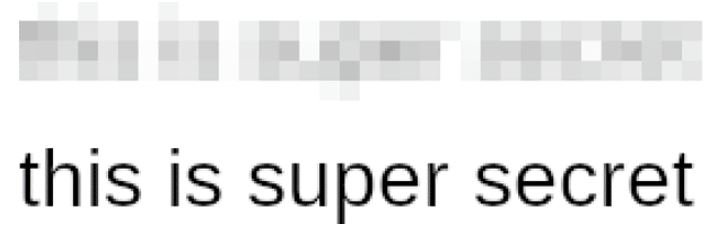
The researchers mention that this process is based on a very simple algorithm, dividing the image to be analyzed into a grid and subsequently assigning a color to each area and obtaining the original text text through the distribution of the colors in each fragment of the grid.

Although experts recognize that some of the information could be lost in this process, it is also a lot of information that can be extracted. For their proof of concept (PoC), the researchers acting as attackers had to know some data about the target, including:
- Know that text is being analyzed
- The font type of the redacted text
- The font size of the redacted text
The researchers mention that a single change of a pixel somewhere in the original image only affects the redacted block to which it belongs, meaning that only the largest blocks of characters are required to interpret the pixelated image and obtain the redacted text.
In other words, during this process experts simply guess a letter “a”, pixelate that letter and analyze how well it matches the redacted image, subsequently guessing the letter “b”, and so on.
While this sounds simple enough, the process involves all sorts of logical problems that cannot be solved in a single way, although other methods might prove functional. The full investigation is available on Bishop Fox’s official platforms.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
