Cybersecurity specialists report that threat actors could track the online activity of Tor browser users to extract potentially sensitive information. This attack variant is known as Website Fingerprinting (WF).
This new attack variant represents a breakthrough in malicious hacking, as similar techniques previously known have an accuracy of just over 60%; According to USENIX researchers Giovanni Cherubin and Rob Jansen, the new attack variant could exceed 95% accuracy.
As some users will know, Tor browsers offer “non-linkable communication,” routing Internet traffic through an overlay network composed of more than 6,000 relays and whose main purpose is to anonymize the origin of the traffic and the websites visited by the user.
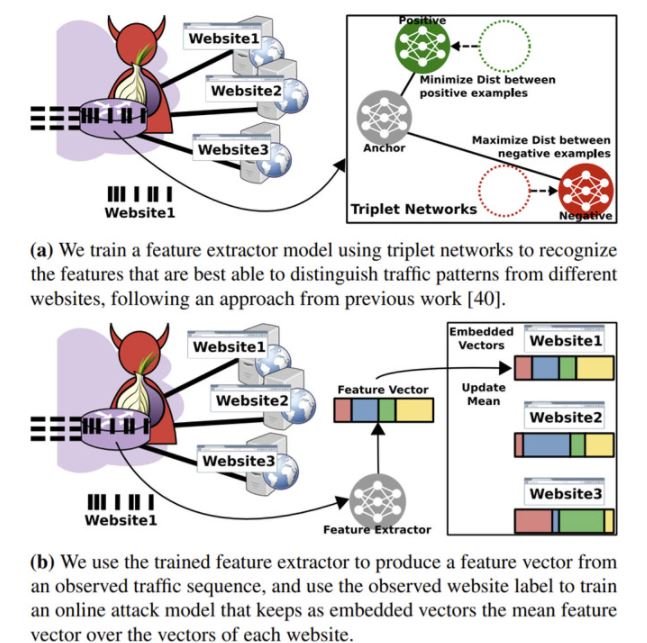
Requests are encrypted once for each relay to make analysis even more difficult and prevent information leakage. Although the Tor clients themselves are not anonymous about their inbound relays, because the traffic is encrypted and requests jump through multiple hops, these inbound relays cannot identify the destination of the clients and output nodes.
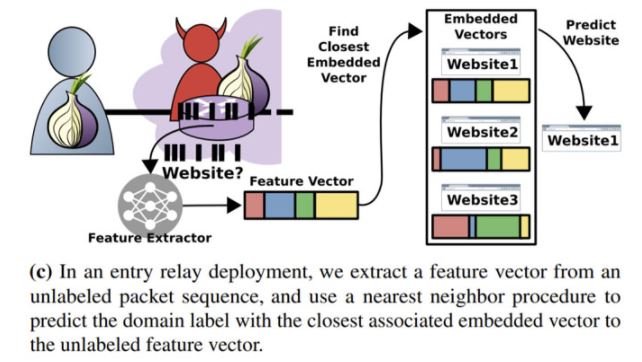
This attack variant is specially designed to remove these security restrictions, allowing threat actors to analyze the victim’s encrypted traffic patterns. The attack described requires threat actors to run an exit node to capture the diversity of traffic generated by real users, which is then used as a source to collect Tor traffic traces and design a classification model based on machine learning.
Attackers also require training an implementation for observing genuine Tor traffic, collected from a series of relays to continuously update the attacker’s classification models. The researchers successfully tested their attack using a custom version of Tor v0.4.3.5 to extract sensitive information.
Faced with this security risk, researchers recommend to Tor browser users to enable all possible protections, which depends on the settings set by users.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
