In a significant development for cybersecurity in critical infrastructure, MITRE Corporation has launched a new threat-modeling framework known as EMB3D. This initiative marks a collaborative effort among leaders in security technology, including MITRE, Red Balloon Security, and Narf Industries.
EMB3D, or Embedded Model-Based Development, Defense, and Disruption, provides a comprehensive toolkit for assessing and mitigating cyber threats to embedded devices. These devices, which are integral to critical infrastructures such as power grids, water systems, and transportation networks, are often the targets of sophisticated cyber-attacks.
The new threat model is publicly accessible at EMB3D’s official website, offering a cultivated knowledge base of cyber threats and vulnerabilities specific to embedded systems. It aims to foster a common understanding and proactive approach among manufacturers, vendors, asset owners, testers, and security researchers.
MITRE EMB3D (Embedded System Attack Model) is a comprehensive threat modeling framework designed to secure embedded devices, which are often used in critical infrastructure sectors. This model helps identify, analyze, and mitigate threats specific to embedded systems. Below is an in-depth look into its components, purpose, and application, along with examples to illustrate its usage.
Components of EMB3D
- Threat Identification and Analysis:
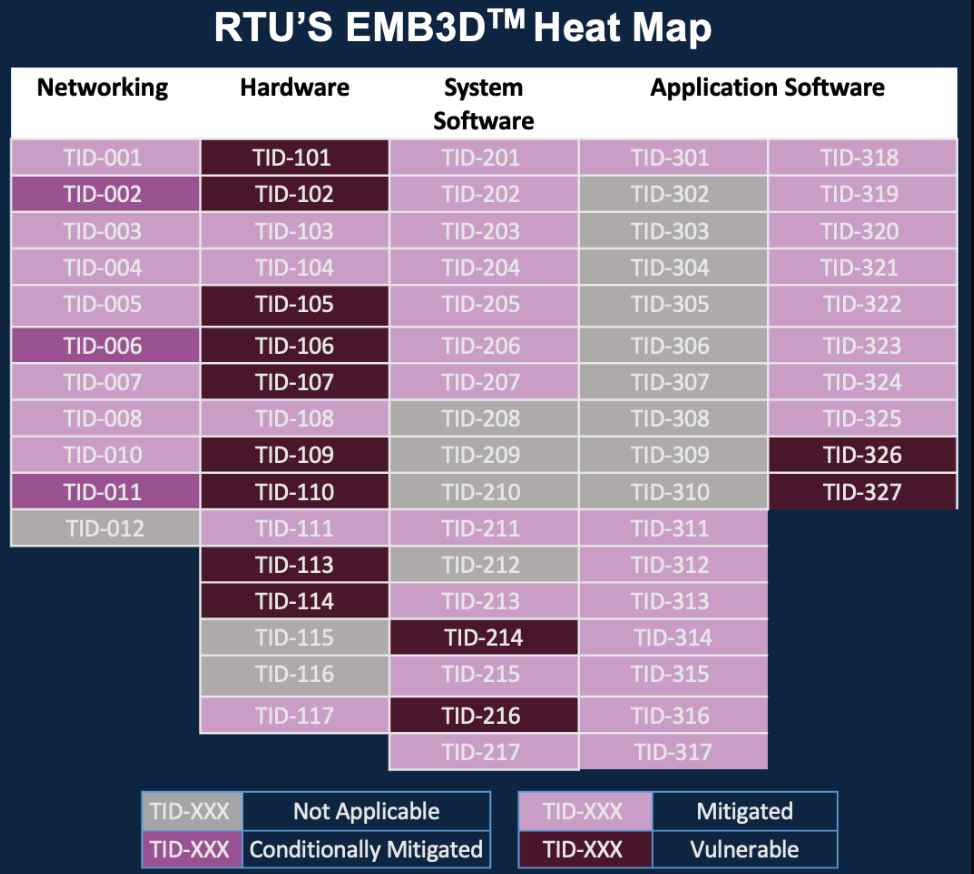
- Threat Knowledge Base: EMB3D provides a detailed knowledge base of threats targeting embedded devices. These threats are drawn from real-world incidents and theoretical research.
- Threat Mapping: Threats are mapped to specific device properties, such as firmware, hardware interfaces, communication protocols, and sensors. This helps in understanding how different threats can exploit particular vulnerabilities in an embedded system.
- Vulnerability Mapping:
- Common Weakness Enumeration (CWE): EMB3D aligns with CWE to categorize common weaknesses in embedded devices.
- Common Vulnerabilities and Exposures (CVE): The model incorporates CVEs to provide details on specific vulnerabilities and their potential impacts .
- Mitigations:
- Technical Mechanisms: EMB3D suggests specific technical mitigations that device vendors can implement. These include secure coding practices, hardware security modules, encryption, and access controls.
- Design Considerations: Emphasizes the importance of incorporating security during the design phase to reduce the need for post-deployment fixes.
- Continuous Updates and Community Involvement:
- Living Framework: EMB3D is continuously updated with new threats and mitigations as the cybersecurity landscape evolves.
- Community Collaboration: MITRE encourages feedback from device vendors, asset owners, security researchers, and academics to enhance the framework .
Purpose and Impact
The primary purpose of EMB3D is to help stakeholders in the embedded device ecosystem understand and address security threats early in the device lifecycle. This proactive approach leads to more secure devices and infrastructure, reducing the need for costly and complex security patches after deployment.
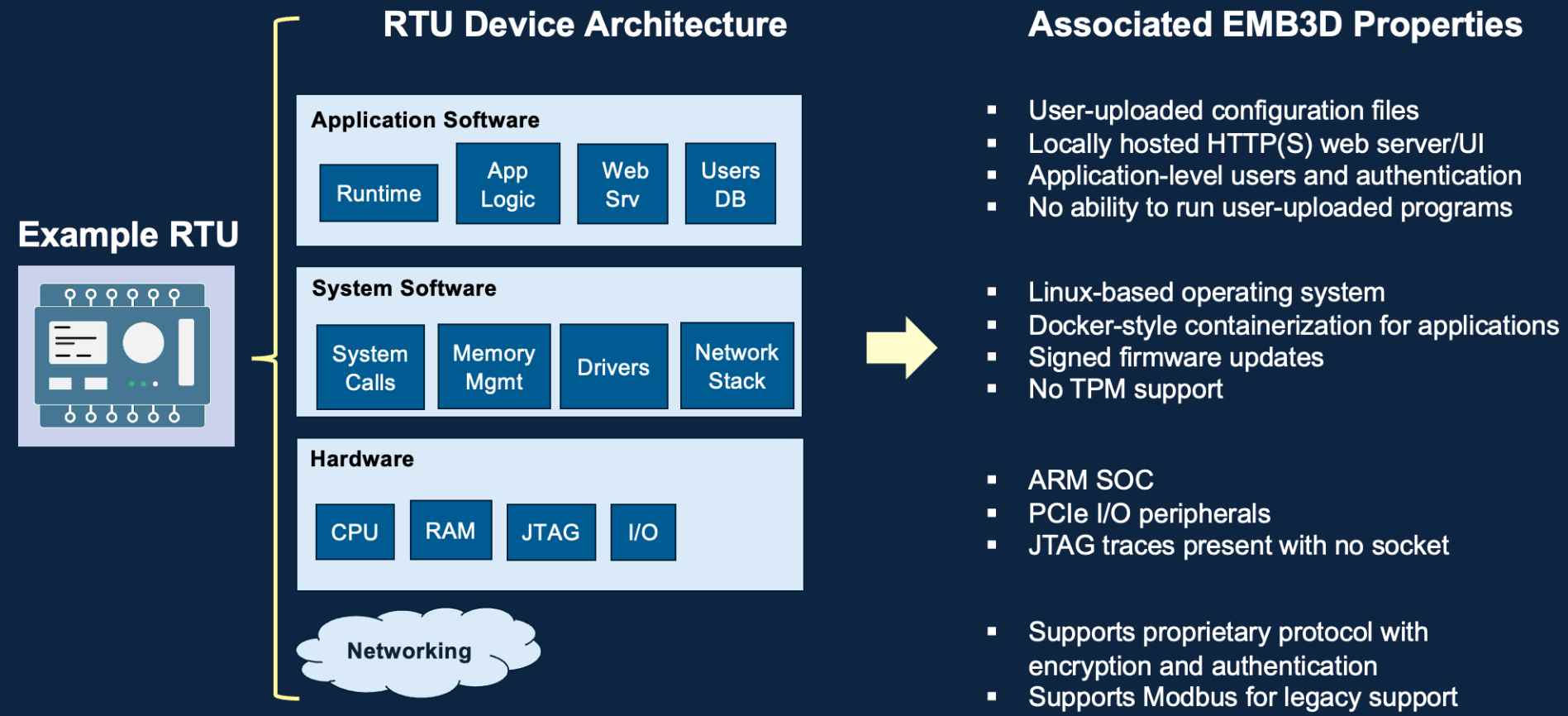
Device Properties in EMB3D
- Firmware:
- Description: The low-level software that controls the device’s hardware.
- Threats: Unauthorized firmware updates, tampered firmware, firmware reverse engineering.
- Mitigations: Secure boot, firmware signing, firmware integrity checks.
- Hardware Interfaces:
- Description: Physical ports and connections, such as USB, GPIO, and JTAG.
- Threats: Physical tampering, unauthorized access through debugging ports.
- Mitigations: Disable unused ports, secure physical access, tamper-evident seals.
- Communication Protocols:
- Description: Methods used by the device to communicate with other devices or networks, such as Wi-Fi, Zigbee, or Ethernet.
- Threats: Eavesdropping, man-in-the-middle attacks, protocol exploitation.
- Mitigations: Encryption, secure protocol selection, network segmentation.
- Sensors and Actuators:
- Description: Components that interact with the physical environment, such as temperature sensors, pressure sensors, and motors.
- Threats: Sensor spoofing, actuator manipulation.
- Mitigations: Input validation, secure control algorithms, redundancy checks.
- Control Software:
- Description: Software that processes inputs and controls the device’s operations.
- Threats: Code injection, logic manipulation, denial of service.
- Mitigations: Code reviews, secure coding practices, runtime integrity checks.
- Data Storage:
- Description: Internal storage used to save data, such as flash memory or EEPROM.
- Threats: Data theft, data corruption, unauthorized data access.
- Mitigations: Encryption, access controls, data integrity checks.
- Power Supply:
- Description: The source of electrical power for the device, including batteries and power regulators.
- Threats: Power supply manipulation, denial of service via power disruption.
- Mitigations: Power surge protection, backup power sources, power integrity monitoring.
- User Interfaces:
- Description: Interfaces through which users interact with the device, such as buttons, touchscreens, and displays.
- Threats: Unauthorized access, spoofing user inputs.
- Mitigations: User authentication, input validation, secure user interface design.
- Network Interfaces:
- Description: Interfaces that connect the device to local or wide area networks.
- Threats: Unauthorized network access, data interception, network-based attacks.
- Mitigations: Network firewalls, secure communication protocols, intrusion detection systems.
- Configuration Management:
- Description: Methods and processes used to manage device settings and configurations.
- Threats: Unauthorized configuration changes, configuration errors.
- Mitigations: Secure configuration interfaces, configuration integrity checks, regular audits.
Applying EMB3D to Enhance Security
Example: Securing an Autonomous Vehicle
- Threat Identification:
- Threats: Remote hijacking, sensor spoofing, unauthorized firmware updates.
- Device Properties: Communication protocols (e.g., CAN bus), sensors (e.g., LIDAR, cameras), firmware.
- Vulnerability Mapping:
- CWE: Insufficient encryption (CWE-311), improper authentication (CWE-287), lack of firmware validation (CWE-345).
- CVE: Known vulnerabilities related to the vehicle’s communication and control systems.
- Mitigation Implementation:
- Technical Mechanisms: Implement strong encryption for data transmission, multi-factor authentication for remote access, secure boot for firmware integrity.
- Design Considerations: Integrate security features during the design phase, conduct thorough security testing.
- Continuous Monitoring and Updating:
- Threat Monitoring: Regularly monitor for new vulnerabilities and threats.
- Community Collaboration: Engage with the cybersecurity community to stay updated on emerging threats and best practices.
By systematically addressing each of these properties and applying the relevant mitigations, organizations can significantly enhance the security of their embedded devices, ensuring robust protection against a wide range of cyber threats
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
