Microsoft along with some organizations blocked world largest Botnet called NECURS that have infected 9 million computers globally. NECURS bot first showed activities back in 2012 and proved their involvement in GameOverZues banking trojan , Dridex , Trickbot and others. NECURS is being dropped in to the victim’ s computer by the other malwares either through email attachments or email advertisements. After capturing the victim , it utilizes it’s kernel mode rootkit capabilities to block security barriers in the victim’s system like Firewall. Microsoft said , “During a 58-day period in our investigation, we observed that one NECURS – infected computer sent a total of 3.8 million spam emails to over 40.6 million potential victims”
NECURS is believed to be operated by a group of hackers in Russia who lends or sell access to the infected computers to the other cyber-criminals as a part of botnet-for-hire services.
The team BitSight who has been working with Microsoft since 2017 , said “Measuring infections for NECURS is not as simple as for other malware; this is due to how the malware establishes communication with its command and control server“
HOW NECURS WORKS ?
As said earlier , NECURS spread by the other malware’s either through attachments, pop-ups or advertisements. After the system got infected with the NECURS, it communicates with its command and control server, through a layered approach using a centralized and P2P (peer to peer) communication channel to prevent disclosing by the Law Enforcement Agencies . NECURS follows a distinctive approach in order to connect to the domains that controls a list of IP’s and domains to connect the infected system to the network of botnets. Necurs follows Domain generation algorithm (DGA) as:
This domain generation algorithm is featured into three steps .
- The very first task that NECURS do after entering into the system is that it checks the internet connectivity by pinging facebook.com and Microsoft.com .
Then it connects to three pools to get the accurate date and time
0.pool.ntp.org
1.pool.ntp.org
2.pool.ntp.org
- Then comes into the play the first DGA that generates four domains with TLD as .com. The algorithm generating these domains is absolutely pure mathematics and thus these domains can’t be predictable. The purpose of these domains is to detect the simulated internet in a practical lab environment to test if the infected system is really working with the network of Botnet’s or not. Some examples of those domains are :
sxotmrxwhddr.com
btysiiquuc.com
kfncxvayakmb.com
vmslcvvocseu.com
- If the lab detection passes, then the process goes to second stage and second DGA comes into play which is the most important step of the whole DGA process . In the second DGA, the NECURS will try to connect to 16 hard-coded list of pseudo-DGA domains with TLD as .bit. These hard-coded domains are the command and control domains to which NECURS want system to connect. Even if the NECURS is able to load only one domain from the 16 hard-coded domains. Some examples of these domains are :
qcmbartuop.bit
qcmbartuop.bit
qcmbartuop.bit
qcmbartuop.bit
- A test is perfomed by pinging facebook.com to check the connectivity at this stage .
- The third DGA comes into play and generates possible 2048 domains that are C2 among 43 Top Level Domains including .bit. The special feature about this stage of DGA is that it is dependent upon time and changes after every 4 days .
As a backup option, if all the above DGA fails , then the NECURS tries to get the domain from a list of 2000 peers from P2P network that is active all the time. The peers in the network are the infected system with elevated privileges .
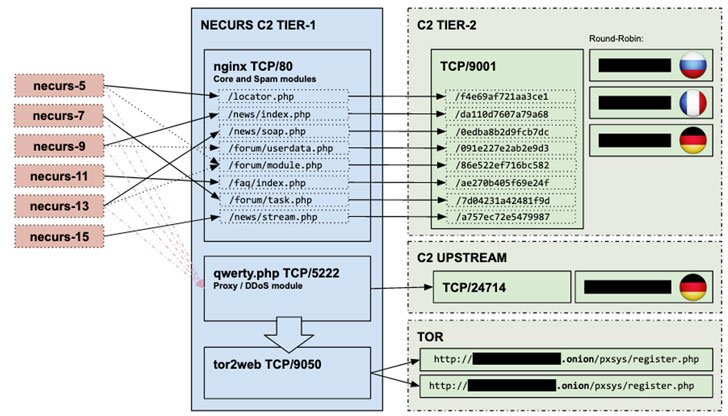
The whole process is made covered by an additional layer of security that follows 2 tier approach using proxies to reverse all communication. Firstly all infected computers in the network play a robin round from which communications are transferred to the first tier which is made up of the cheap VPS in countries like Russia, Ukraine, etc which then reverses all the communication in the upstream of tier 2 C2 .
As a measure to stop Microsoft has already reported these domains to their respective registries in their countries and blocked the working of many Botnet in NECURS Network .The firm is also taking the additional steps and is getting in partnership with ISPs , domain registries , government CERTs and law enforcements in Mexico, Colombia, Taiwan, India, Japan, France, Spain, Poland and Romania, among others to stop the spread of NECURS .

RSU is security researcher who is constantly working to make world a secure place to live. He is working day and night in Cyber Security area.
