Several members of the cybersecurity community have shared a list of organizations affected by Solarigate malware (also known as Sunburst), related to SolarWinds supply chain commitment.
The list shows that some of the most important technology firms, such as Intel, Cisco, Belkin, and Nvidia, were affected by this severe security incident. Reports indicate that Mediatec, which has become the world’s second largest semiconductor supplier, could also have been one of the main targets of hackers, although this information has not been corroborated.
To develop this list, researchers decoded a dynamically generated portion of the C2 subdomain for one of the compromised devices that were analyzed, as well as employing a set of passive DNS data and web traffic to the primary domain connected to the backdoor, used to extract the compromised information.
By decoding the list of subdomains, TrueSec and other security companies, including QiAnXin RedDrip, Kaspersky, and Prevasio, they were able to find many organizations affected by this massive campaign.
TrueSec provides a list of names of internal organizations that were not only infected by the backdoor, but were also attacked individually, which makes hackers think that hackers performed privilege escalations to perform subsequent attacks. “This list contains the decoded values of the internal domain names; we can only assume that they belong to an organization based on domain name and publicly available information,” adds the TrueSec report.
The current list of companies affected by the SolarWinds update is shown below (organization names may be inaccurate because they are based on decoded internal names):
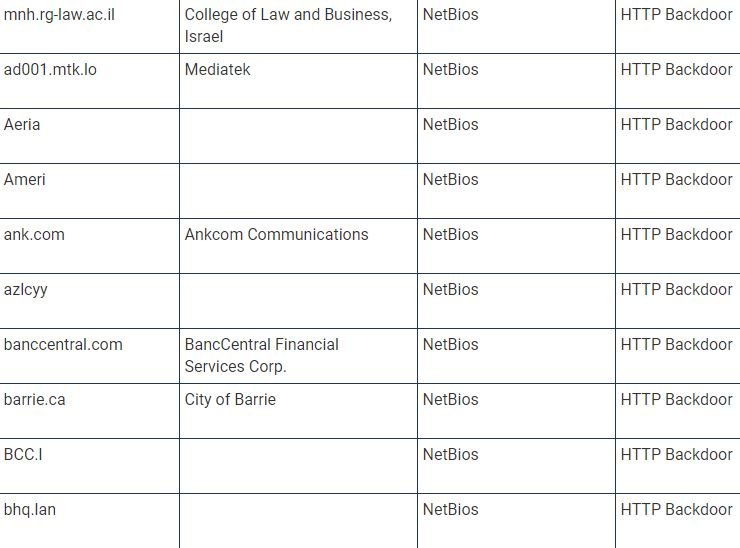
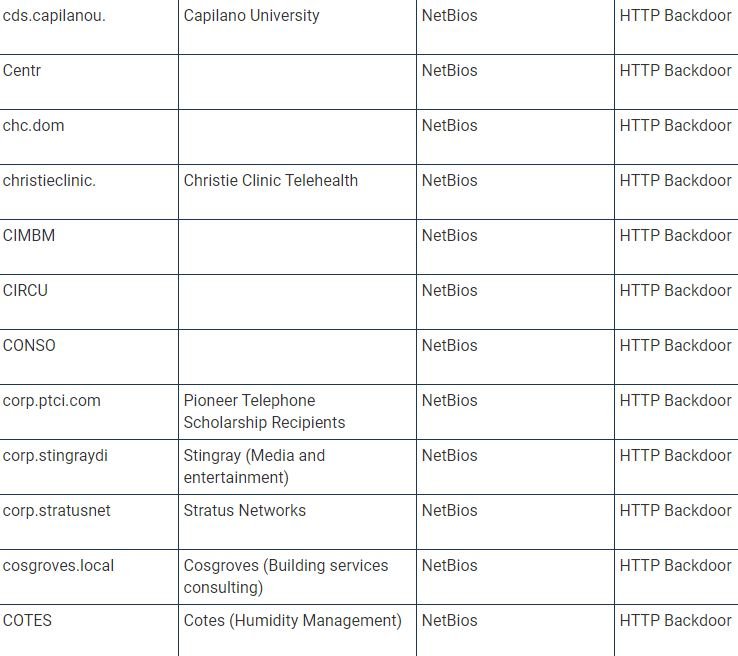
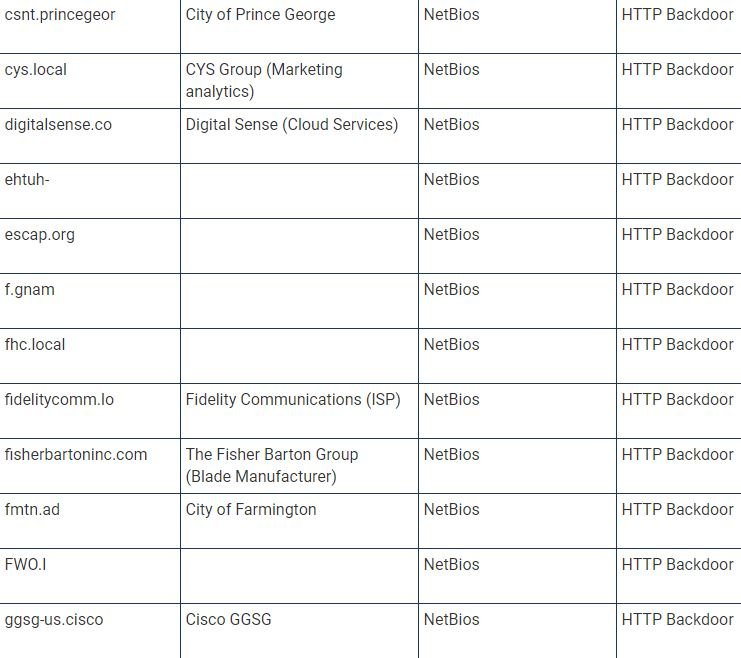
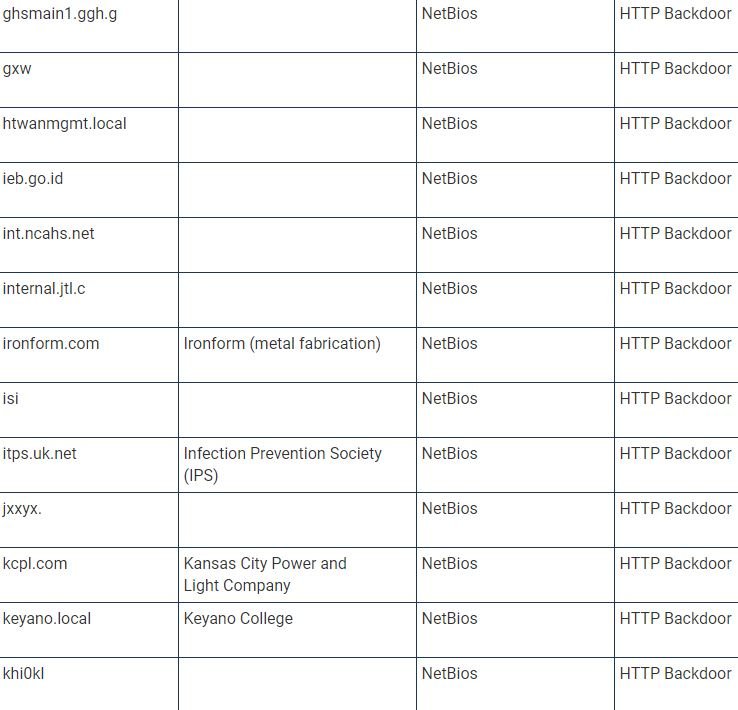
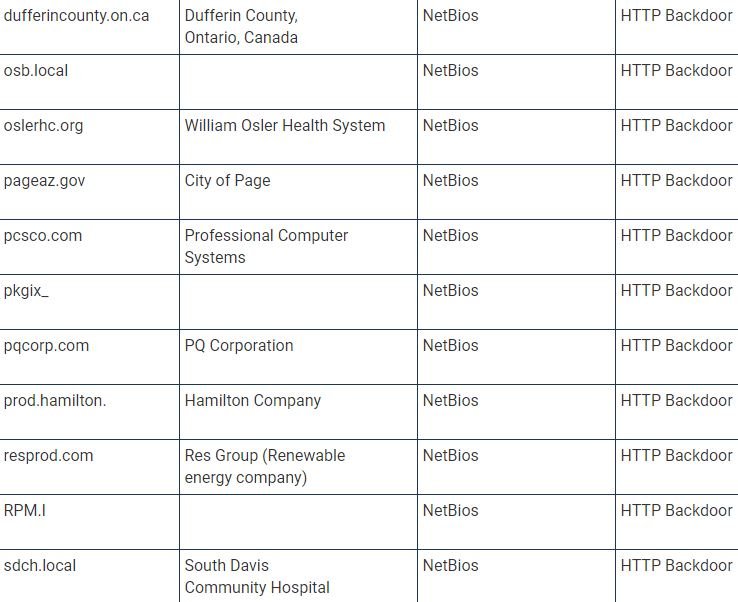
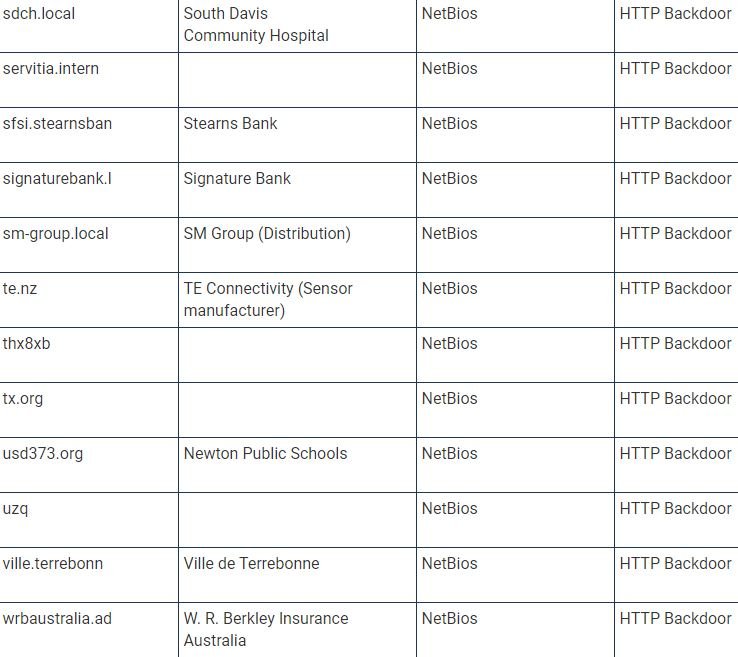
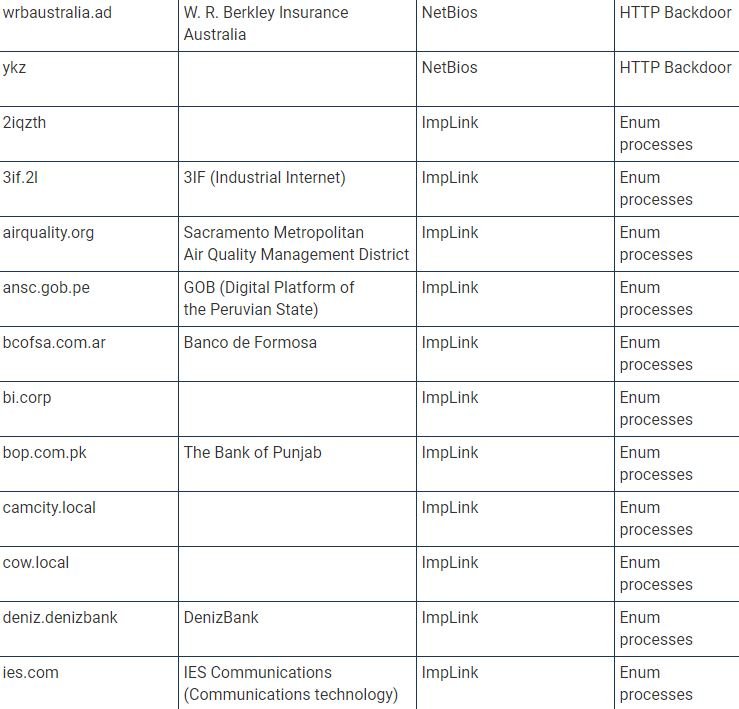
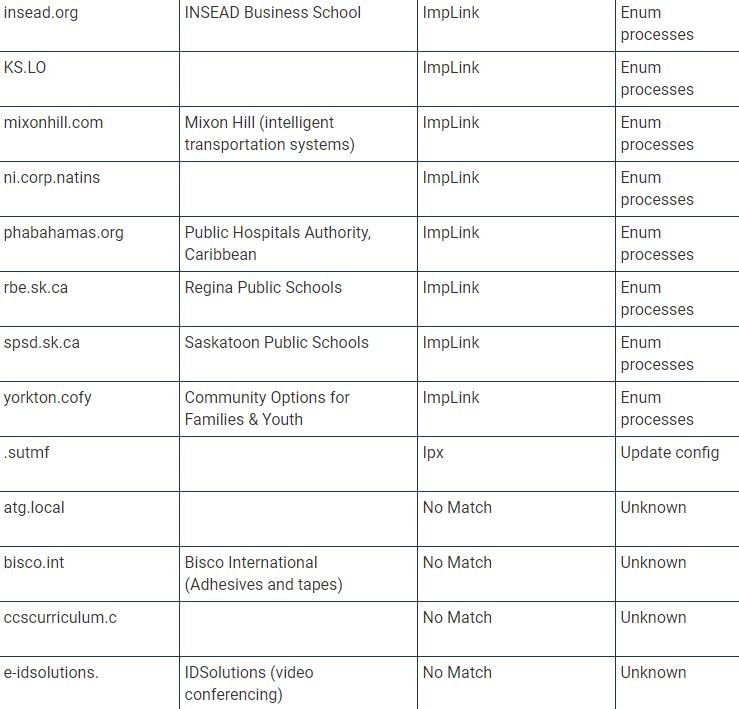
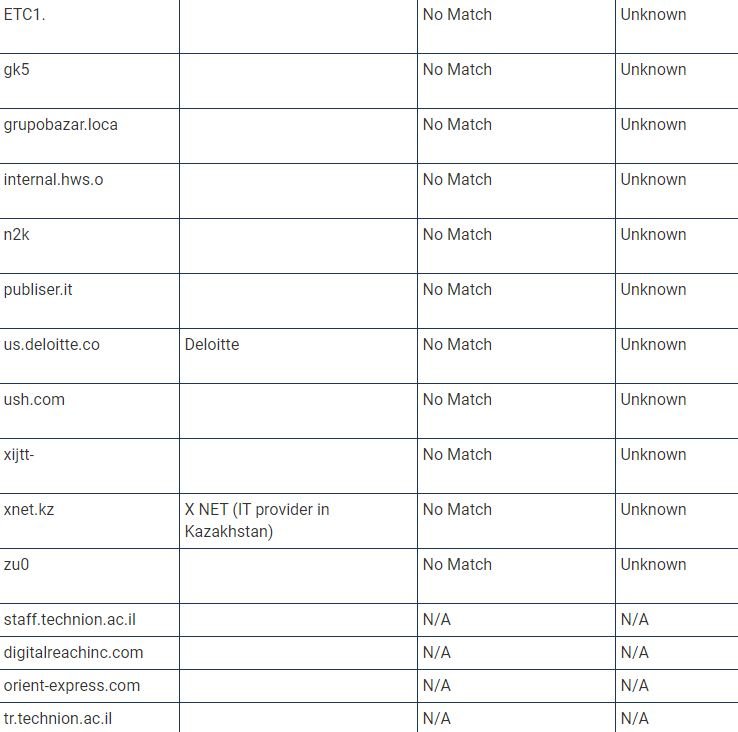
Experts are still investigating this incident, as there is still a lot of information to be discovered.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
