Cybersecurity specialists report that Iranian government has deployed two major Internet surveillance and monitoring operations to track the activities of at least a thousand dissidents and political activists. The alleged targets of this campaign reside in Iran, the United States and the United Kingdom, among others.
According to the specialists, the hacking groups responsible for these campaigns employ various malicious techniques, including the use of spyware for personal computers and mobile devices to spy on calls, text and voice messages, PDF files and images in various formats.
The report mentions that one of these hacking groups, identified as APT-50 or Domestic Kitten, operates by tricking its victims into downloading malware on mobile devices through various attack vectors, including:
- Using malicious versions of games available on the Google Play Store
- Using fake versions of a restaurant app in Tehran
- Using fake security tools
- Distributing a malicious wallpaper app, which contains pro-Islamic State images loaded with malware
- Using a malicious version of Google Play
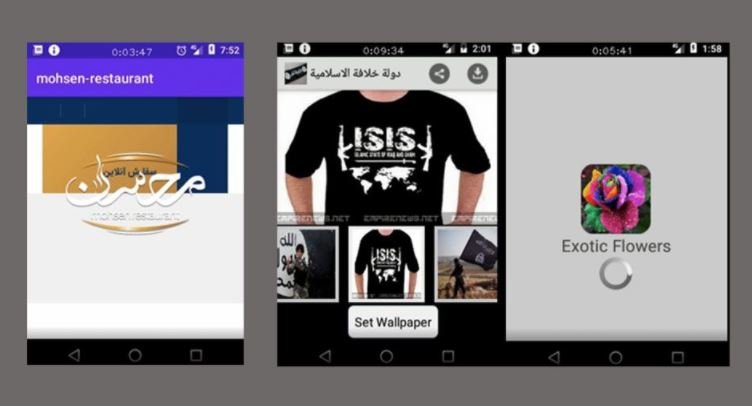
So far researchers have identified at least 200 targets of this attack, including at least 600 successful attacks.
About the second hacking group participating in this campaign, identified as Prince of Persia or Infy, experts claim that they have attacked the personal computers of dissidents in at least twelve countries through sophisticated phishing messages. Despite constant signaling, Iran’s government has not spoken out on it.
Domestic Kitten’s activity was first reported in 2018, when security firm Check Point reported the detection of evidence from at least 10 malicious campaigns deployed since 2017. Experts mentioned that at least four of these campaigns are still active.
Threat actors turn to Iranian blogs, Telegram channels and SMS messages to try to get attention to targets and get them to install malware on their devices. This malware, identified as Furball, features advanced features such as:
- Recording calls and voice notes
- Tracking the location of the device
- Extracting text messages and call logs
- Theft of media files
- Getting a list of installed apps
- File theft on external storage
On the other hand, experts mention that Infy has been active at least since 2007. The most recent attack was targeted against thousands of PCs using fake emails with engaging content in addition to attachments.
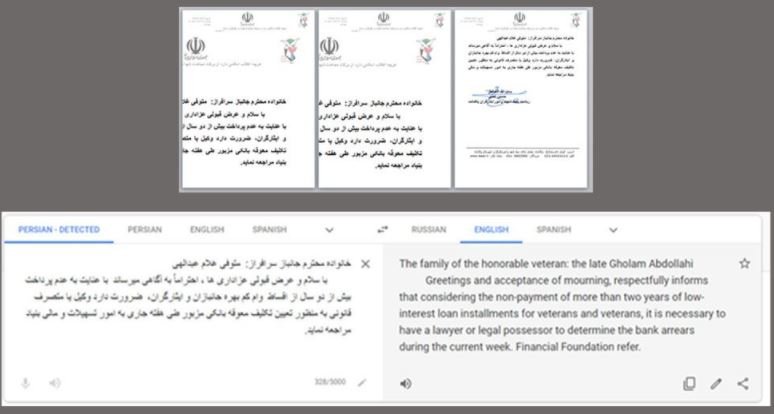
If users interacted with this document, a spyware was installed with which threat actors could steal all kinds of sensitive information. Experts mention that the capabilities of this hacking group are highly sophisticated, so they recommend staying alert to any potential attacks.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
