Researchers have discovered a new vulnerability in Github that might allow an attacker to take advantage of a race situation in the process of creating a repository on GitHub or changing a username on the platform. This approach may be used to carry out an attack known as repojacking. The successful exploitation of this vulnerability has a negative effect on the open-source community since it enables the hijacking of over 4,000 code packages written in languages such as Go, PHP, and Swift, as well as activities on GitHub. An adversary might gain control of a vulnerability repository on GitHub by using a technique known as “repo jacking.” This technique involves taking advantage of a logical flaw that makes vulnerable users with renamed accounts visible.
When a hacker targets GitHub, they want to acquire control of a valid namespace that is heavily used. The username and the name of the repository are combined in order to produce a namespace. An adversary might gain control of a vulnerability repository on GitHub by using a technique known as “repo jacking.” This technique involves taking advantage of a logical flaw that makes vulnerable users with renamed accounts visible.
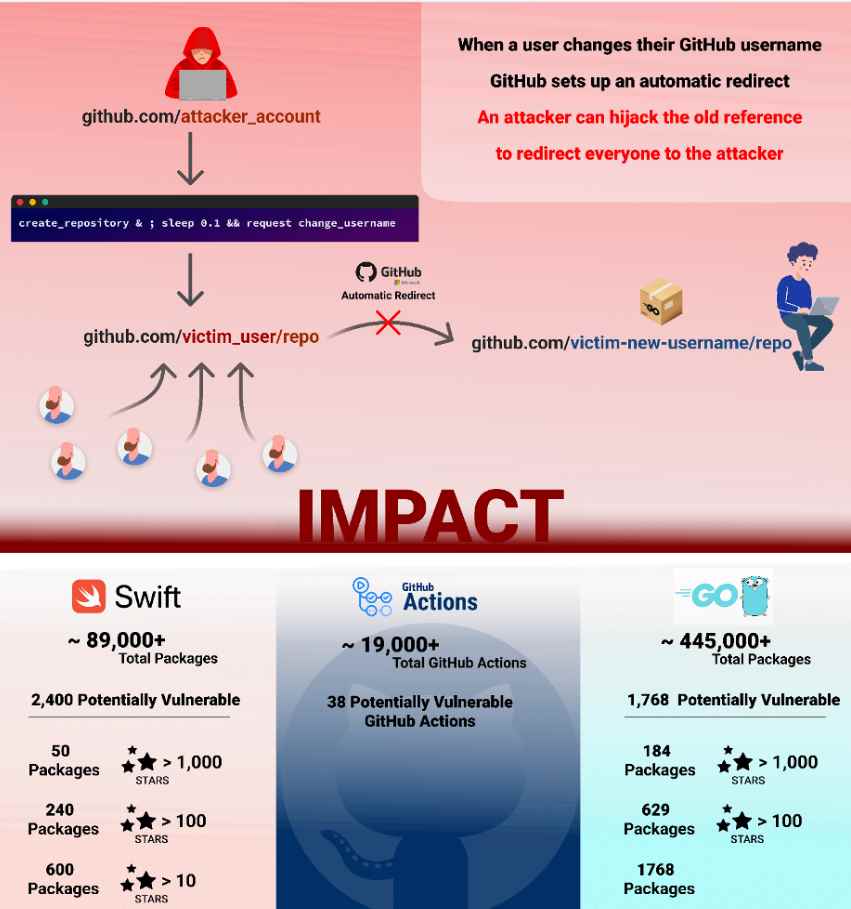
When a namespace’s initial username is changed by utilizing GitHub’s “user rename” option, the namespace’s vulnerability to repojacking is increased. The process of changing a username is a straightforward and speedy one. A warning makes it very apparent that the new repository will get all of the traffic that was previously sent to the old repository’s URL.
It is important to note that the following consequence is outlined in the documentation that GitHub provides for this feature: “After changing your username, your old username becomes available for anyone else to claim.” “Once the username is renamed, an attacker can claim the old username, open a repo under the matching repo name, and hijack the namespace,” the researchers added.
In addition, using this bypass may lead to the takeover of popular GitHub activities, which are similarly used by giving a GitHub namespace. This would be the case if the bypass was utilized.
It is possible that large-scale Supply Chain attacks with far-reaching impacts may be triggered by poisoning a popular activity on GitHub.A recent research conducted by Aqua found that even large corporations such as Google and Lyft were vulnerable to this kind of cyberattack. This highlights how severe the vulnerability is since it has the potential to damage some of the most well-known brands in the information technology industry, many of whom have already taken prompt action to mitigate the risks after being told of the vulnerability.
GitHub has introduced a preventative measure known as “popular repository namespace retirement” in order to mitigate the effects of this possibly harmful conduct.
According to this policy, any repository that has more than one hundred clones when the user account associated with it is changed is considered “retired” and is inaccessible to other users.
It is recommended that retired namespaces be avoided in order to limit the attack surface. You should also make sure that the code you are using does not have any dependencies that might lead to a repository on GitHub that is vulnerable to being hijacked by repojackers.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
