Redis, which stands for “remote dictionary server,” is a cache and database that runs in memory and is open source. In 2009, it was made available for the very first time as a solution for real-time applications that required a mechanism to send data to their customers more quickly than a relational database was capable of managing. It enables the retrieval and distribution of data in a short amount of response time and can accommodate millions of queries per second. Redis ensures that it is responsive by storing data that is often retrieved in memory and employing a cache to do so.
Researchers working for the cloud security business Aqua Security have just discovered a backdoor that targets Redis servers, and they are sounding the alarm about it.
The malicious software, which has been given the name Redigo and is written in Go, was seen being used in an attack that exploited a known vulnerability in Redis (CVE-2022-0543, with a CVSS score of 10) in order to get initial access.
The vulnerability, which might allow for remote code execution (RCE), made news in April when experts in the field of information security identified more than 2,000 internet-facing servers as having a possibility of being affected. February saw the release of many patches.
Redis is susceptible to attack since it makes use of the Lua scripting engine. This allows users to load and run Lua programs directly on the server. The vulnerability has been identified. The Redis architecture is comprised of the Redis client and the Redis server as its two primary running processes. The Redis server is the most significant component of the whole design. It is in charge of storing data in memory and managing the operations associated with storage management. The server also has a Lua scripting engine, which enables users to upload Lua scripts and run them directly on the server without the need for an intermediary. Because of this capability, the process of reading and writing data from scripts is made to be highly efficient. The engine need to be sandboxed such that interactions with Redis clients are carried out via the use of Redis application programming interfaces (APIs), hence restricting the client’s ability to execute arbitrary code on the computer on which Redis is operating. On the other hand, in 2022, a security hole was found to exist in the Lua scripting engine. The Lua library offered a dynamic library in some packages distributed by Debian. An instance of a package variable is loaded whenever the Redis server loads the Lua library. The package is kept in the Lua sandbox so that it may be called from inside any Lua library. As a consequence, a Lua sandbox escape occurred, which made it possible for an adversary to carry out arbitrary instructions.
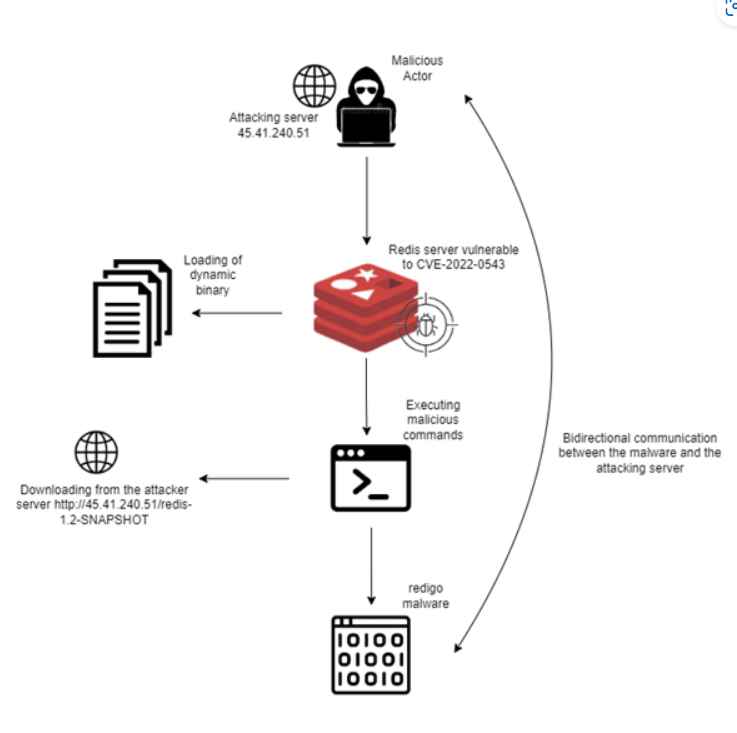
Attackers who are looking for internet-accessible Redis servers can execute a series of commands that will allow them to identify instances that are vulnerable to CVE-2022-0543. They can then exploit the security bug to run code under the control of the attacker after identifying the vulnerable instances.
As a part of the observed attacks, malicious actors were dropping and running the Redigo backdoor, which camouflaged its existence on the computer by concealing its connection with the command-and-control (C&C) server.
Aqua has not been successful in determining the objective of the Redigo cyberattacks; nonetheless, the company thinks that distributed denial-of-service (DDoS), cryptomining, data theft, and permanent access to compromised environments are the most likely explanations.
Researchers think that the threat was created specifically for Redis servers by the perpetrators of the attack due to the fact that certain of the backdoor’s features are unique to Redis. At this time, the malicious software is not recognized by any of VirusTotal’s antimalware engines.
The adversaries are concerned with keeping their behavior a secret in order to avoid being discovered. They are able to achieve this by using a method of connection with Redis that seems to be genuine and mimics communication across Redis clusters by making use of port 6379. However, the adversaries are using the connectivity to convey directives that would give them control of the server that is susceptible to attack.
It is strongly recommended that owners of Redis servers implement fixes as soon as they become available and closely monitor their environments for any unusual behavior.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
