Last August, Google announced the launch of a new security feature that allows people under the age of eighteen to submit requests to remove their photos from search results, which as of this week is available worldwide.
According to cybersecurity experts, any underage user can start the process of deleting their photos on Google’s support page. To do this, you need to provide the URLs of the images you want to remove from the search results, the search words associated with these images, and the name and age of the person requesting, in addition to the data of the parents or guardians.
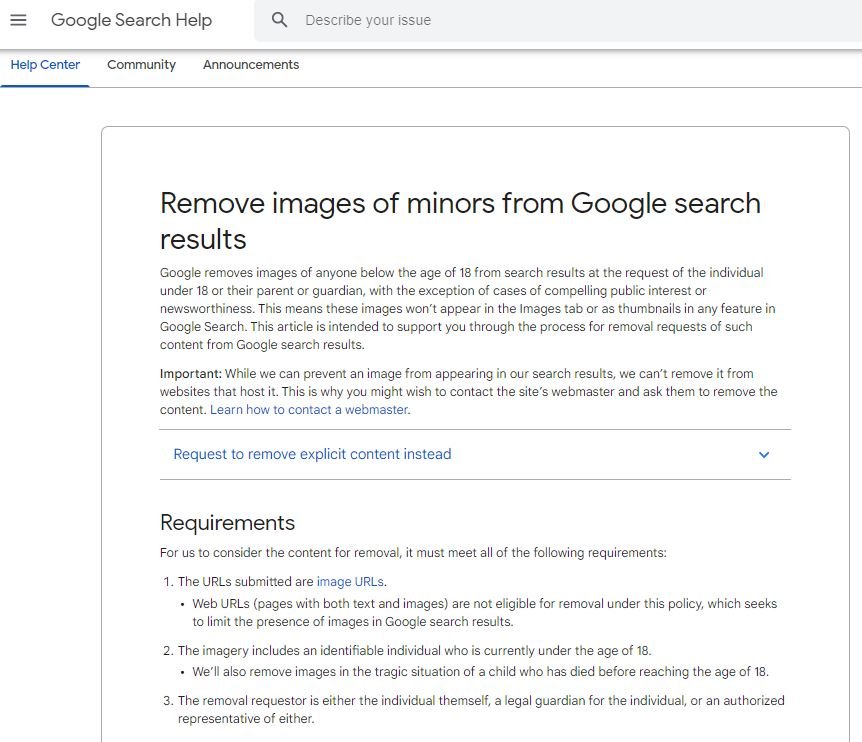
While Google considers this to be a good measure to strengthen the privacy of vulnerable users, the company specifies that requests will not proceed in cases of “public interest or informational value”, so we will have to wait to see how these criteria work in real scenarios.
In addition, the company specifies that applications will only be accepted from people who are currently under the age of eighteen, so anyone who passes this age limit will need to find another way to remove their image from the Internet. It is worth mentioning that, those over 18 years old will not be able to request the deletion of their photographs from years ago.
Users should keep in mind that deleting photos from search results does not mean removing them from the Internet, so Google advises users interested in this to contact the administrators of specific websites. However, if the appeal leads to nothing, removing images from Google search results will certainly be an important step.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
