A team of cybersecurity specialists from the firm Abnormal Security has detected a malicious campaign in which threat actors try to trick users with an alleged renewal of Microsoft Office; Thousands of users around the world are exposed to this attack, so you need to know the mode of operation.
Microsoft Office offers purchase and subscription plans, and collaborates with multiple companies to sell their products and services. Threat actor groups try to take advantage of this to deploy phishing campaigns by posing as company executives and stealing confidential victims’ information for various purposes.
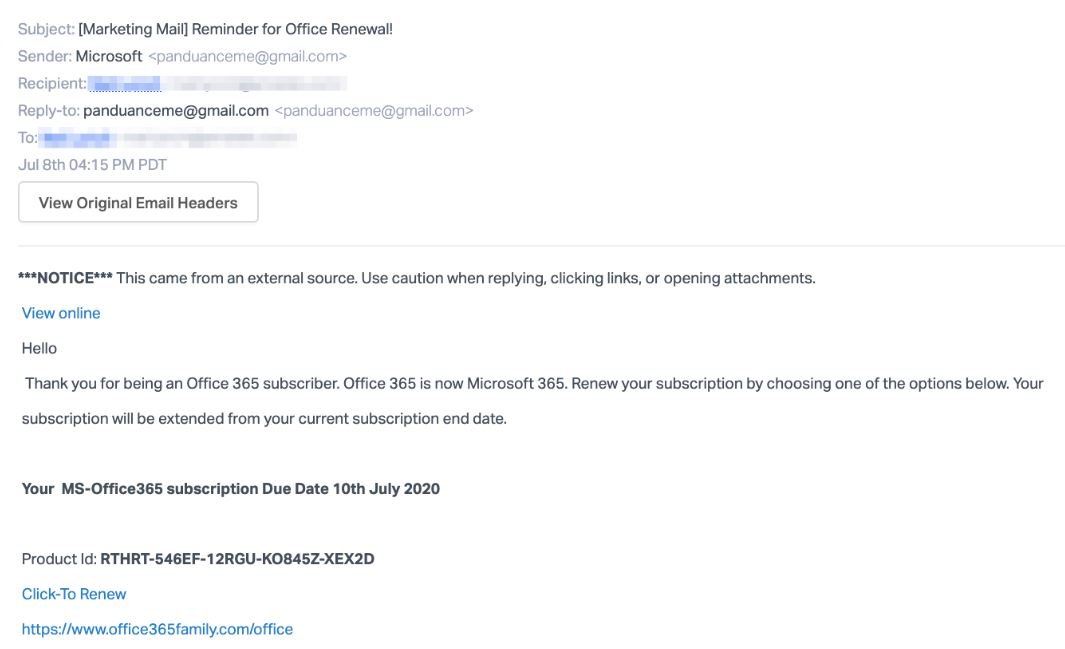
Threat actors send two emails purportedly from Microsoft inviting users to renew their Office subscription through links attached to the email text.
The attack is divided into two stages:
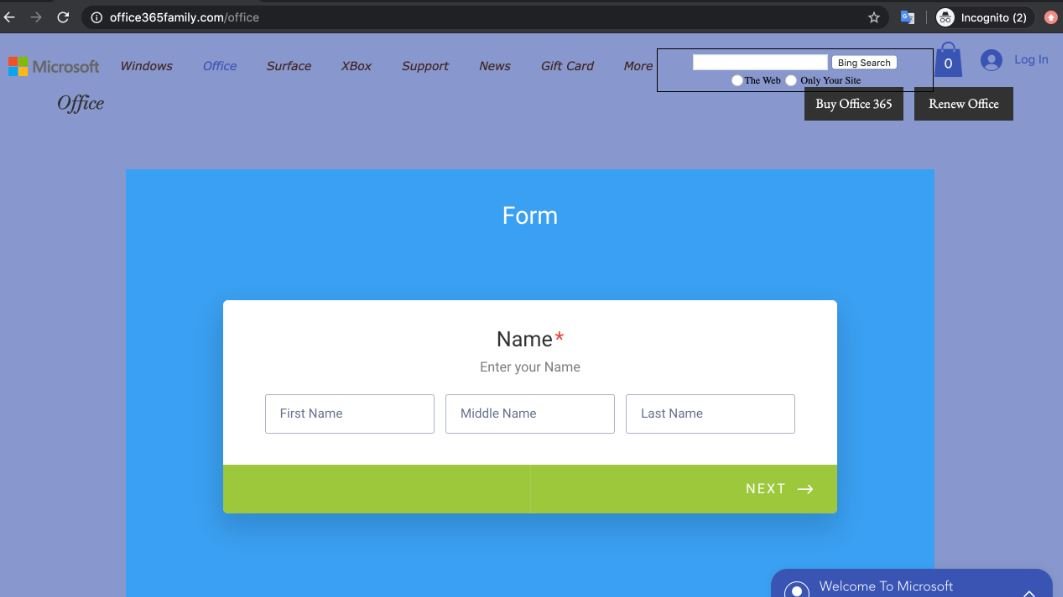
- The target user is redirected to a website hosted on Wix, which contains a confidential information registration form; the form asks for information such as address and payment card number
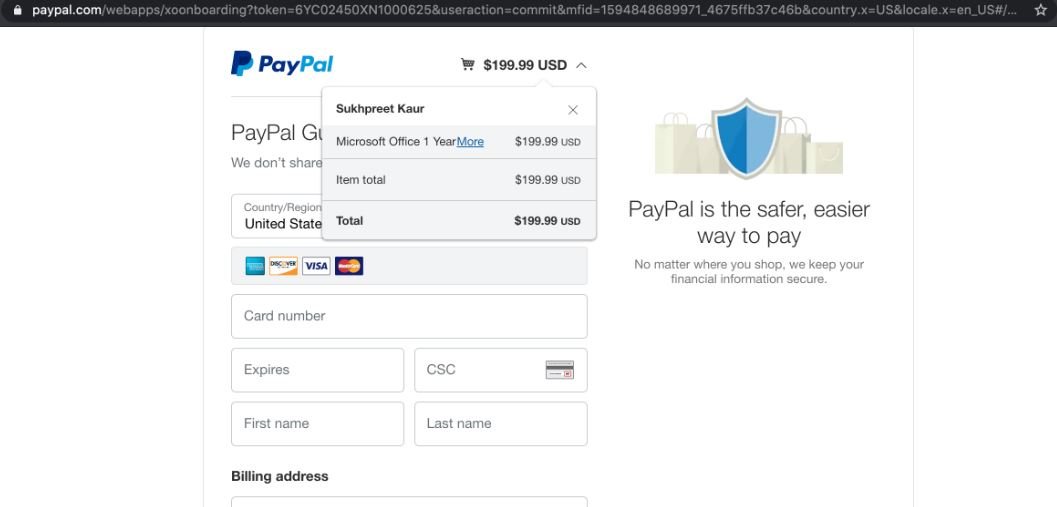
- Subsequently, the user is shown an alleged PayPal message. It is important to mention that although Microsoft accepts payments through PayPal, the payment option is included in the user’s Office account, not on the payment company’s site. Any payment to Microsoft made outside of the company’s official sites could be considered fraudulent
Victims of an attack could see your personal and financial information compromised, which would be useful in other stages of attack.
The email used by hackers is really compelling, as it employs multiple features typical of Microsoft’s legitimate notifications, which increases the chances of users falling into the trap.
In addition, it is necessary to consider Microsoft Office to be an essential service in virtually any business environment, so potential victims could more easily fall into deception. Finally, the researchers point out that the threat actors took the time to eye the malicious URLs, so it is not possible to distinguish the risk with only a small verification. If you receive this message or any other similar message, it is best to ignore it and notify your company’s information technology area, who will find the best way to contain th
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
